
Software and Communications
MOS realizations of fractional-order elements
The exploitation of fractional calculus in engineering applications requires the utilization of fractional-order elements. As there is no immediate access to such type of elements, emulators that proportionally imitate their behavior are developed. The realization of emulators of fractional-order elements is based on the approximation of their impedance function. Subsequently, an advantageous option for the circuit implementation of the obtained, approximated impedance function is MOS transistor-based configurations, as they provide a dynamic system with electronically adjustable parameters
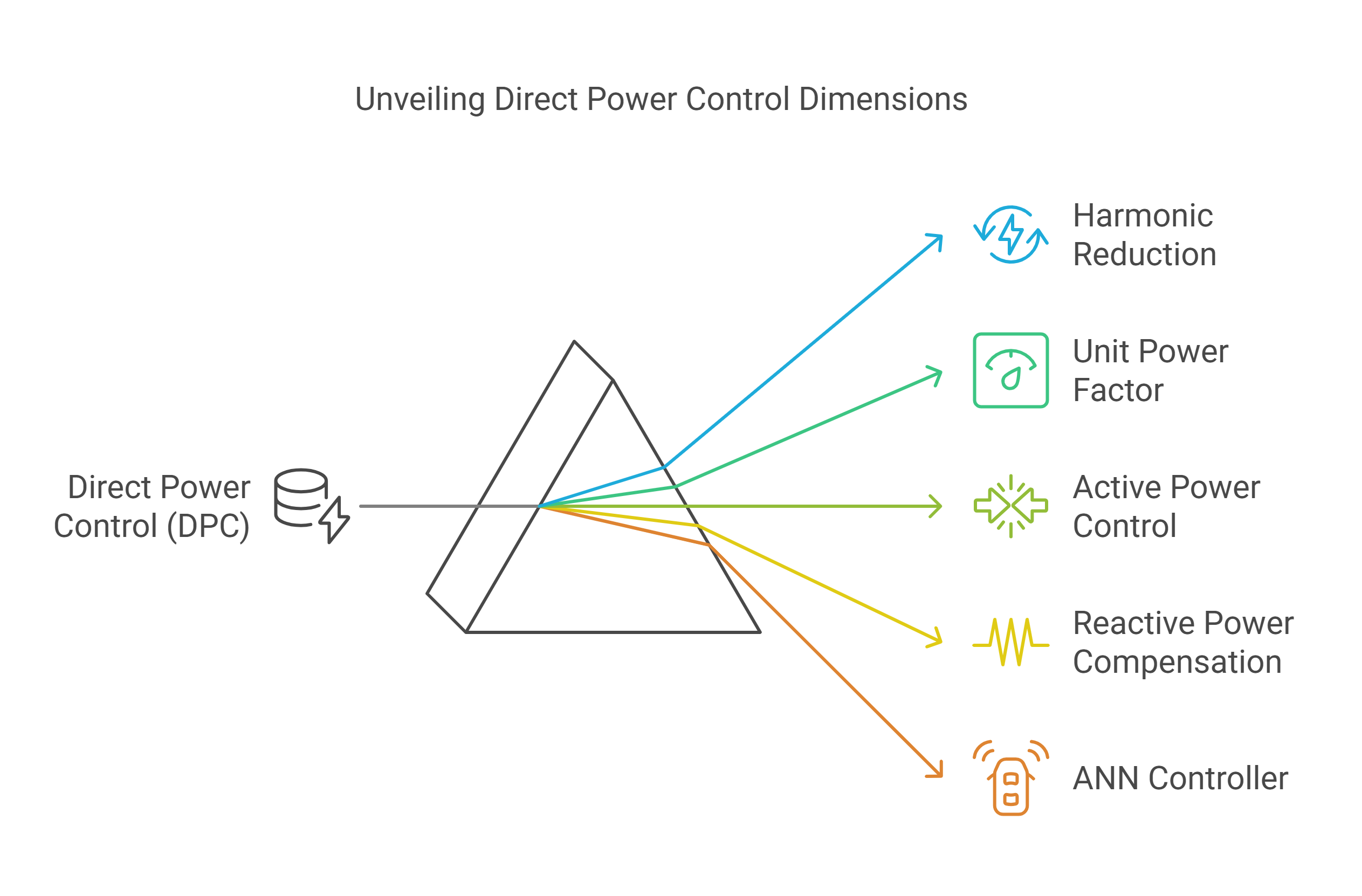
Artificial neural network for PWM rectifier direct power control and DC voltage control
In this chapter, a new technique has been proposed for reducing the harmonic content of a three-phase PWM rectifier connected to the networks with a unit power factor and also providing decoupled control of the active and reactive instantaneous power. This technique called direct power control (DPC) is based on artificial neural network (ANN) controller, without line voltage sensors. The control technique is based on well-known direct torque control (DTC) ideas for the induction motor, which is applied to eliminate the harmonic of the line current and compensate for the reactive power. The
