
Software and Communications
Numerical simulation of viscoelastic blood flow with hematocrit variation in an arterial segment with two aneurysms
In this study, a viscoelastic model with variable viscosity and relaxation-time is proposed for the simulation of the blood flow in an arterial segment with two aneurysms. The Quemada model is adopted to model both the shear rate-dependent viscosity and hematocrit variation. Available experimental data for the shear rate-dependent relaxation-time of the blood, in a certain range, are fitted and used. The arterial segment with aneurysms is considered as a rigid axisymmetric thin tube with two balloon expansions. The stabilised finite element method with the discrete elastic viscous stress
Optimal fractional-order PID controller based on fractional-order actor-critic algorithm
In this paper, an online optimization approach of a fractional-order PID controller based on a fractional-order actor-critic algorithm (FOPID-FOAC) is proposed. The proposed FOPID-FOAC scheme exploits the advantages of the FOPID controller and FOAC approaches to improve the performance of nonlinear systems. The proposed FOAC is built by developing a FO-based learning approach for the actor-critic neural network with adaptive learning rates. Moreover, a FO rectified linear unit (RLU) is introduced to enable the AC neural network to define and optimize its own activation function. By the means
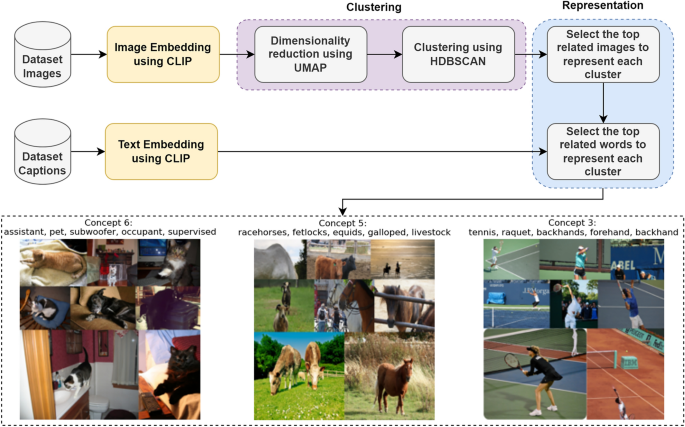
Novel concept-based image captioning models using LSTM and multi-encoder transformer architecture
Captioning an image involves using a combination of vision and language models to describe the image in an expressive and concise sentence. Successful captioning task requires extracting as much information as possible from the corresponding image. One of these key pieces of information is the topic to which the image belongs. The state-of-the-art methods used topic modeling depending only on caption text in order to extract these topics. The problem with extracting the topics using topic modeling only on caption text is that it lacks the consideration of the image’s semantic information
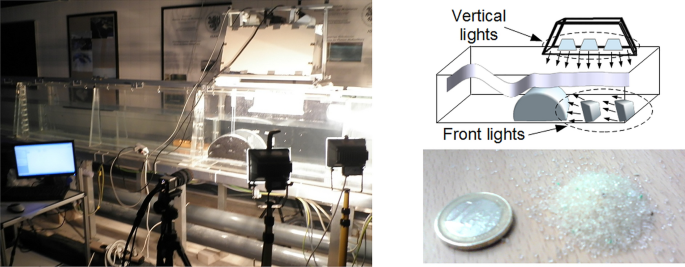
Numerical simulation and PIV measurements of the wave-induced flow field near semi-circular breakwaters
Abstract: Careful design of the high-tech semi-circular breakwaters (SBW), which are used for protection against sea waves, is essential to avoid the failure of these large-scale projects. An improved design tool adopting numerical simulations, complemented with experimental measurements is introduced. Unstructured boundary-fitted grids are used to model the curved SBW boundary accurately and resolve the flow adjacent to it. Experimental measurements based on Particle Image Velocimetry (PIV) are introduced and the numerically simulated velocity fields are validated. For the first time, the

