
Software and Communications
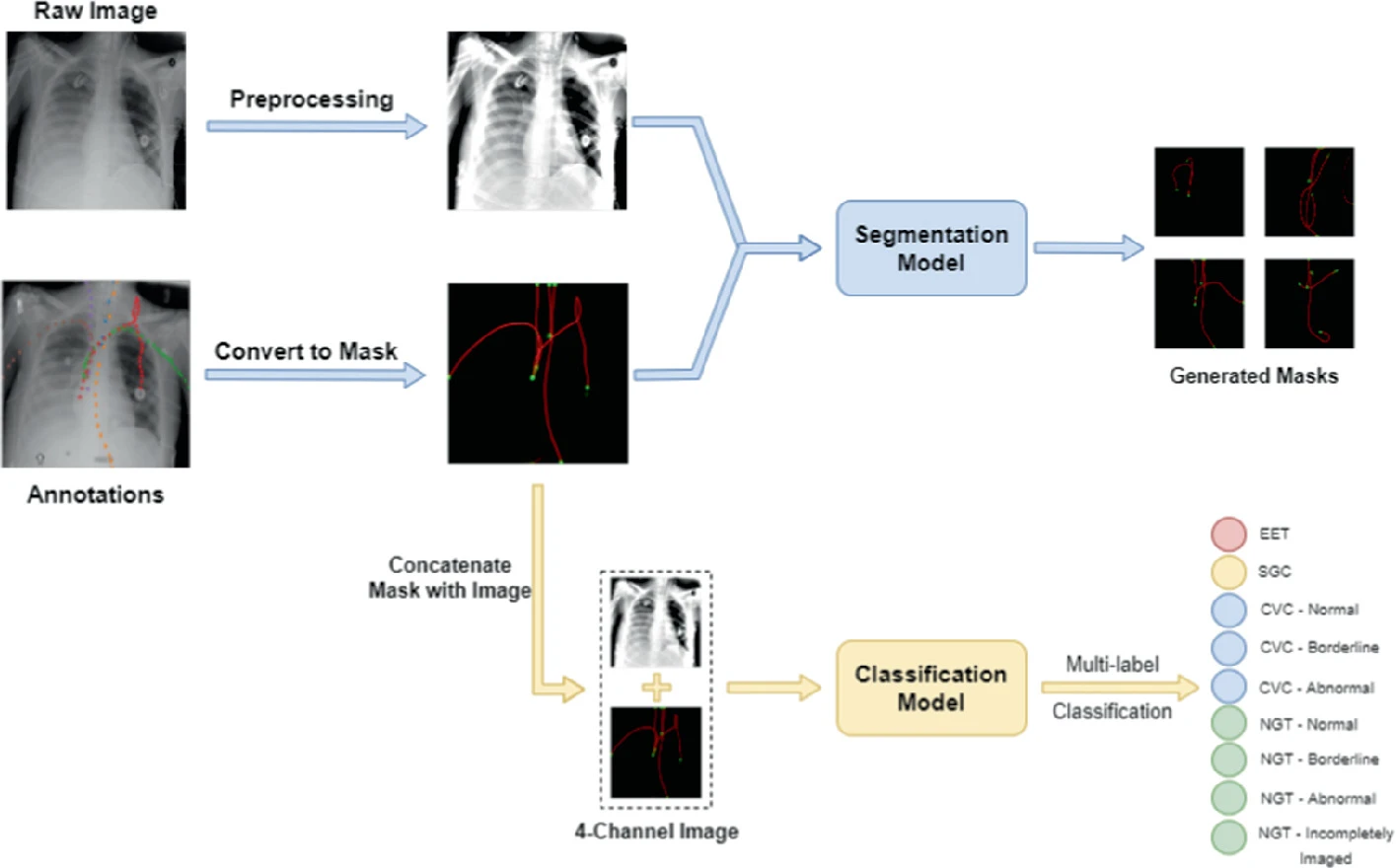
Efficient Pipeline for Rapid Detection of Catheters and Tubes in Chest Radiographs
Catheters are life support devices. Human expertise is often required for the analysis of X-rays in order to achieve the best positioning without misplacement complications. Many hospitals in underprivileged regions around the world lack the sufficient radiology expertise to frequently process X-rays for patients with catheters and tubes. This deficiency may lead to infections, thrombosis, and bleeding due to misplacement of catheters. In the last 2 decades, deep learning has provided solutions to various problems including medical imaging challenges. So instead of depending solely on
Oral Dental Diagnosis Using Deep Learning Techniques: A Review
The purpose of this study is to investigate the gradual incorporation of deep learning in the dental healthcare system, offering an easy and efficient diagnosis. For that, an electronic search was conducted in the Institute of Electrical and Electronics Engineers (IEEE) Xplore, ScienceDirect, Journal of Dentistry, Health Informatics Journal, and other credible resources. The studies varied with their tools and techniques used for the diagnosis while coping with the rapid deep-learning evolving base, with different types of conducting tools and analysis for the data. An inclusion criterion was
ArabicQuest: Enhancing Arabic Visual Question Answering with LLM Fine-Tuning
In an attempt to bridge the semantic gap between language understanding and visuals, Visual Question Answering (VQA) offers a challenging intersection of computer vision and natural language processing. Large Language Models (LLMs) have shown remarkable ability in natural language understanding; however, their use in VQA, particularly for Arabic, is still largely unexplored. This study aims to bridge this gap by examining how well LLMs can improve VQA models. We use state-of-the-art AI algorithms on datasets from multiple fields, including electric devices, Visual Genome, RSVQA, and ChartsQA
Towards Arabic Image Captioning: A Transformer-Based Approach
