Software and Communications
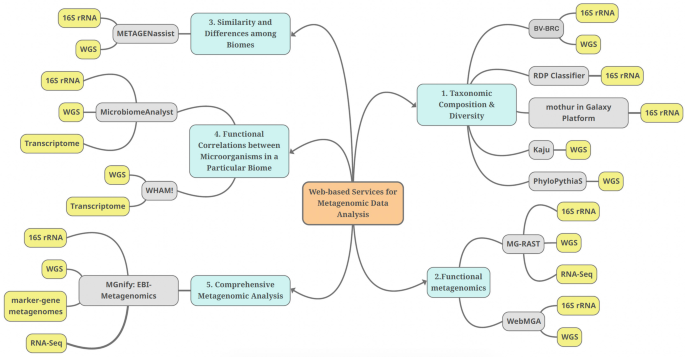
Interactive Web-Based Services for Metagenomic Data Analysis and Comparisons
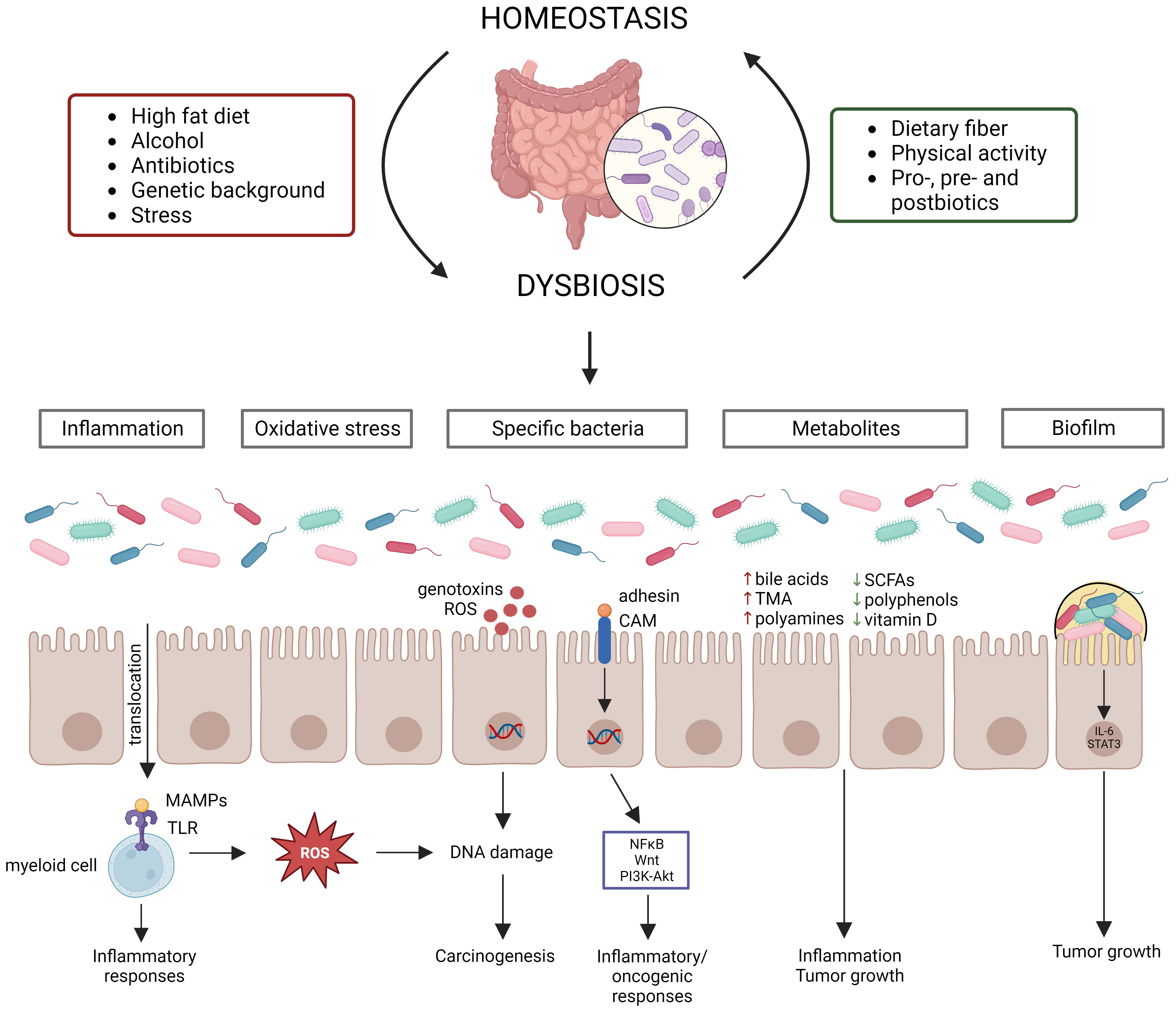
Recently, sequencing technologies have become readily available, and scientists are more motivated to conduct metagenomic research to unveil the potential of a myriad of ecosystems and biomes. Metagenomics studies the composition and functions of microbial communities and paves the way to multiple applications in medicine, industry, and ecology. Nonetheless, the immense amount of sequencing data of metagenomics research and the few user-friendly analysis tools and pipelines carry a new challenge to the data analysis. Web-based bioinformatics tools are now being developed to facilitate the

Sudden Fall Detection and Prediction Using AI Techniques
Fall prediction is a critical process in ensuring the safety and well-being of individuals, particularly the elderly population. This paper focuses on the development of a fall detection and