
Software and Communications
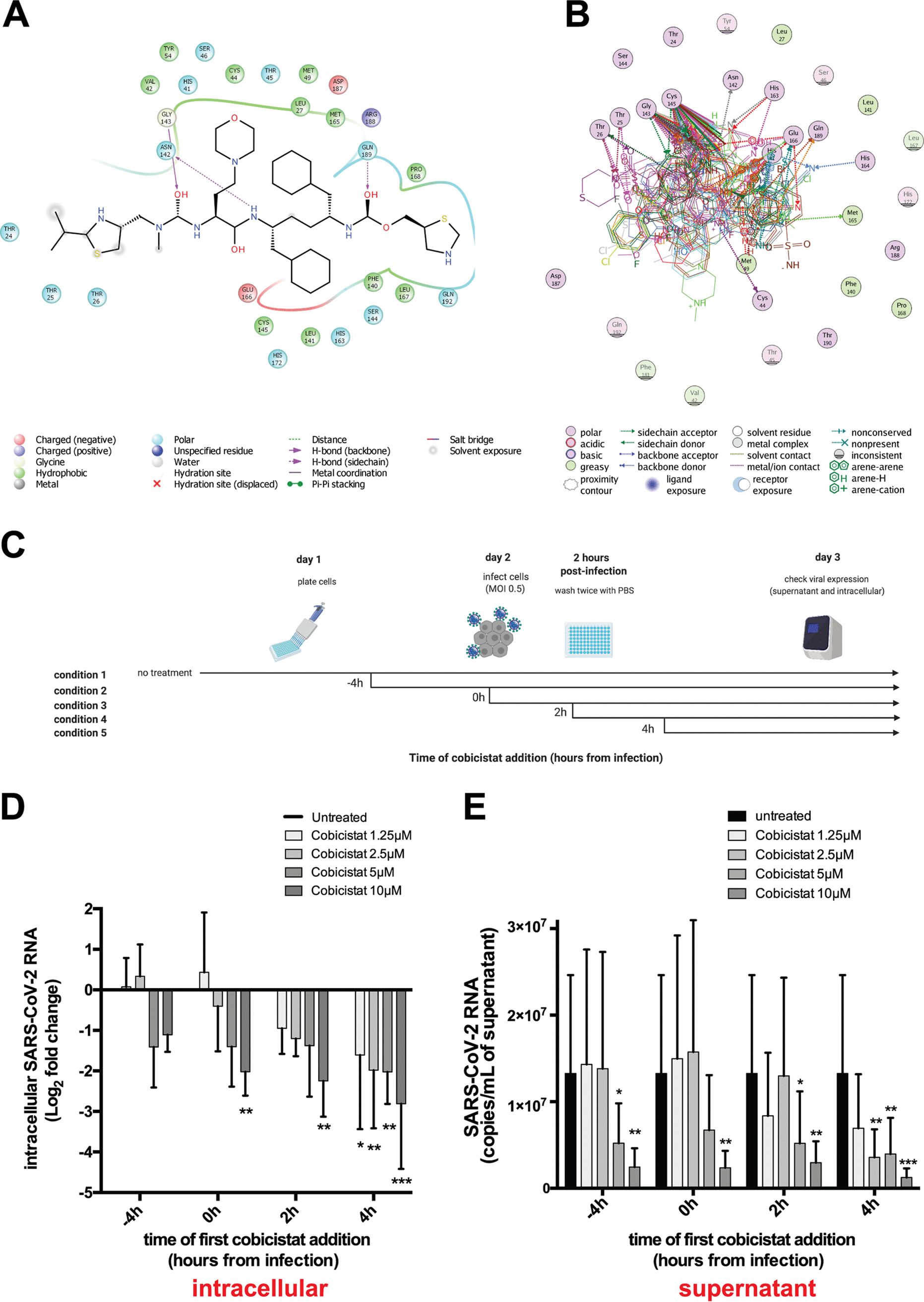
The FDA-Approved Drug Cobicistat Synergizes with Remdesivir to Inhibit SARS-CoV-2 Replication in Vitro and Decreases Viral Titers and Disease Progression in Syrian Hamsters
Combinations of direct-acting antivirals are needed to minimize drug resistance mutations and stably suppress replication of RNA viruses. Currently, there are limited therapeutic options against the severe acute respiratory syndrome coronavirus 2 (SARS-CoV-2), and testing of a number of drug regimens has led to conflicting results. Here, we show that cobicistat, which is an FDA-approved drug booster that blocks the activity of the drug-metabolizing proteins cytochrome P450-3As (CYP3As) and P-glycoprotein (P-gp), inhibits SARS-CoV-2 replication. Two independent cell-to-cell membrane fusion
Immunoinformatics approach of epitope prediction for SARS-CoV-2
Background: The novel coronavirus (SARS-CoV-2) caused lethal infections worldwide during an unprecedented pandemic. Identification of the candidate viral epitopes is the first step in the design of vaccines against the viral infection. Several immunoinformatic approaches were employed to identify the SARS-CoV-2 epitopes that bind specifically with the major histocompatibility molecules class I (MHC-I). We utilized immunoinformatic tools to analyze the whole viral protein sequences, to identify the SARS-CoV-2 epitopes responsible for binding to the most frequent human leukocyte antigen (HLA)
