
Software and Communications
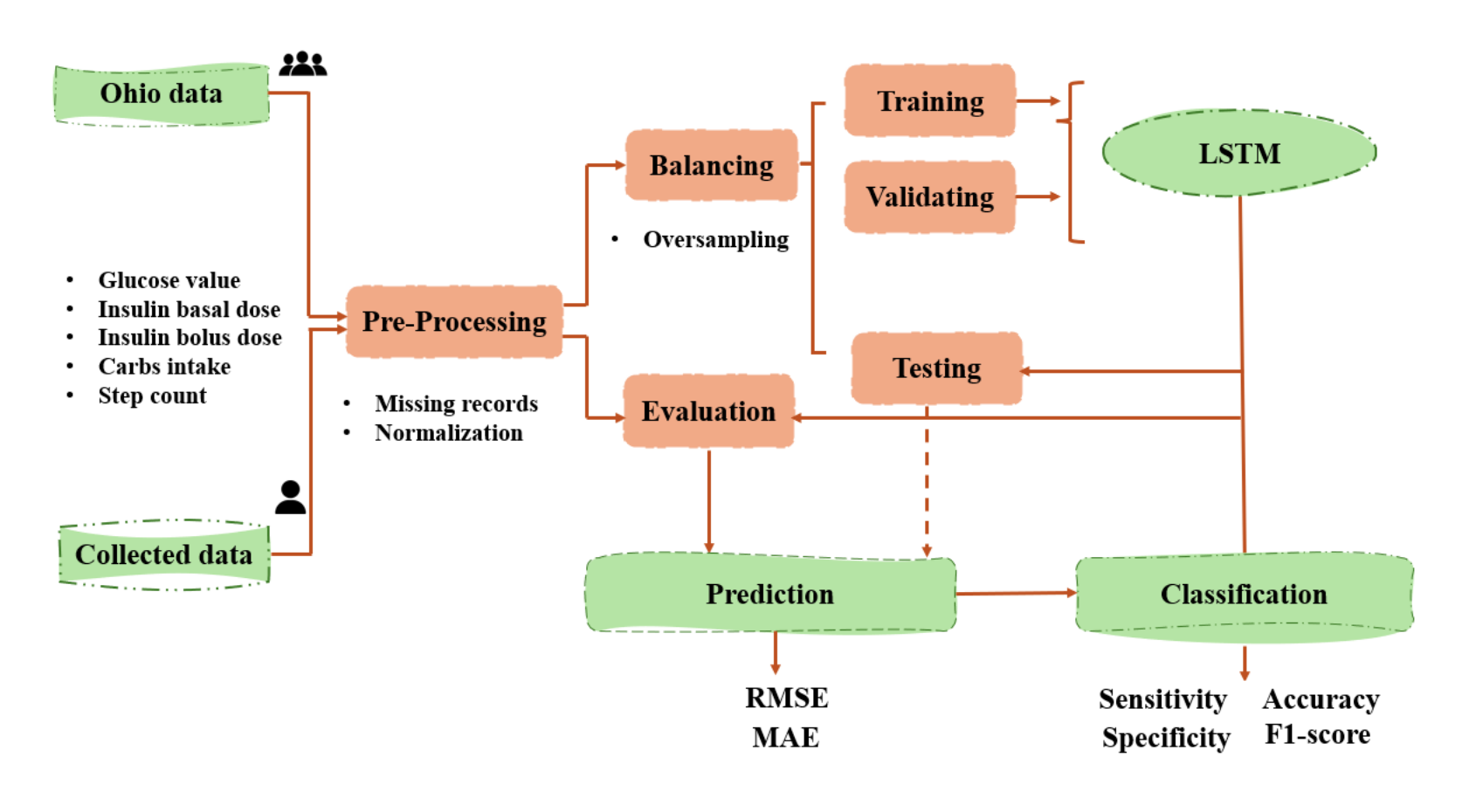
Intelligent Real-Time Hypoglycemia Prediction for Type 1 Diabetes
Hypoglycemia in Type 1 Diabetes (T1D) refers to a condition where blood glucose (BG) levels drop to abnormally low levels, typically below 70 mg/dL. This can occur when there is an excessive amount of insulin relative to the blood glucose level, leading to an imbalance that can be dangerous and potentially life-threatening if not promptly treated. The availability of large amounts of data from continuous glucose monitoring (CGM), insulin doses, carbohydrate intake, and additional vital signs, together with deep learning (DL) techniques, has revolutionized algorithmic approaches for BG
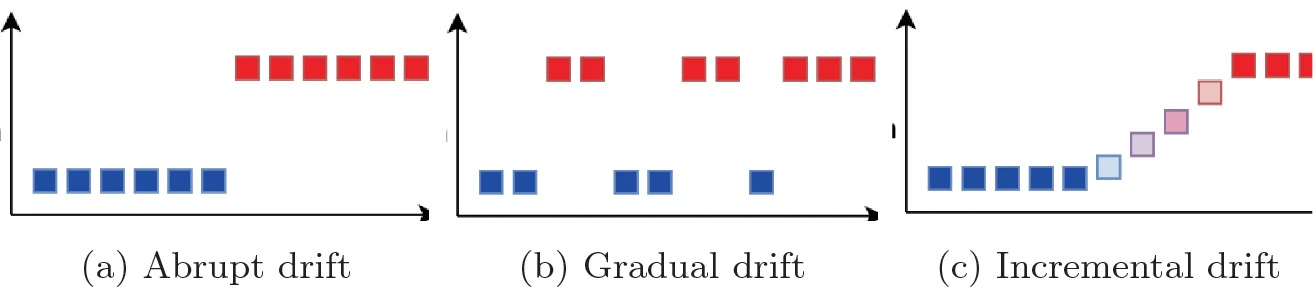
Benchmarking Concept Drift Detectors for Online Machine Learning
Concept drift detection is an essential step to maintain the accuracy of online machine learning. The main task is to detect changes in data distribution that might cause changes in the decision boundaries for a classification algorithm. Upon drift detection, the classification algorithm may reset its model or concurrently grow a new learning model. Over the past fifteen years, several drift detection methods have been proposed. Most of these methods have been implemented within the Massive Online Analysis (MOA). Moreover, a couple of studies have compared the drift detectors. However, such
Optimizing truss members using Machine Learning
This paper aims to produce an optimization methodology for a truss for minimal stress on critical sections using Machine learning models. This is done by varying the height and length of the truss span and applying live loads on different joints. The optimization of the truss is done through feed forward with back propagation artificial neural network model, The optimized truss is modelled and analysed using finite element and stiffness software. The paper presents the results and identifies the best dimensions for the truss design with a safety factor. © The Authors.
Decision Analysis for the Influence of Incorporating Waste Materials on Green Concrete Properties