Smarter CRM Solutions in the Emerging Technologies Age
There are trends across modern Customer Relationship Management (CRM) solutions that are centered on emerging technologies such as Artificial Intelligence (AI), internet of things (IoT), and Blockchain to improve the overall customer experience. Smart CRM solutions focus on embedding emerging technologies capabilities within marketing, sales, and service functionalities to turns unpredictable customer journeys into predictive and interactive experiences. For example, applying artificial intelligence and machine learning to customer data and Internet of Things data allows organizations to
Pronounced fluctuations of pions in ring-like events in 16O-Ag/Br interactions at 60 A GeV/c in the framework of complex network analysis
Visibility graphs (VGs), horizontal visibility graphs (HVGs) and the sandbox algorithm (SB) are applied for multifractal characterization of complex network systems that are converted from time series measurements, are used to characterize the fluctuations in pseudorapidity densities of singly charged particles produced in 16O-AgBr interactions at 60AGeV. The work presents the analysis of ring-like and jet-like events in terms of multifractality characterization of 16O-AgBr interactions at 60AGeV. We systematically compared the experimental events of both ring- and jet-like events with Monte
Rapidity distribution within Landau hydrodynamical model and EPOS event-generator at AGS, SPS, and RHIC energies
The rapidity distribution of well-identified particles such as pions, kaons, protons and their antiparticles measured in AGS, SPS, and BRAHMS experiments (Au+Au collisions), at various energies spanning from higher energies sNN = 200 down to lower energies 2 GeV, are compared with that obtained from huge statistical ensembles of 100, 000 events generated from the Cosmic Ray Monte Carlo (CRMC) EPOS event-generator. All these data are then compared to the results calculated in the frame work of Landau hydrodynamical model. The EPOS event-generator can describe the experimental data of the
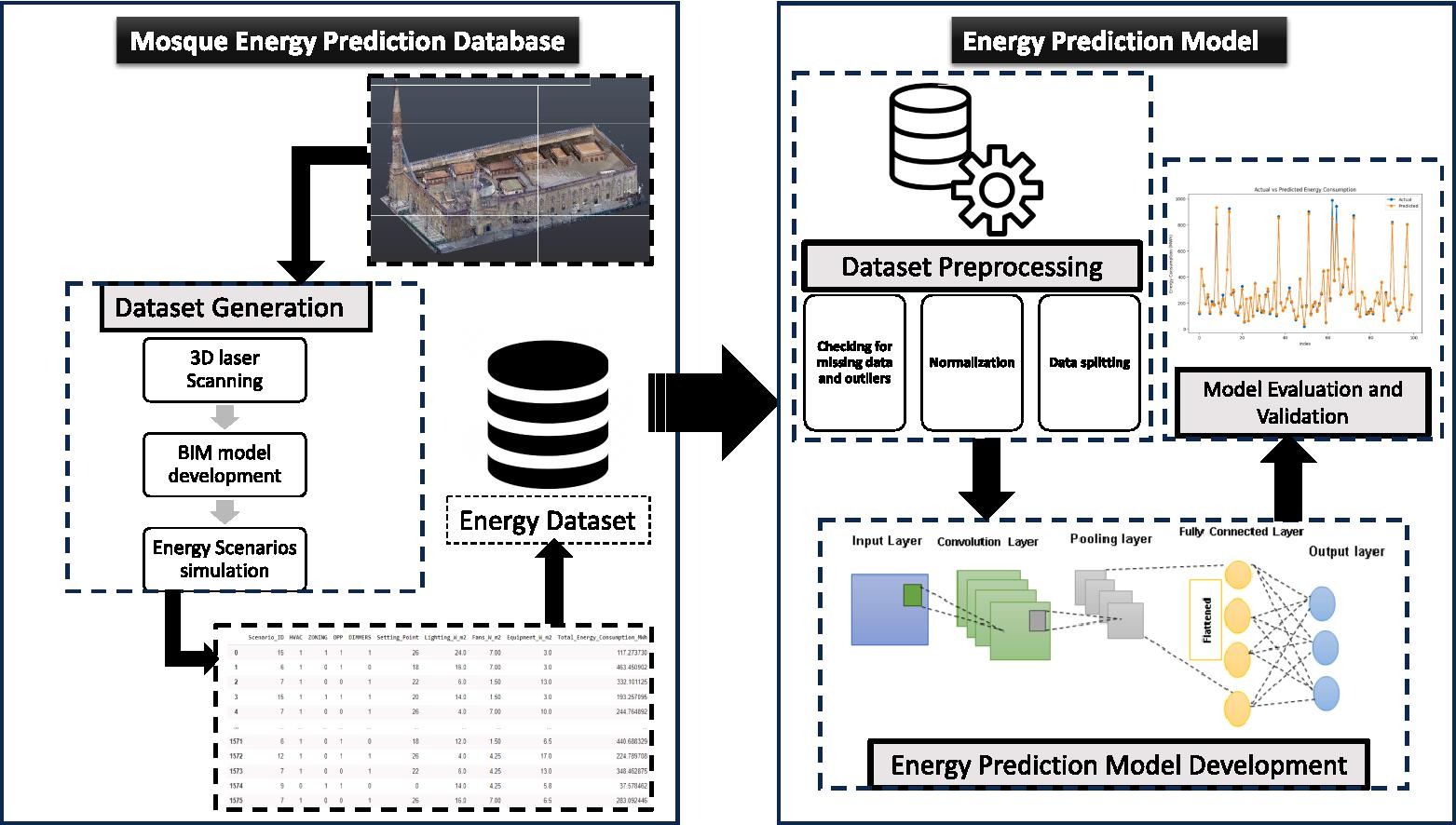
Predicting energy consumption of mosque buildings during the operation stage using deep learning approach
The energy consumption resulting from the construction sector is increasing rapidly. Different building types have different energy consumption schemes, especially during their operational stage. Among these types of buildings, mosques are considered one of the intermittent building types that suffer from huge energy wastage. That's why there is a need to monitor their operational performance through retrofitting or changing their operational scheme to enhance their operational performance and examine the effect of different alterations on the annual energy consumption. However, using