prediction system using wearable sensors and machine learning algorithms. The system issues an alarm upon predicting the occurrence of falling and sends alerts to a monitoring centre for timely assistance. Wearable sensor devices, including Inertial Measurement Units (IMUs) equipped with accelerometers, gyroscopes, and magnetometers are utilized for data collection. UPFALL, a comprehensive online freely
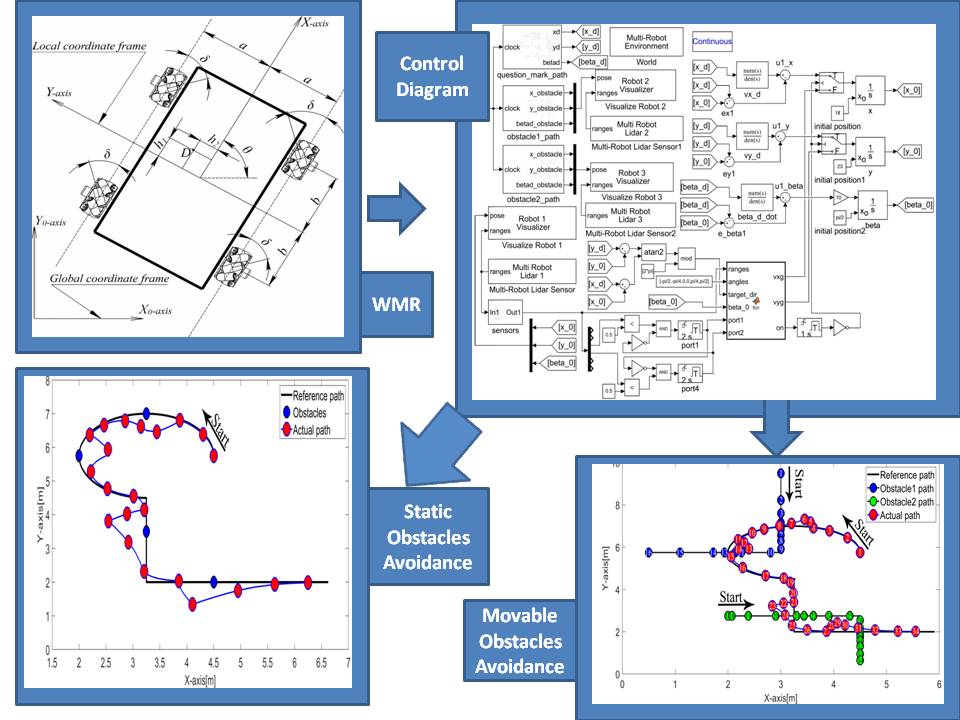
The Implementation of Fuzzy logic controller for the obstacle avoidance in 3 Mecanum-wheeled Robot
mobile robots play an enormous role in different fields of daily life applications including military, safety, and logistic multi-tasking capabilities. A new approach is introduced to the market which is the 3 Mecanum wheeled mobile robot (3-MWMR) is being tested and validated. The main goal of the proposed design is to achieve all the desired directions of motion and to improve the performance of the mobile robot in avoiding obstacles using the fuzzy logic controller. © 2022 IEEE.
