
Software and Communications
Clay chips and beads capture in situ barley root microbiota and facilitate in vitro long-term preservation of microbial strains
Capturing the diverse microbiota from healthy and/or stress resilient plants for further preservation and transfer to unproductive and pathogen overloaded soils, might be a tool to restore disturbed plant-microbe interactions. Here, we introduce Aswan Pink Clay as a low-cost technology for capturing and storing the living root microbiota. Clay chips were incorporated into the growth milieu of barley plants and developed under gnotobiotic conditions, to capture and host the rhizospheric microbiota. Afterward, it was tested by both a culture-independent (16S rRNA gene metabarcoding) and
Automated Detection and Consistency Analysis of Tajweed Recitation Rules in the Holy Quran
Precise Recitation of Holy Quran is a religious duty that must be performed with great care. Tajweed rules are constructed to guide the reader to utter the Holy Quran text as it was originally uttered by prophet Muhammad. An automatic pattern detection algorithm is implemented to allocate basic Tajweed rules. The rules addressed in this paper, are Madd, Noon Sakinah, Tanween and Meem Sakinah rules. These rules are characterized by well-defined uttered style. The rules studied in this paper, were allocated at 487 positions in forty verses of Surat El-Anfal of Sheikh El-Hosary's recitation. Data

Harris Hawks Feature Optimization for Identifying the Informative Pathogens of Pediatric Sepsis
One of the most fatal potentially life-threatening medical condition that increases the mortality in pediatric populations is pediatric sepsis. Unfortunately, the improper control of such disease can lead to tissue damage and organ dysfunction because of the overwhelming the human body's response to an infection. Therefore, early recognition and intervention can clearly improve outcome for infants and children with conditions that lead to sepsis before the admission to the intensive care unit (ICU). Accordingly, 17 informative differential expressed genes have been selected using a nature
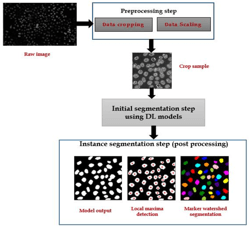
A comparative study for nuclei segmentation using latest deep learning optimizers
Nuclei segmentation is a critical task in biological image analysis, with numerous applications in cancer diagnosis, grading, staging, and treatment planning. However, this task is challenging, particularly when dealing with low-resolution and low signal-to-noise ratio microscopy images. Segmentation problems arise, such as touching and missing cells, which make the process even more challenging. Deep learning models, including Attention U-Net and TransUNet, have demonstrated exceptional performance in medical image segmentation. Nonetheless, the choice of optimizer can significantly impact
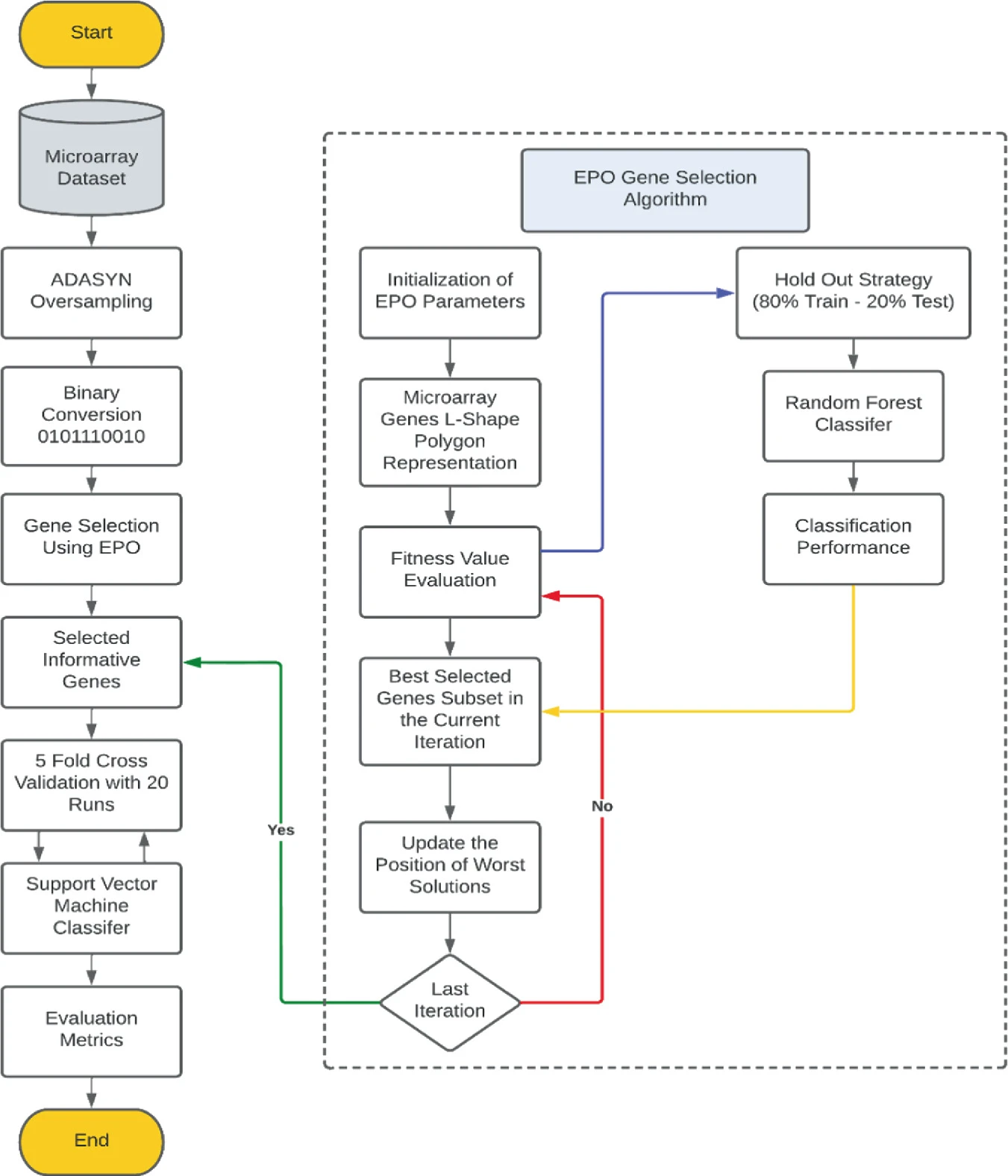
Computational Microarray Gene Selection Model Using Metaheuristic Optimization Algorithm for Imbalanced Microarrays Based on Bagging and Boosting Techniques
Genomic microarray databases encompass complex high dimensional gene expression samples. Imbalanced microarray datasets refer to uneven distribution of genomic samples among different contributed classes which can negatively affect the classification performance. Therefore, gene selection from imbalanced microarray dataset can give rise to misleading, and inconsistent nominated genes that would alter the classification performance. Such unsatisfactory classification performance is due to the skewed distribution of the samples across the microarrays toward the majority class. In this paper, we