Physics-Constrained Data-Driven Dynamic Modeling of Underactuated Robotic Systems
Underactuated robots are intriguing systems that have found numerous applications across various fields. These systems are characterized by having fewer actuators than degrees of freedom, resulting in complex behaviors that challenge traditional modeling and control techniques. Despite the prevalent use of data-driven modeling, extracting the dynamic model of underactuated systems is particularly challenging. This paper focuses on deriving from data the dynamic model of the Double Inverted Pendulum on a Cart (DIPC). The Euler-Lagrange equations are employed to derive the model's terms from the

Preprocessing Trajectory Learning Techniques For Robots: A comparative study
Many applications in our everyday living are totally depending on using the robots. So that, the need for having smart and more productive robots is increasing. Developing such robots necessitates the programming of the robot. Hence, the machine learning approaches are widely employed to accomplish this objective successfully. Programming the robot can be applied by demonstration such that the skills are transferred to robots through supplying examples of the desired movement. Multiple trajectories are observed and modelled in order to learn new skills by obtaining a general trajectory of the
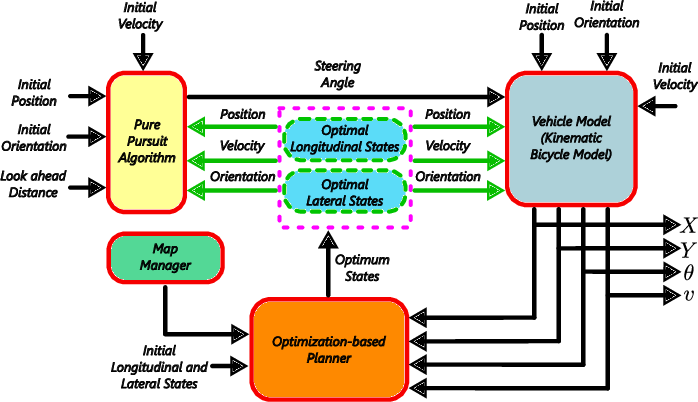
Trajectory Planning for Safety-Critical Driving Scenarios based on Dynamic Programming
Autonomous Vehicles (AVs) are critical, and nowadays are essential technology that transfers traditional transportation systems into smart, and driverless ones. Considering the available processed data and information that came from localization, perception, and HD map, AVs could exceed the limit of the efficiency and safety of those conventional systems. AVs could use enhanced techniques and algorithms to execute safety-critical scenarios in dynamic environments that have static and dynamic obstacles, traffic signs,..., etc. This paper aims to propose a novel motion planning algorithm that

Thermodynamic, phase diagram, and high-entropy alloys system: basic concepts
The evolution of alloy-based materials, transitioning from simple binary alloy systems to more intricate compositions, has played a pivotal role in facilitating the advancement of innovative technologies and, in turn, driving social progress. This transformative journey has been accompanied by a significant enhancement in humanity’s capacity to create novel materials. High-entropy alloys (HEAs) have emerged as a recent and noteworthy class of materials due to their novel concept and remarkable properties. These alloys exhibit exceptional mechanical characteristics, boasting impressive strength
Concept, phase selection rule, challenges, and future prospective of high-entropy alloys
High-entropy alloys (HEAs) have emerged as a promising class of materials that exhibit exceptional mechanical properties, corrosion resistance, and high-temperature stability. They have become a significant area of research in the materials science domain owing to their potential for a wide range of applications. This chapter provides an overview of the concept, phase selection rules, the challenges faced, and the future perspectives of HEAs. © 2024 Elsevier Inc. All rights are reserved including those for text and data mining AI training and similar technologies.

Characterization and properties of high-entropy alloys materials
High-entropy alloys (HEAs) are a relatively new class of materials that have been attracting significant attention in material science and engineering research. This chapter provides an introductory discourse on the microstructural characterization and properties of these fascinating materials. The term “HEAs” refers to an innovative concept of metallic materials composed of multiple principal elements, each with concentrations between 5% and 35%. Unlike conventional alloys, which typically comprise one principal element with minor alloying additions, HEAs possess a unique composition that can