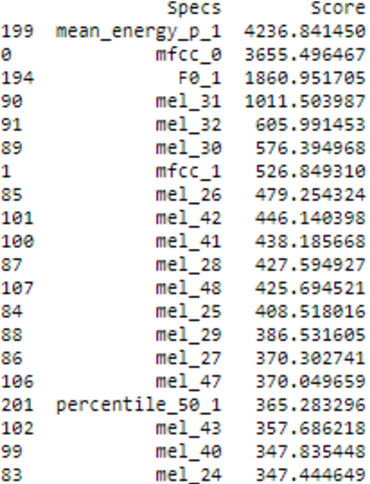
Arabic English Speech Emotion Recognition System
The Speech Emotion Recognition (SER) system is an approach to identify individuals' emotions. This is important for human-machine interface applications and for the emerging Metaverse. This work presents a bilingual Arabic-English speech emotion recognition system based on EYASE and RAVDESS datasets. A novel feature set was composed by using spectral and prosodic parameters to obtain high performance at a low computational cost. Different classification models were applied. These machine learning classifiers are Random Forest, Support Vector Machine, Logistic Regression, Multi-Layer Perceptron
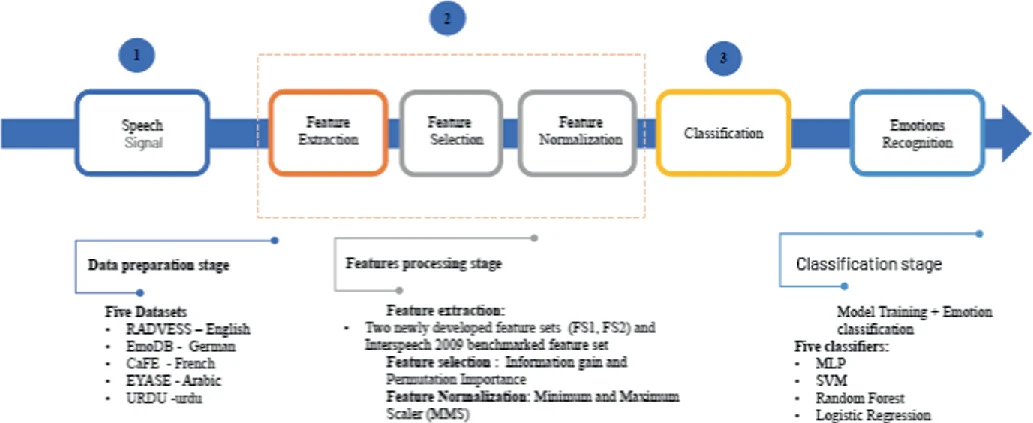
Emotion Recognition System for Arabic Speech: Case Study Egyptian Accent
Speech Emotion Recognition (SER) systems are widely regarded as essential human-computer interface applications. Extracting emotional content from voice signals enhances the communication between humans and machines. Despite the rapid advancement of Speech Emotion Recognition systems for several languages, there is still a gap in SER research for the Arabic language. The goal of this research is to build an Arabic-based SER system using a feature set that has both high performance and low computational cost. Two novel feature sets were created using a mix of spectral and prosodic features
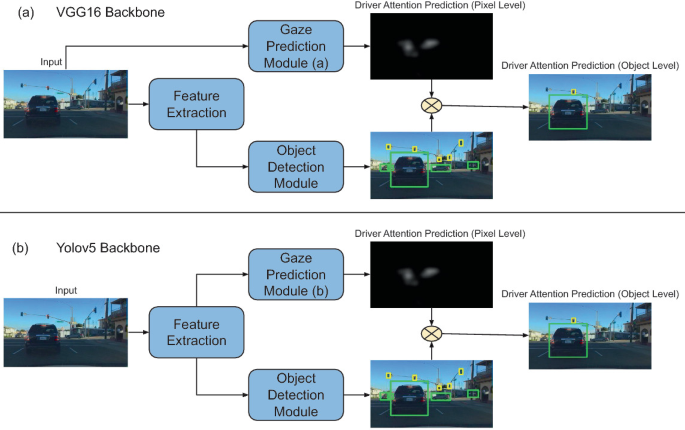
DAP: A Framework for Driver Attention Prediction
Human drivers employ their attentional systems during driving to focus on critical items and make judgments. Because gaze data can indicate human attention, collecting and analyzing gaze data has emerged in recent years to improve autonomous driving technologies. In safety-critical situations, it is important to predict not only where the driver focuses his attention but also on which objects. In this work, we propose DAP, a novel framework for driver attention prediction that bridges the attention prediction gap between pixels and objects. The DAP Framework is evaluated on the Berkeley
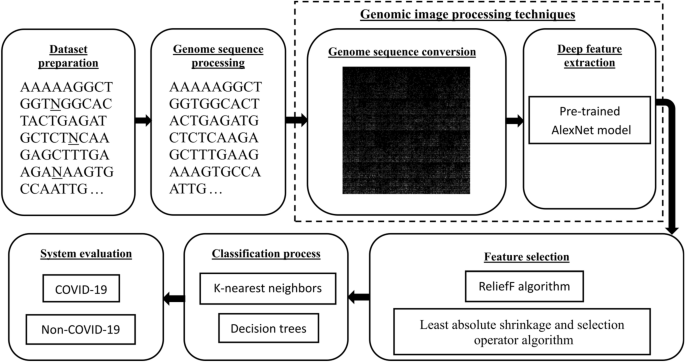