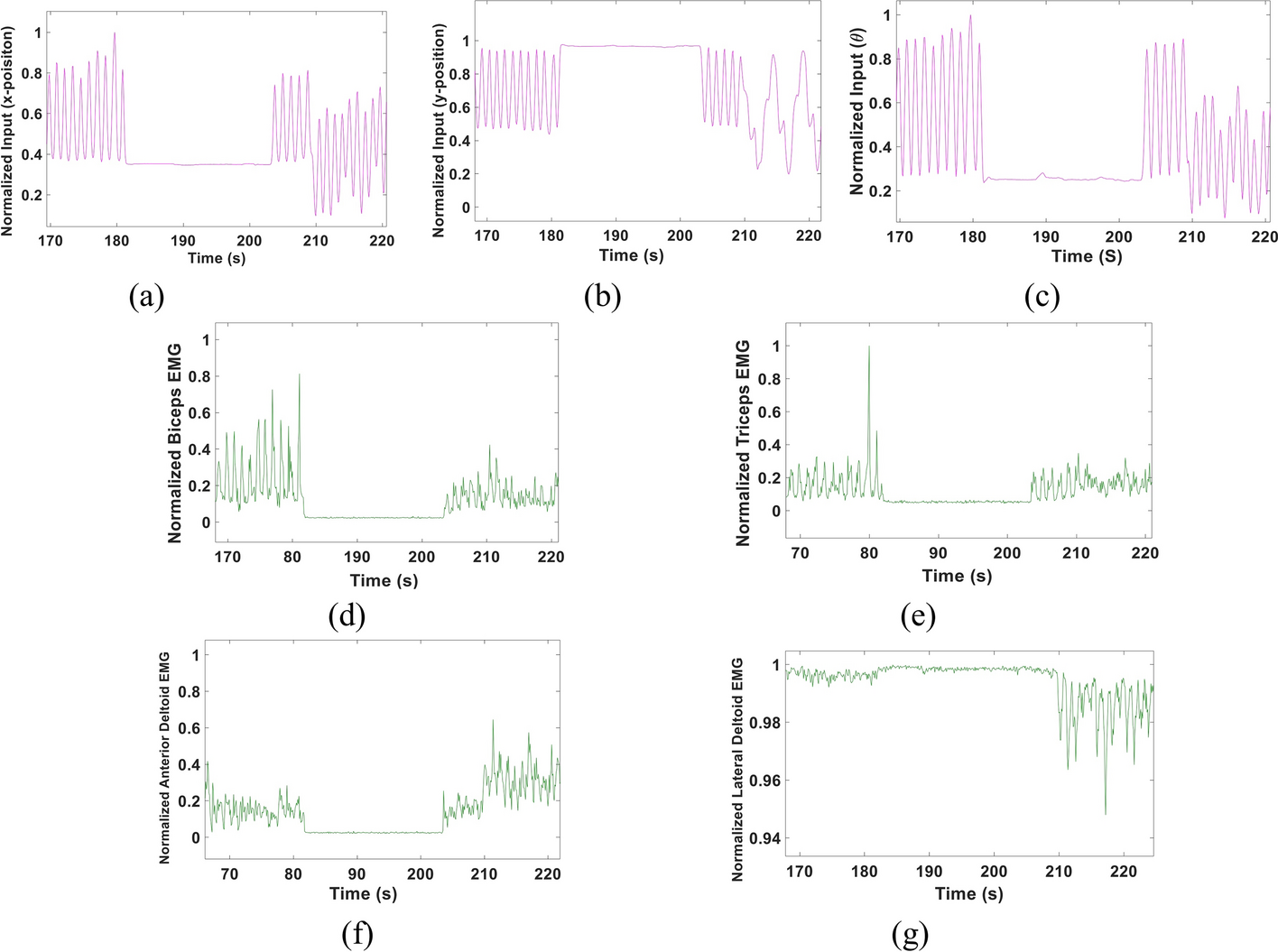
A multi-Kalman filter-based approach for decoding arm kinematics from EMG recordings
Background: Remarkable work has been recently introduced to enhance the usage of Electromyography (EMG) signals in operating prosthetic arms. Despite the rapid advancements in this field, providing a reliable, naturalistic myoelectric prosthesis remains a significant challenge. Other challenges include the limited number of allowed movements, lack of simultaneous, continuous control and the high computational power that could be needed for accurate decoding. In this study, we propose an EMG-based multi-Kalman filter approach to decode arm kinematics; specifically, the elbow angle (θ), wrist
Machine Learning-Based Prediction of Backhaul Capacity Requirements for Cellular Networks
The accurate prediction of the required backhaul transmission capacity for cellular networks is critical to ensure efficient and reliable network performance, especially with the increasing demand for high-speed data services and the introduction of new radio technologies. This paper presents a framework for predicting the required capacity of backhaul networks based on the base stations' radio resources utilization and serving radio conditions. The proposed framework utilizes machine learning techniques to accurately estimate the required backhaul capacity by analyzing the base stations'
