
Software and Communications
Mechanical and environmental performance assessment of cotton stalk composites with natural adhesives for sustainable construction materials
Carbon dioxide emissions pose a global issue, with deforestation, forest loss from logging, fires, and construction highlighting the adverse effects of climate change. Urgent action is required to reduce carbon dioxide emissions and preserve forests. Egypt can contribute to reducing greenhouse gas emissions by effectively utilizing its waste resources, especially agricultural waste. The research focuses on developing environmentally friendly and sustainable construction materials with a forward-looking approach. This involves exploring alternative options for synthetic formaldehyde adhesives
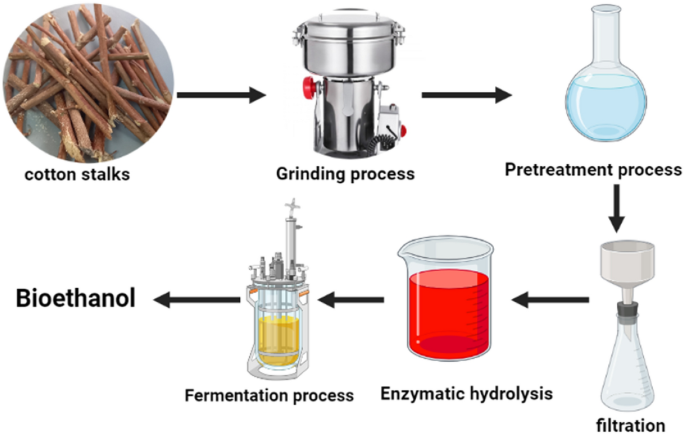
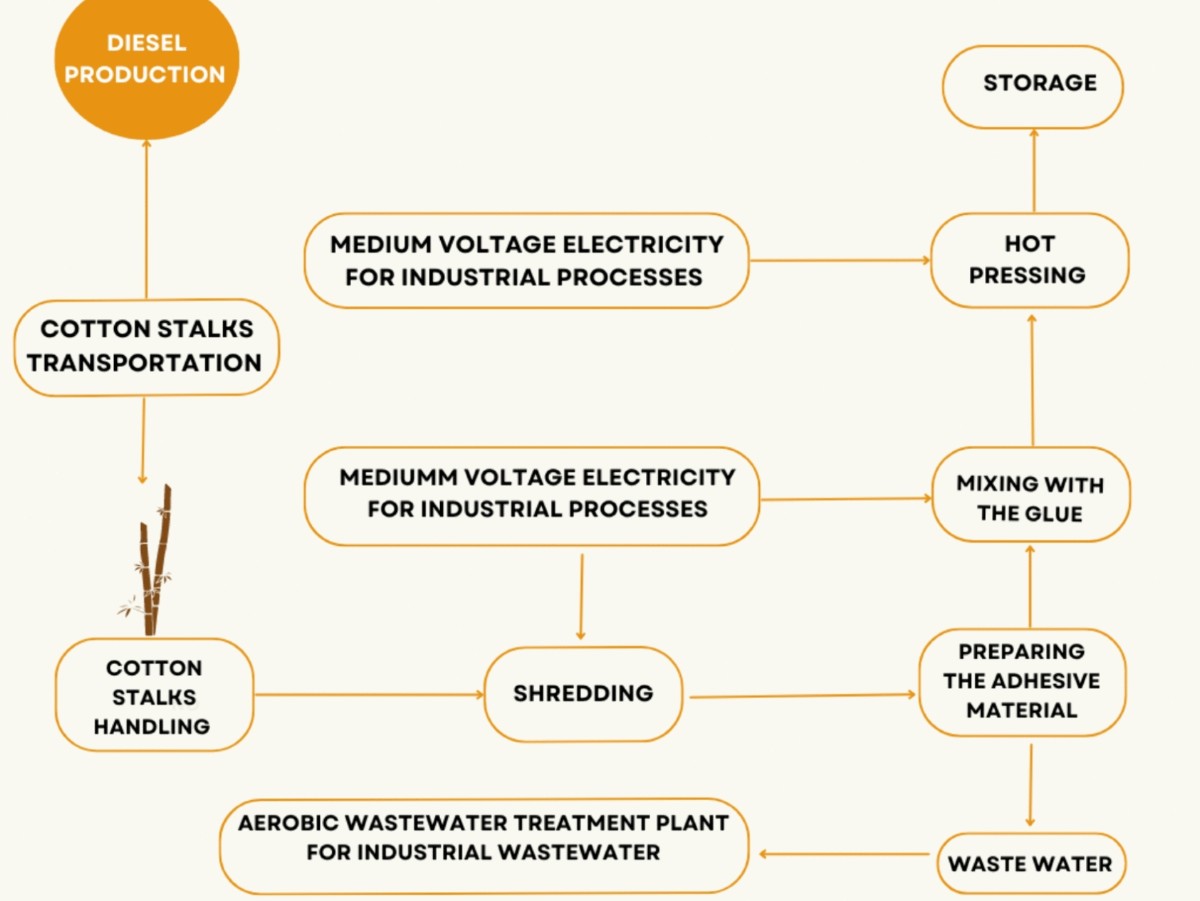
A comparative cradle-to-gate life cycle assessment of three cotton stalk waste sustainable applications
This paper presents a novel approach to utilizing agricultural waste. It compares three different applications for cotton stalks: fabrication of wood composites, bioethanol production, and biogas cradle-to-gate Life cycle assessment production processes. Cotton cultivation generates a lot of debris, mostly cotton stalks, which are incinerated or landfilled, Sustainable resource management is critical for maintaining the ecosystem, and economic stability, and promoting social fairness since it ensures the long-term availability of resources while minimizing environmental damage. The

