
Software and Communications
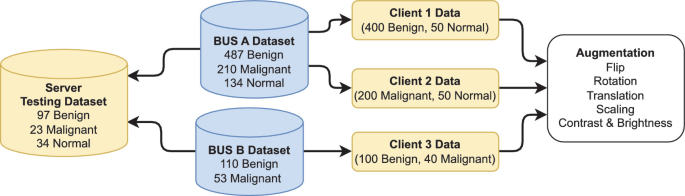
A Novel Approach to Breast Cancer Segmentation Using U-Net Model with Attention Mechanisms and FedProx
Breast cancer is a leading cause of death among women worldwide, emphasizing the need for early detection and accurate diagnosis. As such Ultrasound Imaging, a reliable and cost-effective tool, is used for this purpose, however the sensitive nature of medical data makes it challenging to develop accurate and private artificial intelligence models. A solution is Federated Learning as it is a promising technique for distributed machine learning on sensitive medical data while preserving patient privacy. However, training on non-Independent and non-Identically Distributed (non-IID) local datasets
From Gestures to Audio: A Dataset Building Approach for Egyptian Sign Language Translation to Arabic Speech
The communication barriers faced by people with disabilities, particularly the deaf or hard of hearing, nonverbal, deaf-mute, and blind have a significant impact on their quality of life and social inclusion. Our research aims to provide real-time translation from sign language to speech and vice versa. The ability to provide real-time speech-to-text and text-to-sign language translation will help alleviate these barriers, improve communication, and increase social inclusivity for this community ensuring they are not left out in conversations and social interactions. A significant amount of
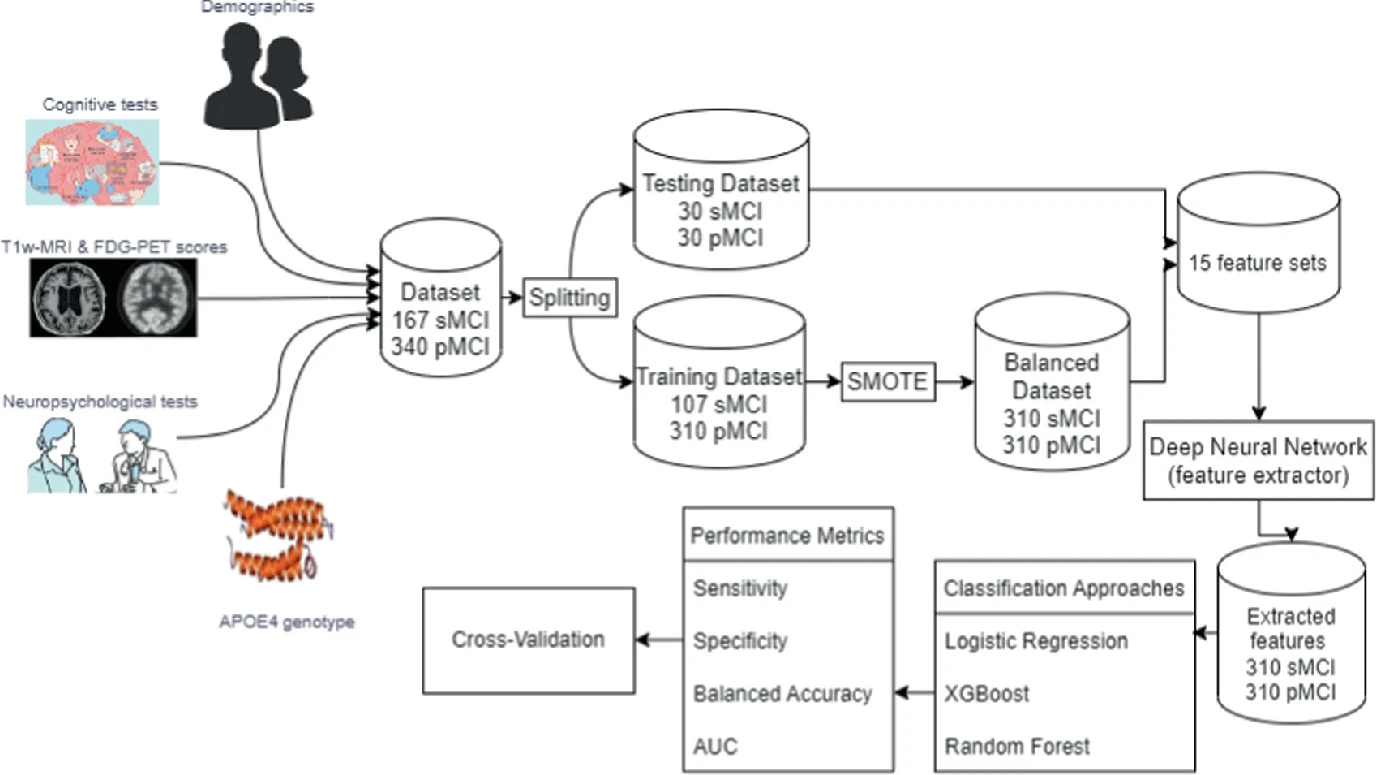
A Novel Diagnostic Model for Early Detection of Alzheimer’s Disease Based on Clinical and Neuroimaging Features