The automatic generation of textual descriptions from images, known as image captioning, holds significant importance in various applications. Image captioning applications include accessibility for the visually impaired, social media enhancement, automatic image description for search engines, assistive technology for education, and many more. While extensive research has been conducted in English, exploring this challenge in Arabic remains limited due to its complexity. Arabic is one of the world's most widely spoken languages. Around 420 million native people speak this language. It is also
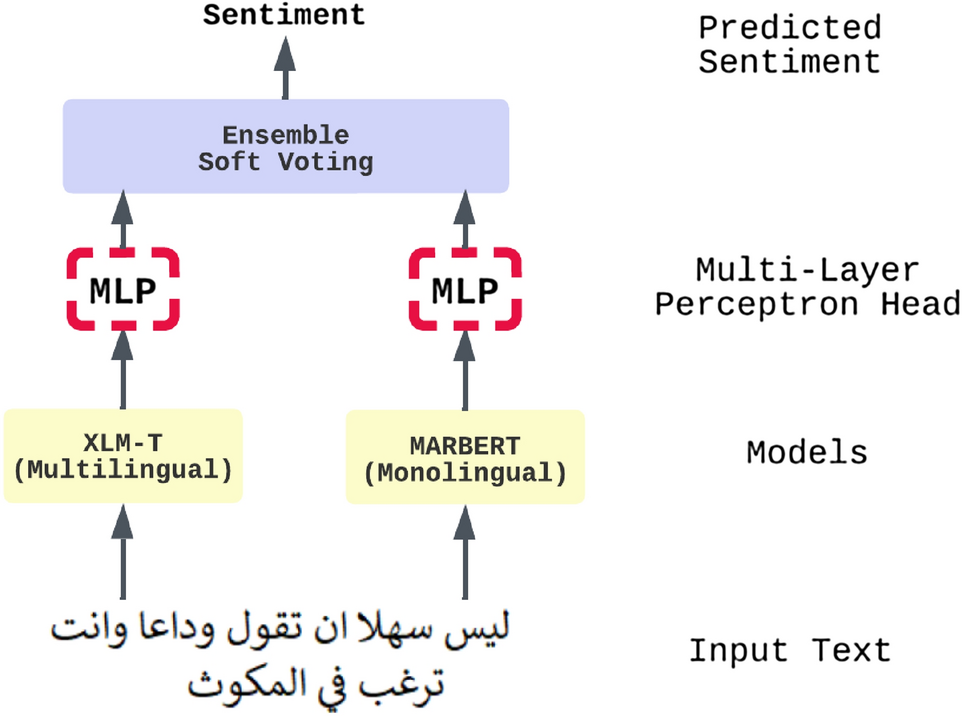
An ensemble transformer-based model for Arabic sentiment analysis
Sentiment analysis is a common and challenging task in natural language processing (NLP). It is a widely studied area of research; it facilitates capturing public opinions about a topic, product, or service. There is much research that tackles English sentiment analysis. However, the research in the Arabic language is behind other high-resource languages. Recently, models such as bidirectional encoder representations from transformers (BERT) and generative pre-trained transformer (GPT) have been widely used in many NLP tasks; it significantly improved performance in NLP tasks, especially

Generalisability of fetal ultrasound deep learning models to low-resource imaging settings in five African countries
Most artificial intelligence (AI) research and innovations have concentrated in high-income countries, where imaging data, IT infrastructures and clinical expertise are plentiful. However, slower progress has been made in limited-resource environments where medical imaging is needed. For example, in Sub-Saharan Africa, the rate of perinatal mortality is very high due to limited access to antenatal screening. In these countries, AI models could be implemented to help clinicians acquire fetal ultrasound planes for the diagnosis of fetal abnormalities. So far, deep learning models have been

ArFakeDetect: A Deep Learning Approach for Detecting Fabricated Arabic Tweets on COVID-19 Vaccines
Social media platforms have emerged as major sources of false information, particularly regarding health topics. like COVID-19 vaccines. This rampant dissemination of inaccurate content contributes significantly to vaccine hesitancy and undermines vaccination campaigns. This research addresses the pressing need for automated methods to distinguish between factual and fabricated Arabic tweets concerning vaccines, aiming to mitigate the spread of misinformation on these platforms. The proposed approach utilizes deep learning techniques, leveraging pre-trained Arabic language models (Arabert)