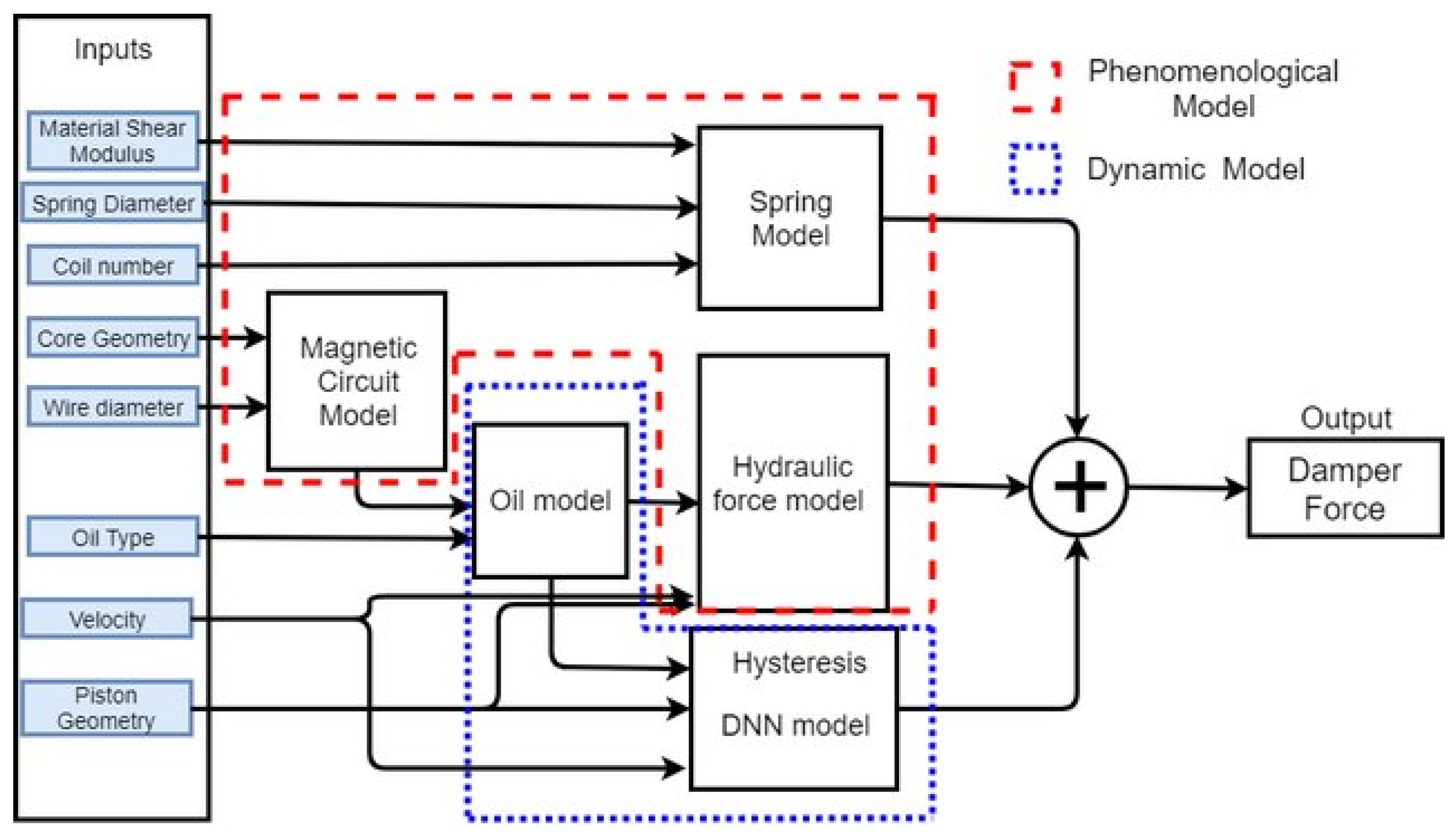
Adjustment of Tall Building Behavior by Guided Optimization of Magneto-Rheological Damper Control Parameters
Magneto-rheological dampers (MR-Dampers) are increasingly being used in construction applications to reduce the dynamic response of structures to seismic activities or severe wind loading. Sensors attached to the structure will signal the computer to supply the dampers with an electric charge that transfers the MR fluid to a near-solid material with different physical and mechanical properties (viscoelastic behavior). Control algorithms govern the fluid to near-solid conversion, which controls the behavior of the damper and the performance of the structure under the seismic or wind loading
A Fractional Variable Order Model of COVID-19 Pandemic
2020 has witnessed a rapidly spread pandemic COVID-19 which is one of the worst in the history of mankind. Scientists believe that COVID-19 spreads mainly from a person to another. Recent researches consider bats as a vector for COVID-19. This paper suggests a variable fractional order model for COVID-19 to figure out how bats and hosts interact, and how the seafood market affect people. The proposed model assumes that infection cannot be recovered. The basic reproduction number R0 for real data on reported cases in Wuhan China was computed. Disease-free equilibrium points and proposed model
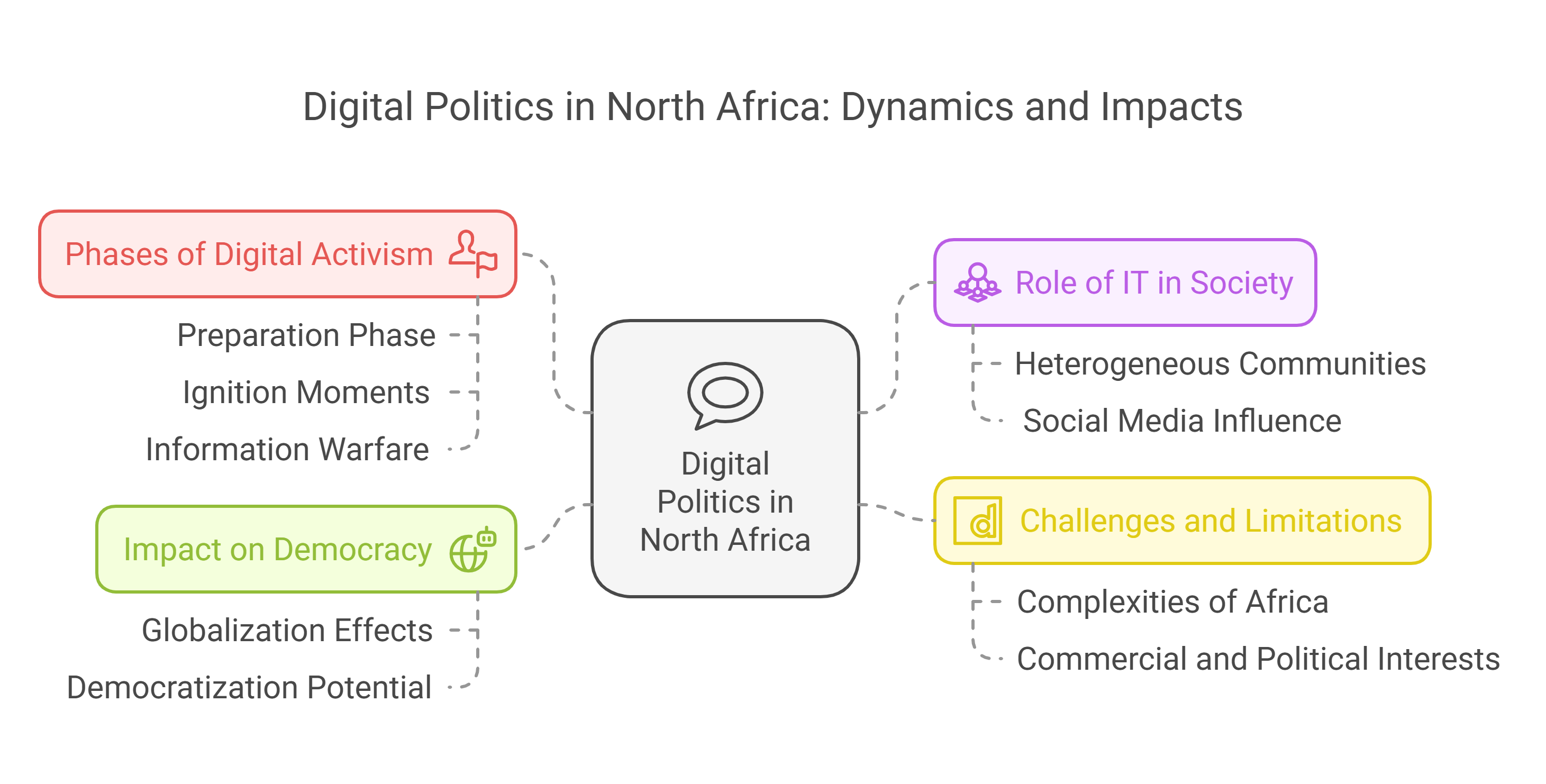