Alzheimer’s Disease (AD) is a dangerous disease that is known for its characteristics of eroding memory and destroying the brain. The classification of Alzheimer's disease is an important topic that has recently been addressed by many studies using Machine Learning (ML) and Deep Learning (DL) methods. Most research papers tackling early diagnosis of AD use these methods as a feature extractor for neuroimaging data. In our research paper, the proposed algorithm is to optimize the performance of the prediction of early diagnosis from the multimodal dataset by a multi-step framework that uses a

Uni-Buddy: A Multifunctional AI-Powered Assistant for Enhancing University Life: A Use Case at Nile University
Uni-Buddy is an advanced AI system developed to simplify university life at Nile University. It efficiently handles questions in everyday language, accesses real-time university databases, and simultaneously provides accurate responses for multiple users. Its goals include assisting with course registration, academic advising, financial inquiries, campus navigation, and research support. The evaluation demonstrates Uni-Buddy's user-friendly design, effective navigation, language comprehension, and database connectivity proficiency. Compared to similar studies, it stands out for its ease of use
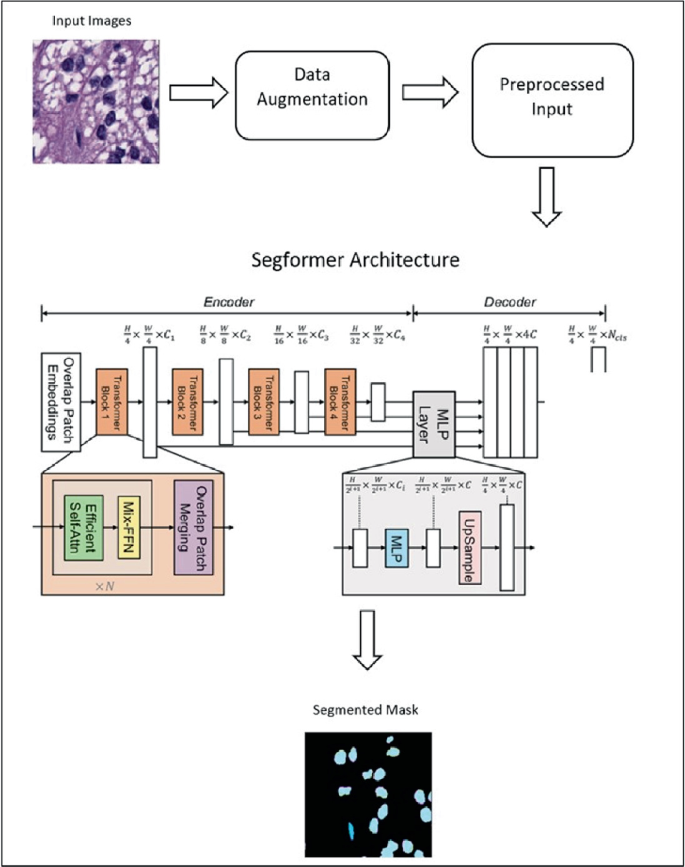
Efficient Semantic Segmentation of Nuclei in Histopathology Images Using Segformer
Segmentation of nuclei in histopathology images with high accuracy is crucial for the diagnosis and prognosis of cancer and other diseases. Using Artificial Intelligence (AI) in the segmentation process enables pathologists to identify and study the unique properties of individual cells, which can reveal important information about the disease, its stage, and the best treatment approach. By using AI-powered automatic segmentation, this process can be significantly improved in terms of efficiency and accuracy, resulting in faster and more precise diagnoses. Ultimately, this can potentially lead