Concrete industry is challenged by sustainability and technical concerns. Sustainability includes minimization of raw material usage, energy consumption, and emission of greenhouse gases, while technical concerns comprise the enhancement of mechanical properties and durability such as compressive strength, resistance to chloride, acids, and elevated temperatures. Therefore, recycling of industrial waste in manufacturing of green concrete has become a robust viable alternative to disposal, due to the limited natural resources and raw materials which contribute to sustainable construction

Penetration Testing: A Cost-Benefit Analysis of Best Practices Implementation for Software Startups
Despite software startups often not handlingsensitive data, the implementation of robust security measures is crucial to mitigate significant financial and reputational risks. This study investigates the cost-benefit analysis of implementing best practices in penetration testing (Pentest) versus notimplementing them, using Roboost as a case study. It emphasizes that proactive security investments not only protect current assets but also prepare organizations for future growthThe research employs a mixed-methods approach, combining quantitative analysis of financial data with qualitative
Prediction model for the compressive strength of green concrete using cement kiln dust and fly ash
Integrating artificial intelligence and green concrete in the construction industry is a challenge that can help to move towards sustainable construction. Therefore, this research aims to predict the compressive strength of green concrete that includes a ratio of cement kiln dust (CKD) and fly ash (FA), then recommend the optimum sustainable mixture design. The artificial neural network (ANN) and multiple linear regression techniques are used to build prediction models and statistics using MATLAB and IBM SPSS software. The input parameters are based on 156 data points of concrete components
Optimizing the coagulation/flocculation process for the treatment of slaughterhouse and meat processing wastewater: experimental studies and pilot-scale proposal
The slaughterhouse industry generates substantial wastewater rich in proteins, lipids, fibers, and carbohydrates. This study integrates experimental investigations into artificial neural network (ANN) optimization and commerce design studies for treating slaughterhouse and meat processing wastewater (SMW). Batch coagulation/flocculation experiments identified optimal conditions for three coagulants: Ferric Chloride (FeCl3·6H2O), Poly Aluminum Chloride (PAC), and Aluminum Sulfate Al2(SO4)3, aiming for optimum removal of chemical oxygen demand (COD), total suspended solids (TSS), and total