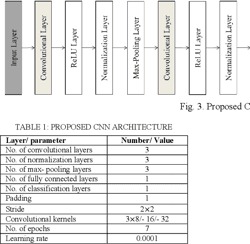
Classification of Autism Spectrum Disorder using Convolutional Neural Networks from Neuroimaging Data
Current Autism Spectrum Disorder (ASD) diagnosis methods exhibit some limitations as they are based on clinical interviews and observations of behaviors, characteristics, and abilities. Moreover, considering the current challenges in identifying the causes and mechanisms associated with ASD, there is an essential need for automated techniques capable of providing an accurate classification between ASD and typically developed (TD). In this paper, we present a convolutional neural network model that can differentiate ASD from TD. This proposed system is trained and validated on the well-known
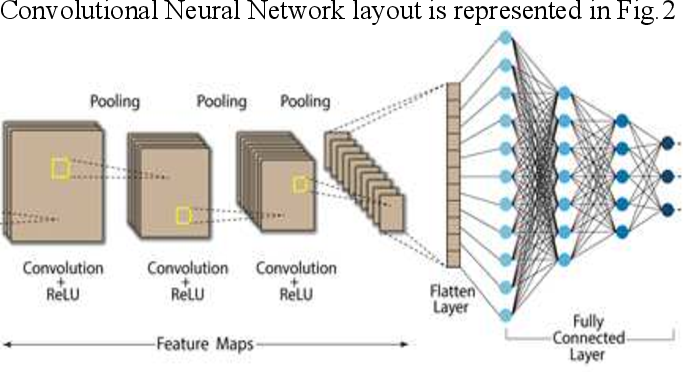
Automatic Detection of Some Tajweed Rules
correct understanding of the Holy Quran is an essential duty for all Muslims. Tajweed rules guide the reciter to perform Holy Quran reading exactly as it was uttered by Prophet Muhammad peace be upon him. This work focused on the recognition of one Quranic recitation rule. Qalqalah rule is applied to five letters of the Arabic Alphabet (Baa/Daal/Jeem/Qaaf/Taa) having sukun vowelization. The proposed system used the Mel Frequency Cepstral Coefficients (MFCC) as the feature extraction technique, and the Convolutional Neural Networks (CNN) model was used for recognition. The available dataset
Downlink Throughput Prediction in LTE Cellular Networks Using Time Series Forecasting
Long-Term Evolution (LTE) cellular networks have transformed the mobile business, as users increasingly require various network services such as video streaming, online gaming, and video conferencing. A network planning approach is required for network services to meet user expectations and meet their needs. The User DownLink (UE DL) throughput is considered the most effective Key Performance Indicator (KPI) for measuring the user experience. As a result, the forecast of UE DL throughput is essential in network dimensioning for the network planning team throughout the network design stage. The

Differentiation Between Normal and Abnormal Functional Brain Connectivity Using Non-directed Model-Based Approach
Brain Connectivity refers to networks of functional and anatomical connections found throughout the brain. Multiple neural populations are connected by intricate connectivity circuits and interact with one another to exchange information, synchronize their activity, and participate in the accomplishment of complex cognitive tasks. Issues about how various brain regions contribute to cognition and their reciprocal roles have drawn the attention of researchers since the beginning of neuroscience. The interest in brain connection estimation has grown significantly due to the advancement of
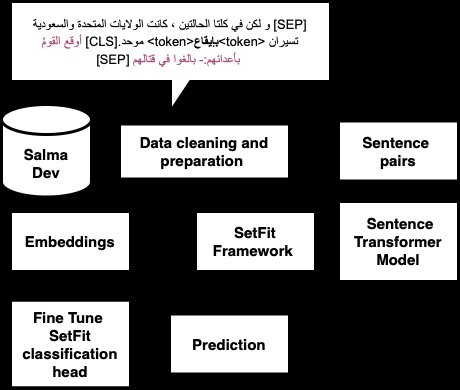
Pirates at ArabicNLU2024: Enhancing Arabic Word Sense Disambiguation using Transformer-Based Approaches
This paper presents a novel approach to Arabic Word Sense Disambiguation (WSD) leveraging transformer-based models to tackle the complexities of the Arabic language. Utilizing the SALMA dataset, we applied several techniques, including Sentence Transformers with Siamese networks and the SetFit framework optimized for few-shot learning. Our experiments, structured around a robust evaluation framework, achieved a promising F1-score of up to 71%, securing second place in the ArabicNLU 2024: The First Arabic Natural Language Understanding Shared Task competition. These results demonstrate the