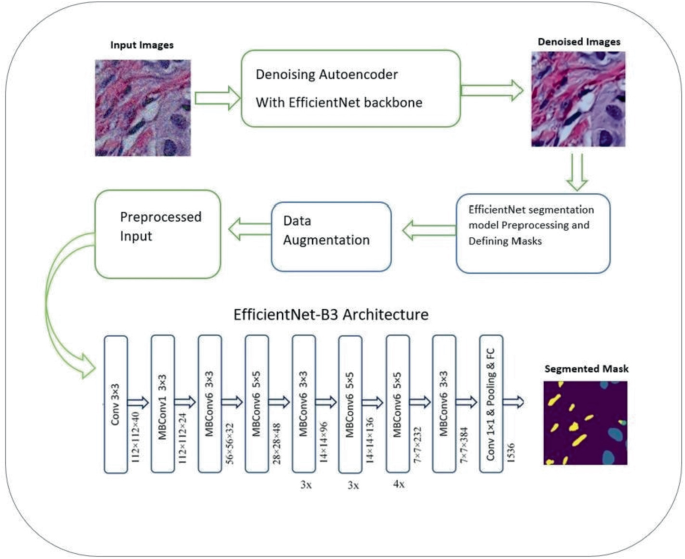
Revolutionizing Cancer Diagnosis Through Hybrid Self-supervised Deep Learning: EfficientNet with Denoising Autoencoder for Semantic Segmentation of Histopathological Images
Machine Learning technologies are being developed day after day, especially in the medical field. New approaches, algorithms and architectures are implemented to increase the efficiency and accuracy of diagnosis and segmentation. Deep learning approaches have proven their efficiency; these approaches include architectures like EfficientNet and Denoising Autoencoder. Accurate segmentation of nuclei in histopathological images is essential for the diagnosis and prognosis of diseases like cancer. In this paper, we propose a novel method for semantic segmentation of nuclei using EfficientNet and
A Multi-scale Self-supervision Method for Improving Cell Nuclei Segmentation in Pathological Tissues
Nuclei detection and segmentation in histopathological images is a prerequisite step for quantitative analysis including morphological shape and size to help in identifying cancer prognosis. Digital pathology field aims to improve the quality of cancer diagnosis and has helped pathologists to reduce their efforts and time. Different deep learning architectures are widely used recently in Digital pathology field, yielding promising results in different problems. However, Deep convolutional neural networks (CNNs) need a large subset of labelled data that are not easily available all the time in
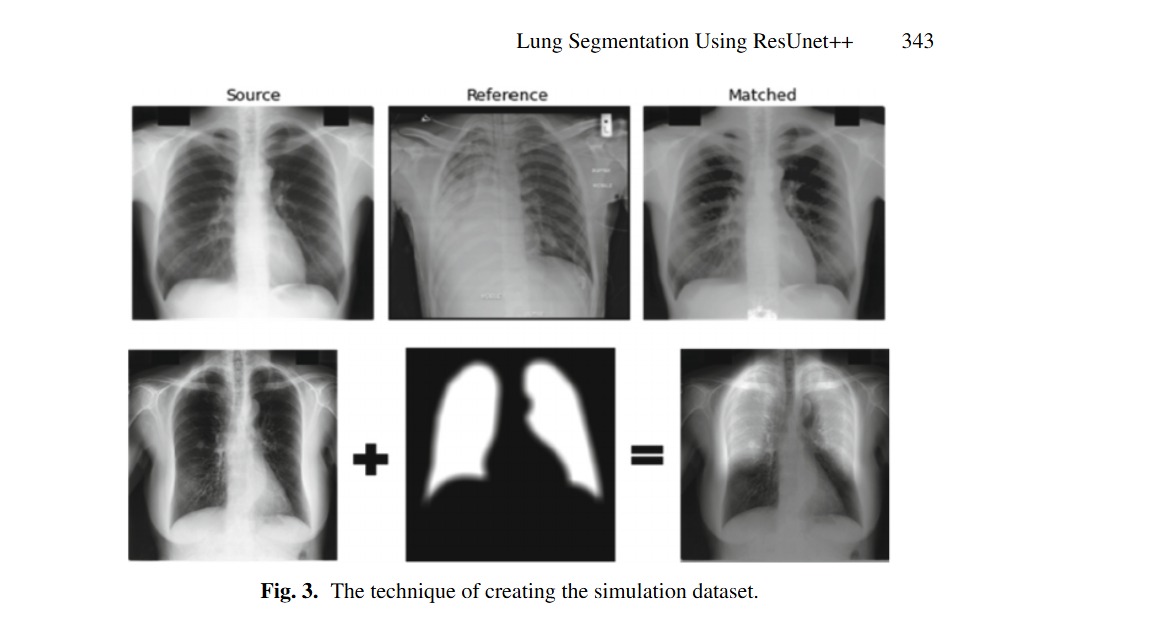
Lung Segmentation Using ResUnet++ Powered by Variational Auto Encoder-Based Enhancement in Chest X-ray Images