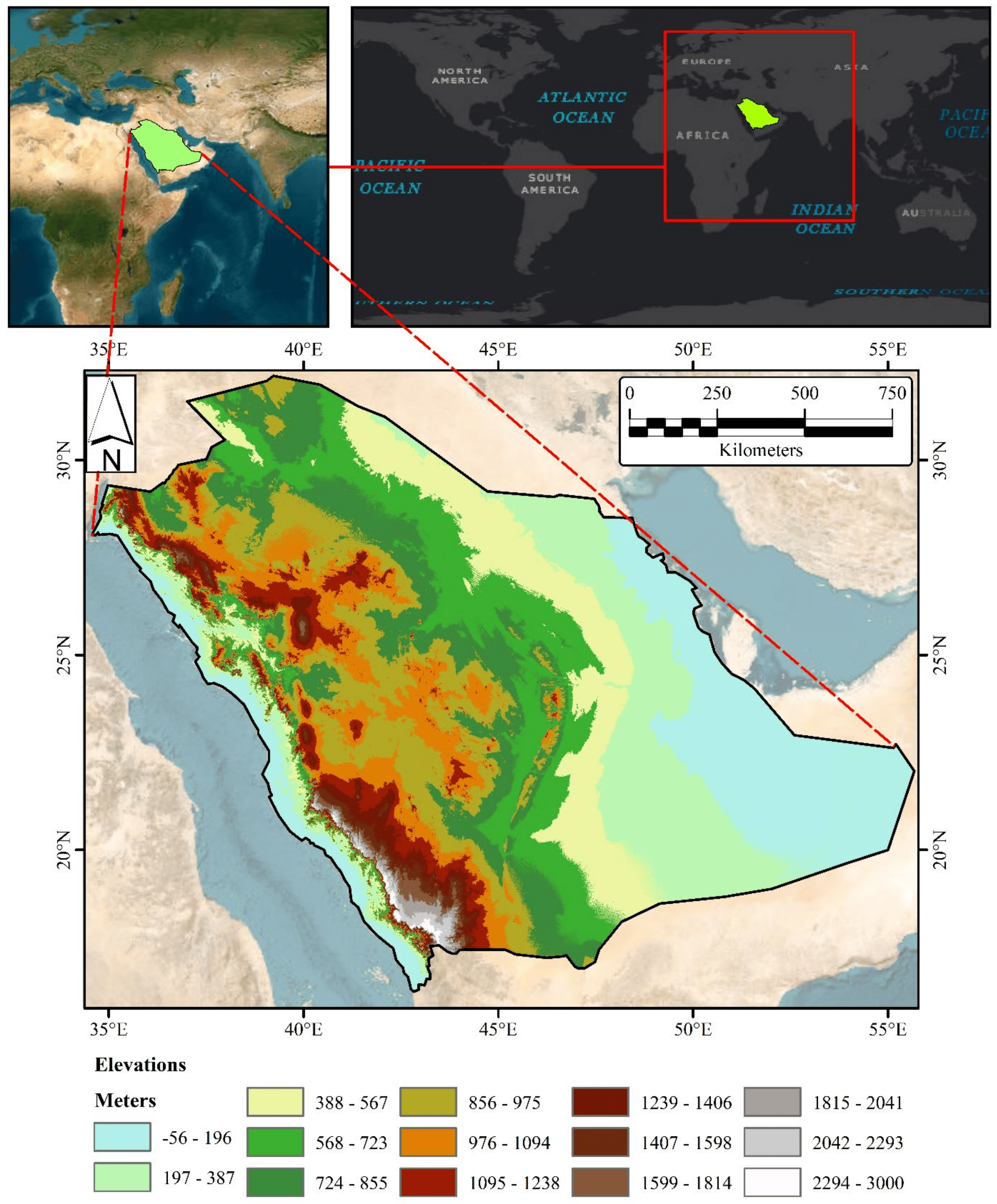
Evaluation of Geospatial Interpolation Techniques for Enhancing Spatiotemporal Rainfall Distribution and Filling Data Gaps in Asir Region, Saudi Arabia
Providing an accurate spatiotemporal distribution of rainfall and filling data gaps are pivotal for effective water resource management. This study focuses on the Asir region in the southwest of Saudi Arabia. Given the limited accuracy of satellite data in this arid/mountain-dominated study area, geospatial interpolation has emerged as a viable alternative approach for filling terrestrial records data gaps. Furthermore, the irregularity in rain gauge data and the yearly spatial variation in data gaps hinder the creation of a coherent distribution pattern. To address this, the Centered Root
Impact assessment of implementing virtual reality in the Egyptian construction industry
Construction projects in Egypt are becoming more complex as the need for mega projects increases to meet the Egyptian 2030 vision. Meanwhile, the advancement of Virtual Reality technologies is apparent in the 21st century. This paper aims to assess the impact of implementing virtual reality in the Egyptian construction industry. An application using Fuzor VDC and Oculus Quest 2 has been developed elaborating the technology's use. The application includes 4D simulation and meetings in virtual reality. Furthermore, a survey is conducted to measure the impact of implementation on key project
LRFD for Shallow Foundations Using Plate Load Test Data
In this study, a database was developed to house reliable results from 43-plate load tests conducted on different types of compacted soil, including load-displacement responses and other information about soil and testing conditions. Using information from that database, resistance factors were developed for shallow foundations based on the prevalent first order second moment reliability approach. The resistance factors were calculated for common equations used to calculating the soil bearing capacity such as Terzaghi, Meyerhof, and Hansen. The calibration was based on comparing the calculated