A hybrid deep learning approach for COVID-19 detection based on genomic image processing techniques
The coronavirus disease 2019 (COVID-19) pandemic has been spreading quickly, threatening the public health system. Consequently, positive COVID-19 cases must be rapidly detected and treated. Automatic detection systems are essential for controlling the COVID-19 pandemic. Molecular techniques and medical imaging scans are among the most effective approaches for detecting COVID-19. Although these approaches are crucial for controlling the COVID-19 pandemic, they have certain limitations. This study proposes an effective hybrid approach based on genomic image processing (GIP) techniques to
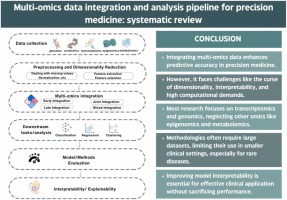
Multi-omics data integration and analysis pipeline for precision medicine: Systematic review
Precision medicine has gained considerable popularity since the “one-size-fits-all” approach did not seem very effective or reflective of the complexity of the human body. Subsequently, since single-omics does not reflect the complexity of the human body's inner workings, it did not result in the expected advancement in the medical field. Therefore, the multi-omics approach has emerged. The multi-omics approach involves integrating data from different omics technologies, such as DNA sequencing, RNA sequencing, mass spectrometry, and others, using computational methods and then analyzing the
Genomic image representation of human coronavirus sequences for COVID-19 detection
Coronavirus (CoV) disease 2019 (COVID-19) is a severe pandemic affecting millions worldwide. Due to its rapid evolution, researchers have been working on developing diagnostic approaches to suppress its spread. This study presents an effective automated approach based on genomic image processing (GIP) techniques to rapidly detect COVID-19, among other human CoV diseases, with high acceptable accuracy. The GIP technique was applied as follows: first, genomic graphical mapping techniques were used to convert the genome sequences into genomic grayscale images. The frequency chaos game