X-ray has a huge popularity around the world. This is due to its low cost and easy to access. Most of lung diseases are diagnosed using Chest X-ray (CXR). So, developing computer aided detection (CAD) provided with automatic lung segmentation can improve the efficiency of the detection and support the physicians to make a reliable decision at early stages. But when the input image has image artifacts, then any lung segmentation model will introduce suboptimal lung segmentation results. In this paper, a new approach is proposed to make the lung segmentation model robust and boost the basic
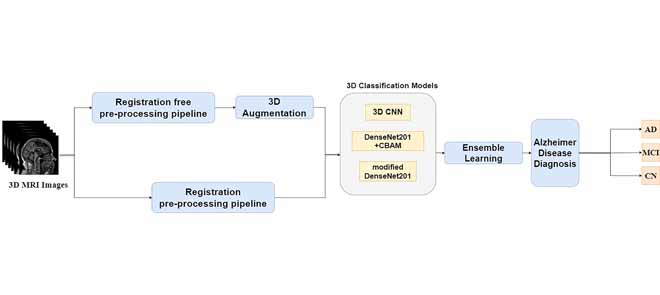
Automatic Early Diagnosis of Alzheimer's Disease Using 3D Deep Ensemble Approach
Alzheimer's disease (AD) is considered the 6 th leading cause of death worldwide. Early diagnosis of AD is not an easy task, and no preventive cures have been discovered yet. Having an accurate computer-aided system for the early detection of AD is important to help patients with AD. This study proposes a new approach for classifying disease stages. First, we worked on the MRI images and split them into an appropriate format to avoid data leakage. Subsequently, a simple and fast registration-free preprocessing pipeline was applied to the dataset. Numerous experiments were conducted to analyze
Does Deep Learning Require Image Registration for Early Prediction of Alzheimer’s Disease? A Comparative Study Using ADNI Database
Image registration is the process of using a reference image to map the input images to match the corresponding images based on certain features. It has the ability to assist the physicians in the diagnosis and following up on the patient’s condition. One of the main challenges of the registration is that it takes a huge time to be computationally efficient, accurate, and robust as it can be framed as an optimization problem. In this paper, we introduce a comparative study to investigate the influence of the registration step exclusion from the preprocessing pipeline and study the counter