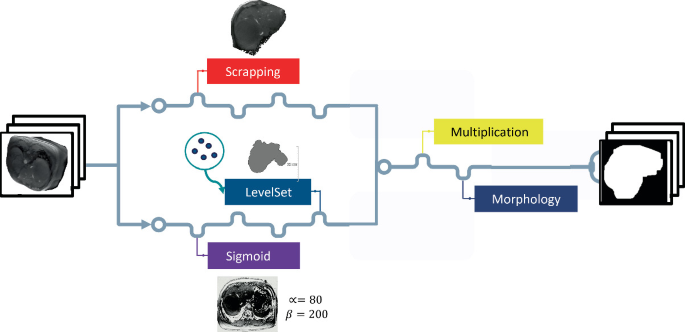
Iterative Refinement Algorithm for Liver Segmentation Ground-Truth Generation Using Fine-Tuning Weak Labels for CT and Structural MRI
Medical image segmentation is indicated in a number of treatments and procedures, such as detecting pathological changes and organ resection. However, it is a time-consuming process when done manually. Automatic segmentation algorithms like deep learning methods overcome this hurdle, but they are data-hungry and require expert ground-truth annotations, which is a limitation, particularly in medical datasets. On the other hand, unannotated medical datasets are easier to come by and can be used in several methods to learn ground-truth masks. In this paper, we aim to utilize across-modalities

Cross-Modality Deep Transfer Learning: Application to Liver Segmentation in CT and MRI
Liver diseases cause up to two million deaths yearly. Their diagnosis and treatment plans require an accurate assessment of the liver structure and tissue characteristics. Imaging modalities such as computed tomography (CT) and Magnetic resonance (MR) can be used to assess the liver. CT has better spatial resolution compared to MR, which has better tissue contrast. Each modality has its own applications. However, CT is widely used due its ease of access, lower cost and a shorter examination time. Liver segmentation is an important step that helps to accurately identify and isolate the liver
On The Arabic Dialects' Identification: Overcoming Challenges of Geographical Similarities Between Arabic dialects and Imbalanced Datasets
Arabic is one of the world's richest languages, with a diverse range of dialects based on geographical origin. In this paper, we present a solution to tackle subtask 1 (Country-level dialect identification) of the Nuanced Arabic Dialect Identification (NADI) shared task 2022 achieving third place with an average macro F1 score between the two test sets of 26.44%. In the preprocessing stage, we removed the most common frequent terms from all sentences across all dialects, and in the modeling step, we employed a hybrid loss function approach that includes Weighted cross entropy loss and Vector