Nanoionic liquid for hydrogen generation and storage
Climate change and the increase in population are encouraging many researchers to work on getting nonconventional sources of energy. Ionic liquids (ILs) have unique physicochemical properties for this field. Therefore, using nanoionic liquids and ILs in energy storage is very promising, particularly considering the reported high efficiency in the existing literature. Hydrogen production technologies have garnered considerable interest in the energy sector, particularly involving the formation of water from a petroleum field and carbon steel materials. Modern methods rely on hydrogen production

Technological innovation in ergonomics & safety in automotive industries in Egypt
The increase in the complexity and the inspiring environment between the automotive organizations in Egypt forced the quality experts and management team to propose various tools related to Quality Management Systems but there is a slight apprehension to the ergonomic concepts in these industries. This study investigates the complications related to the ergonomics in the assembly line of an automotive company in Egypt. The assembly line is divided into several stations including trim line, chassis line and a glass handling station. The focus of this study is the ergonomics of the glass
Analysis of musculoskeletal disorders in personal care industries in Egypt
The increase in the complexity of operations in personal care industries in Egypt forced the ergonomic experts to propose various tools to analyze the human errors and eliminate the most dangerous operations according to the international standards of safety and ergonomics. International references such as the Rapid Upper Limb Assessment (RULA) and Rapid Entire Body Assessment (REBA) analysis are performed to investigate different postures as well as Computer Aided Three-Dimensional Interactive Application (CATIA) and Maynard Operation Sequence Technique (MOST softwares). A modified scissor

The Effect of Directional Tactile Memory of the Back of the User on Reaction Time and Accuracy
Tactile memory is the cognitive process of storing and recalling information that has been perceived through the sense of touch. Directional tactile memory involves the encoding and retrieval of sensory data associated with a tactile experience, allowing individuals to remember and recognize directional information encoded through the sense of touch. A new method for providing directional tactile feedback, at the back of the user, has been developed to investigate the efficacy of directional tactile memory, its decay over time, and its impact during a concurrent cognitive task. Two experiments

Dynamic Distributed Monitoring for 6LoWPAN-based IoT Networks
—Mission-critical Internet of Things (IoT)-based networks are increasingly employed in daily and industrial infrastructures. The resilience of such networks is crucial. Given IoT networks’ constantly changing nature, it is necessary to provide dependability and sustainability. A robust network monitoring can reinforce reliability, such that the monitoring mechanism adapts itself to real-time network instabilities. This work proposes a proactive, dynamic, and distributed network monitoring mechanism with monitor placement and scheduling for 6LoWPAN-based IoT networks intended for mission

Modeling circular supply chains as an approach for waste management: A systematic review and a conceptual framework
All world countries are suffering from repercussions of the global climate change problems and there is an urgent need to mitigate their negative impacts. Improper waste management methods contribute directly to climate change where common waste treatment methods are basically relying on incineration or landfilling. Nowadays, incorporating the circular economy perspective into the business model demonstrates the ability of creating value from wastes and reducing the residuals by adopting the circular supply chains management (CSCM) as a promising alternative to linear supply chains. Studying
Modelling stress-strain curves and forming limit curves using deep learning
The sheet metal forming process stands one of the most principal applications in production engineering with the goal of producing defect free products possessing the mechanical properties that met the working conditions requirements. The efficient metal forming process relies on a deep understanding of the material behaviour during the forming process. To achieve this, feasibility studies for new incoming components helps determine if a part is feasible for manufacturing or if design modifications are required. This simulation requires an accurate material card to replicate the real material

Commercial Versus Natural Activated Carbon Fabricated Sheets: Applied to Dyes Removal Application
Industrial dyes are considered one of the main causes of increased water pollution of water. Many businesses, such as steel and paper, are located along riverbanks because they require large amounts of water in their manufacturing processes, and their wastes, which contain acids, alkalis, dyes, and other chemicals, are dumped and poured into rivers as effluents. For example, chemical enterprises producing aluminum emit a significant quantity of fluoride into the air and effluents into water bodies. Fertilizer facilities produce a lot of ammonia, whereas steel plants produce cyanide. Many