
Software and Communications

A comprehensive guide to high-entropy alloy subgroups
Despite the fact that numerous equiatomic and nonequiatomic high-entropy alloys (HEAs) have been observed to form a single solid solution (SS), it has also been established that several intermediate phases can emerge, some of which exhibit the structural characteristics of intermetallic compounds (ICs) such as Laves, B2, sigma, L12, and amorphous phases. This phenomenon has been extensively documented by researchers, and it is primarily attributed to a range of competing factors, including the mixing enthalpy, mixing entropy, and disparities in atomic sizes among the constituent elements

High-Entropy Alloys: Design, Manufacturing, and Emerging Applications
High-Entropy Alloys: Design, Manufacturing, and Emerging Applications presents cutting-edge advances in the field of these materials, covering their mechanics, methods of manufacturing, and applications, all while emphasizing the link between their structure/microstructure and functional properties. The book starts with a section on the fundamentals of high-entropy alloys (HEAs), with chapters discussing their thermodynamics, subgroups (transition metal; refractory; ceramics; metallic glasses and more), physical metallurgy, and microstructural characterization. The next section features
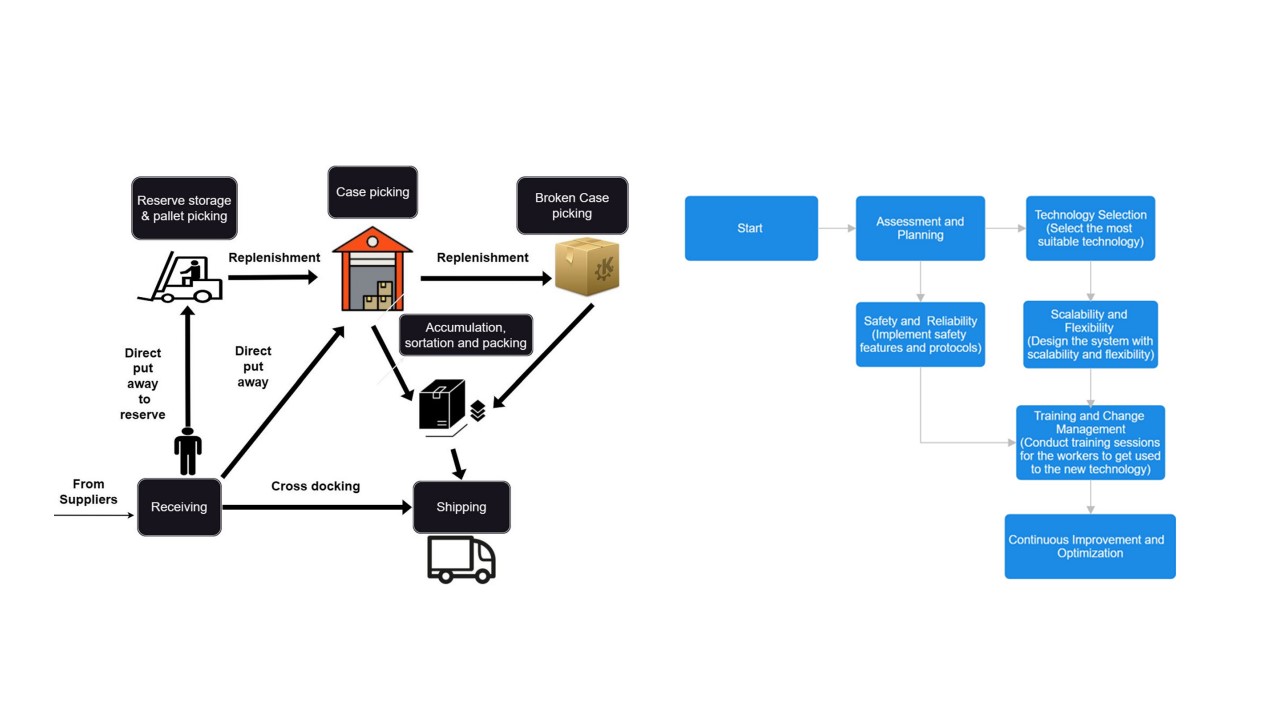
AGV and Industry 4.0 in warehouses: a comprehensive analysis of existing literature and an innovative framework for flexible automation
The just-in-time concept, mass customization, omnichannel distribution, and the rising global population have all fueled the logistics sector. Consequently, using automation inside the warehouses to make them more dynamic and sustainable for the future is one of the crucial components to adapt to this quick shift. Giants in the industry and technology are becoming more interested in the “smart warehouse” system, built with innovative warehousing technologies, as an achievable solution for the development of warehouses in the future. To contextualize the past and provide light on prospective
Implementation of process optimization to maximize line productivity in pharmaceutical industries
Abstract: Macro Group is the largest player in Egypt’s fast-growing cosmeceutical industry founded in 2002, and Macro has about 149 stock-keeping units (“SKUs”) with a 31.4% market share in 2022. The macro group has three-ampoule products for hair, namely, Atrakta, Verdex, and Solodex with an expected forecast of 134,655 FG in 2023 and it’s expected to reach 261,000 FG in 2027. 188 working days per year in 2023 are required to manufacture the forecasted units and 365 working days to manufacture 2027 forecasted units. Through observing the production line of Atrakta, it has been noticed that
Optimum Selection of Communication Tower Structures Based on Wind Loads & lifecycle cost analysis
Communication towers are vital assets in our daily lives as they transfer signals between cell phones facilitating communication and commerce among people and businesses all around the world. Wind loads are crucial in the communication towers design since they are tall and slender. With climate change bringing more storms and higher wind speeds, it is more crucial to research the finest tower structure that withstands such conditions with the least life cycle cost. Therefore, in this paper, a comparative case study is performed between 45 m height lattice tower and monopole tower in Egypt. Two
Comparative Analysis of Wind-loaded Telecom Tower Structures with Recommendations
Telecommunication towers are essential infrastructure in today's fast-paced world. Lattice self-supporting towers, monopole towers, and guyed towers are the three types of structures that can be used for telecommunications towers. When analyzing telecom tower loads, wind loads are the most important ones to address. As a result, it is necessary to choose an appropriate structure that can withstand the wind and the surrounding environment. The main aim of this paper is to propose a guideline for selecting the optimum tower structure based on the surrounding environment. In order to create this