NGU_CNLP at WANLP 2022 Shared Task: Propaganda Detection in Arabic
This paper presents the system developed by the NGU_CNLP team for addressing the shared task on Propaganda Detection in Arabic at WANLP 2022. The team participated in the shared tasks' two sub-tasks which are: 1) Propaganda technique identification in text and 2) Propaganda technique span identification. In the first sub-task the goal is to detect all employed propaganda techniques in some given piece of text out of a possible 17 different techniques, or to detect that no propaganda technique is being used in that piece of text. As such, this first sub task is a multi-label classification

Database Security: Current Challenges and Effective Protection Strategies
Database security has grown to a necessary level of importance today, characterized by the escalating demand for data storage. The surge in data storage requirements, propelled by technological advancements, has led to increased attacks targeting database security vulnerabilities. While multiple storage and protection methods have emerged in tandem with evolving technologies, the discovery of security vulnerabilities has led to new attack vectors. This study aims to repair this gap by securing and fortifying the security of stored data within databases. Fundamental to information security, the
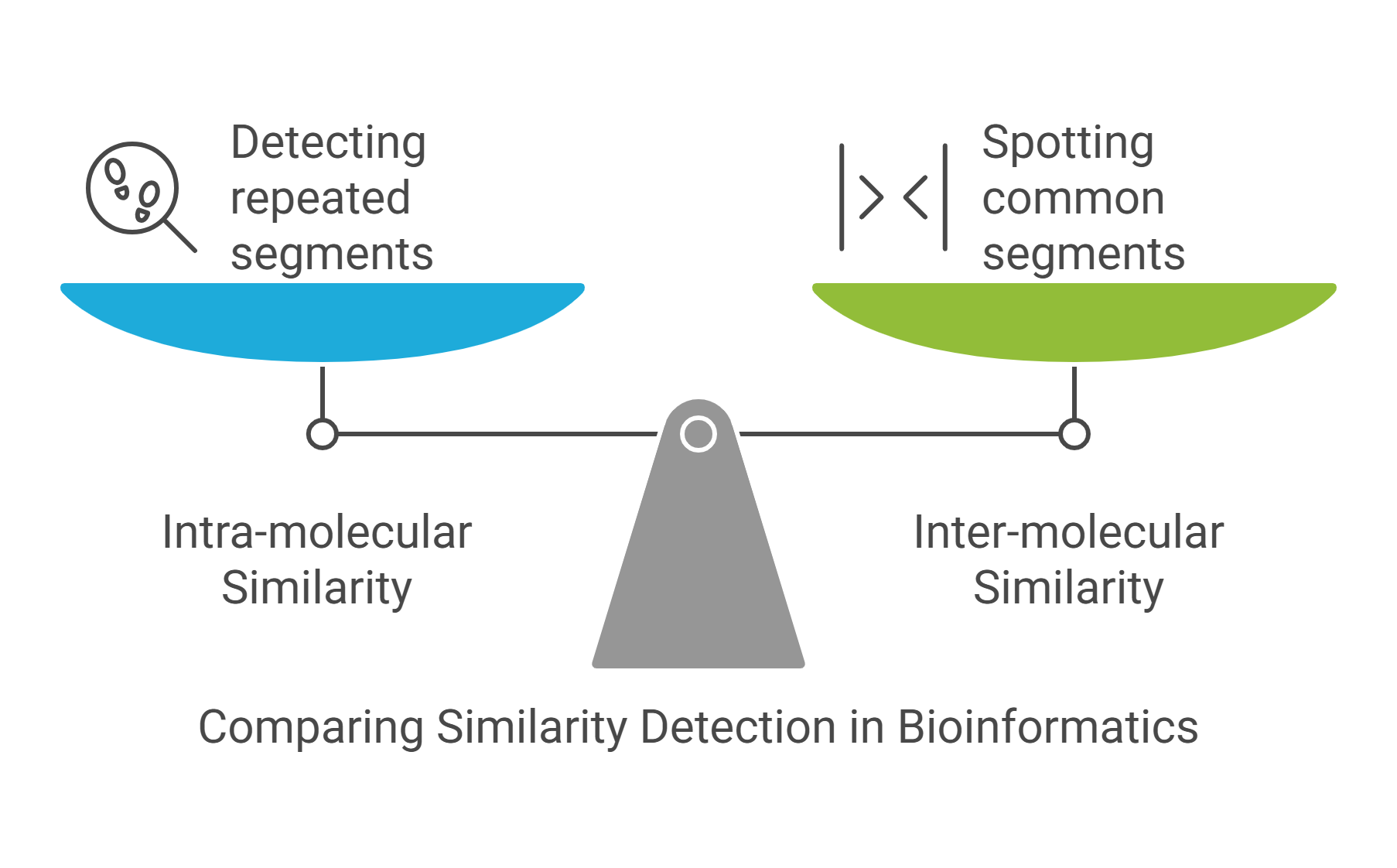
String mining in bioinformatics
Sequence analysis is a major area in bioinformatics encompassing the methods and techniques for studying the biological sequences, DNA, RNA, and proteins, on the linear structure level. The focus of this area is generally on the identification of intra-and inter-molecular similarities. Identifying intra-molecular similarities boils down to detecting repeated segments within a given sequence, while identifying inter-molecular similarities amounts to spotting common segments among two or multiple sequences. From a data mining point of view, sequence analysis is nothing but string-or pattern

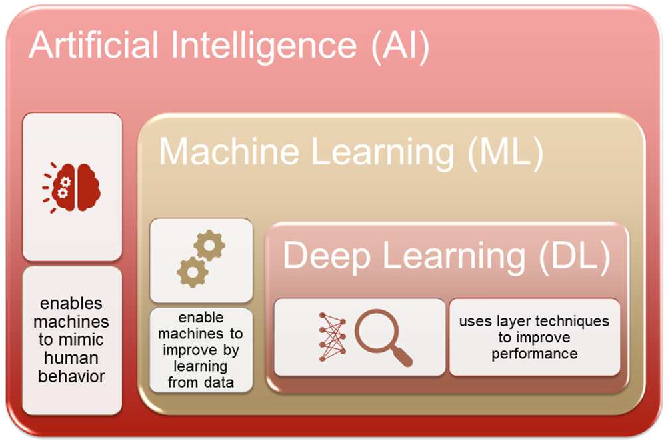
Computational Intelligence for Medical Internet of Things (MIoT) Applications
Computational Intelligence for Medical Internet of Things (MIoT) Applications: Machine Intelligence Applications for IoT in Healthcare explores machine intelligence techniques necessary for effective MIoT research and practice, taking a practical approach for practitioners and students entering the field. This book investigates advanced concepts and applications in the MIoT field, guiding readers through emerging developments and future trends. A wide range of international authors guide readers through advanced concepts, including deep learning, neural network, and big data analytic