Digital politics in north Africa: Possibilities to reverse subversion
North Africa is marked with an unmatched phenomena of increase in IT (Adeiza, 2013), though IT users are not homogenous groups, but rather heterogeneous communities with diverse interests and motivations. As explained by the Swiss Agency for Development and Cooperation (SDC) that technology itself cannot solely make a difference in the practice of the sociopolitical and economic progress, but rather the other way around where indicators of development behind the technology drives the change. IT is thus an instrument, not a goal (Sarrazin, 2011). The synergy between politics and IT is
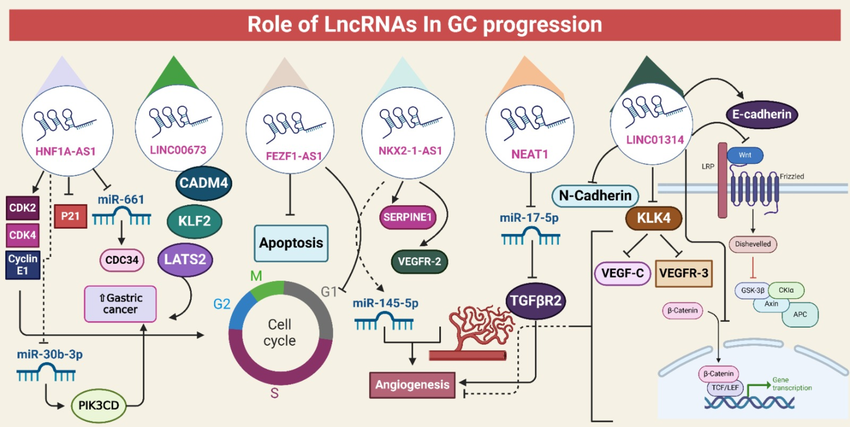
LncRNAs orchestration of gastric cancer - particular emphasis on the etiology, diagnosis, and treatment resistance
Gastric cancer (GC) remains a major public health challenge worldwide. Long non-coding RNAs (lncRNAs) play important roles in the development, progression, and resistance to the treatment of GC, as shown by recent developments in molecular characterization. Still, an in-depth investigation of the lncRNA landscape in GC is absent. However, The objective of this systematic review is to evaluate our present understanding of the role that lncRNA dysregulation plays in the etiology of GC and treatment resistance, with a focus on the underlying mechanisms and clinical implications. Research that