Secure Data Aggregation in Cultural Heritage Monitoring: NMEC Case Study
Intelligent management plays a vital role in the preservation and success of cultural heritage, particularly in the context of museums. To ensure the long-term safeguarding of valuable and significant artifacts housed in museums, regular inspections are necessary. In this specific research study, the National Museum of Egyptian Civilization (NMEC) serves as a case study. To effectively monitor the museum's environment and protect its cultural assets, a wireless sensor network (WSN) is proposed. This network comprises various sensors that monitor crucial environmental factors such as
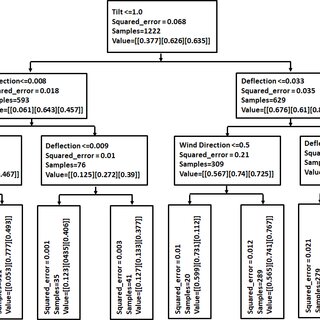
Stability Analysis and Fault Detection of Telecommunication Towers Using Decision Tree Algorithm under Wind Speed Condition
This paper presents a decision tree (DT) modeling technique to estimate any increase in the load on telecommunication towers. A structural analysis was done for the lattice and mono-pole towers using TNX Tower software to determine the basic features of the towers, such as tilt angle, deflection, twist, and acceleration. The structure analysis generated a data set based on wind speeds. This data set was then used to train a machine-learning algorithm to estimate the loads on the structure. Any change in the applied loads greater than the loads considered in the design might be identified using
Microfactory strategic decision making using simulation
This paper aims to study how the agility concept is successfully applied in manufacturing facilities. The study is involved in selecting the industry and the machines for the novel Microfactory established at Nile Preneurs, Nile University, with focus on the sheet metal workshop located in the Microfactory. The recommendations of this work include the most suitable layout, scheduling technique according to the manufacturing lead time, utilization, work in process, tool change over and distance travelled by operators. Flexsim simulation software is used to determine the optimum combination of
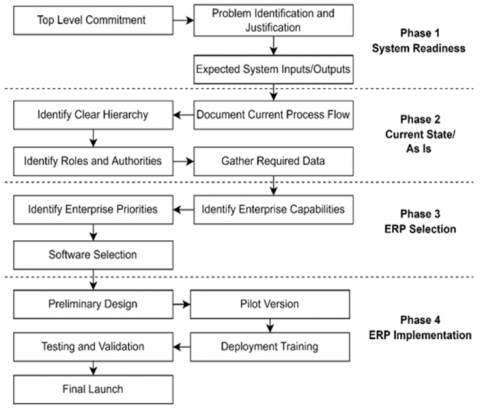
Novel Integrated Framework for ERP Selection and Implementation
As the economic pressure on businesses increases, organizations try to adopt innovative technology solutions to cope with this pressure and adapt to the rapid market changes. Particularly for small and medium enterprises (SMEs). They must integrate all resources and information levels to highly utilize their limited resources and survive the local and global competition. This could be achieved by adopting the best suitable Enterprise Resource Planning (ERP) system. On the other hand, properly selecting and implementing the right ERP system is challenging for many reasons. Hence, this paper