AI for Automated Thoracic Disease Assessment from X-Ray Imaging: a Review
With the increasing availability of digital X-ray imaging, artificial intelligence (AI) has emerged as a promising tool for automating the assessment of thoracic diseases. The objective of this study is to systematically review the artificial intelligence (AI) and deep learning methods proposed for the automated assessment of thoracic diseases from chest X-ray images. A thorough search of the relevant literature was conducted, and studies that met the inclusion criteria were critically reviewed. Information on the datasets, model architectures, evaluation metrics, and results was extracted
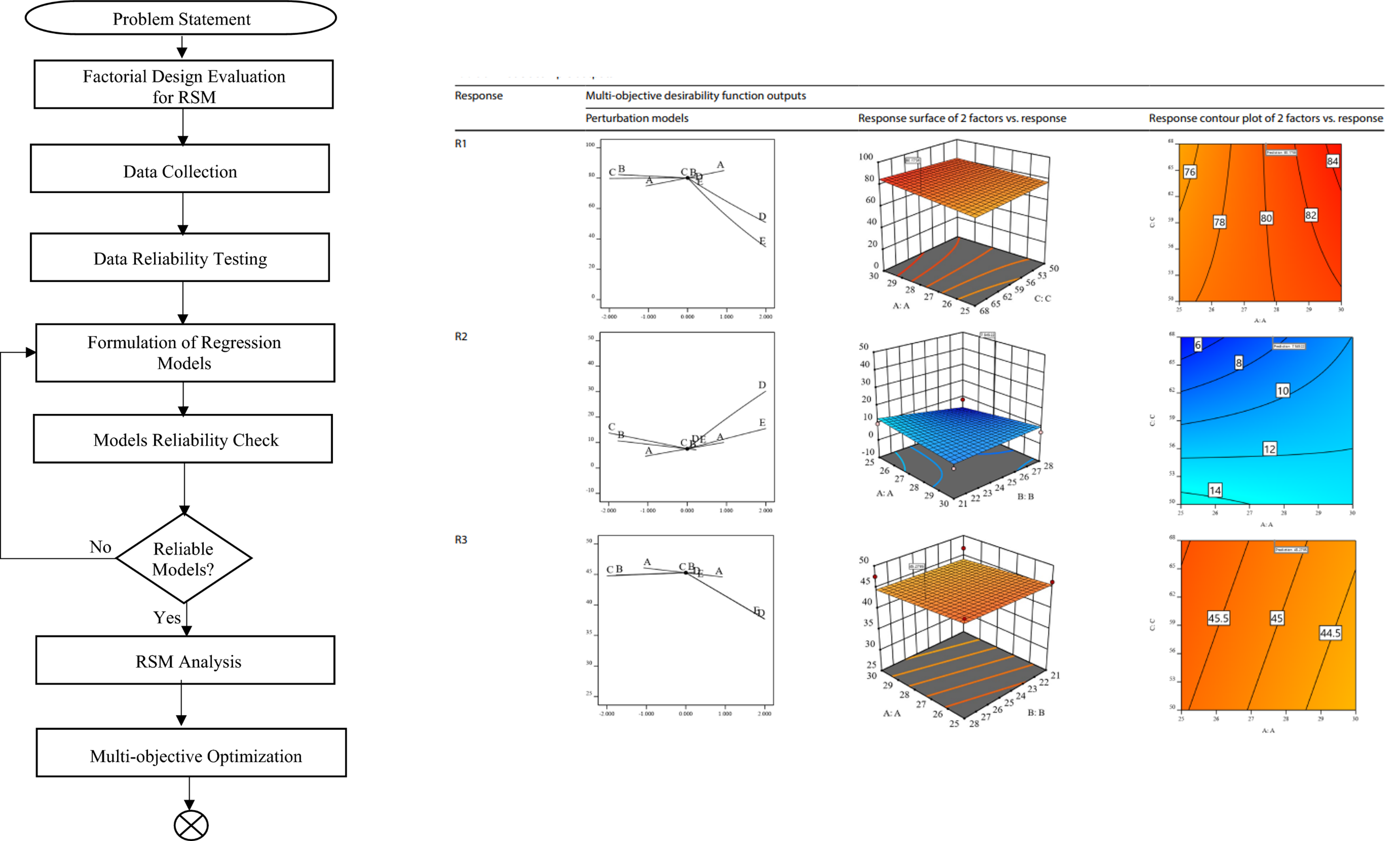
Multi-objective ergonomics design model optimization for micro electric cars via response surface methodology
Despite advancements in ergonomic comfort assessments in automotive design, optimizing seat dimensions within the constrained spaces of micro-electric cars presents a substantial challenge. In this study, response surface methodology (RSM) is utilized for the ergonomics design of a micro electric car in the conceptual design phase. Specifically, five critical seat dimensions are analyzed: Seatback Angle, Seat Base Angle, Steering Wheel Height from Car Base, Distance from Seat Base to Pedals, and Distance from Seat Base to Steering Wheel. The analysis took place using a 2-level full factorial