
Software and Communications
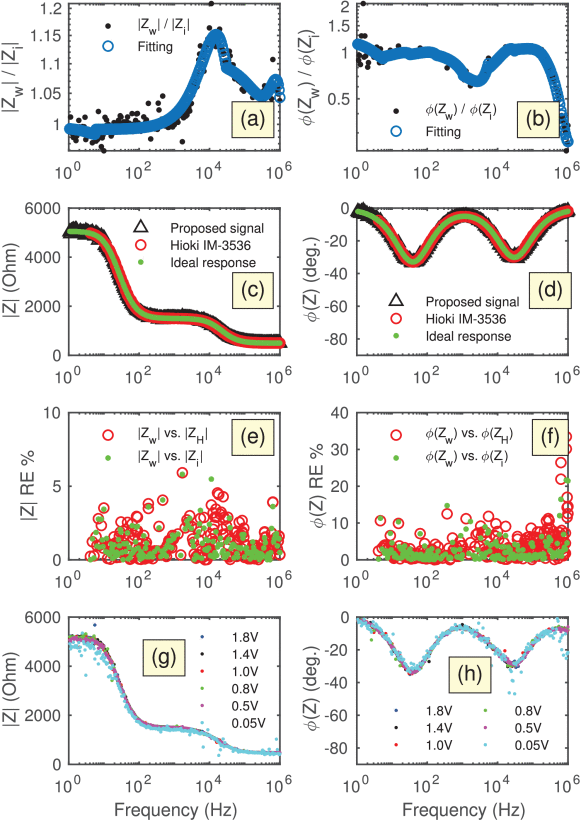
Time-Frequency Design of a Multi-Sine Excitation with Random Phase and Controllable Amplitude for (Bio) Impedance Measurements
Impedance spectroscopy has become a standard electroanalytical technique to study (bio)electrochemical and physiological systems. From an instrumentation point of view, the measurement of impedance can be carried out either in the frequency domain using the classical frequency sweep method or in the time domain using a variety of broadband signals. While time-domain techniques can be implemented with relatively simple hardware and can achieve faster acquisition time, they are still not that popular because of their lower accuracy and modularity. In this work we present a method and an
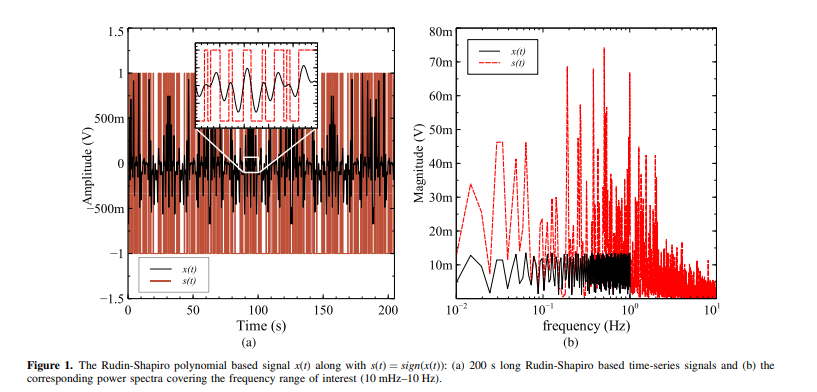
Electrical Impedance Spectroscopy Using a Wide-Band Signal Based on the Rudin-Shapiro Polynomials
Electrochemical Impedance Spectroscopy (EIS) has become an increasingly important diagnostic and monitoring tool in many industries. An obstacle that arises when employing EIS in low and ultra low sub-Hz frequencies is the long measurement time associated with using the conventional frequency-sweep method. One possible solution to this problem is to use wide-band signals that cover at once the entire frequency range of interest. In this work, we explore and validate the use of such a signal obtained from the Rudin-Shapiro polynomial over the frequency range 10 mHz to 10 Hz. The proposed signal
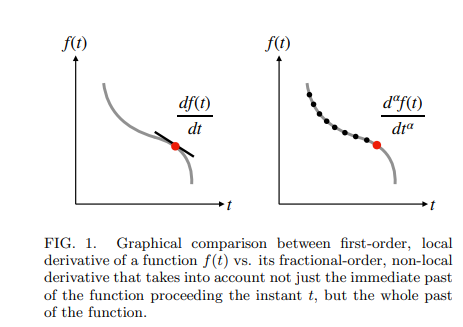
Extended RC Impedance and Relaxation Models for Dissipative Electrochemical Capacitors
Electrochemical capacitors are a class of energy devices in which complex mechanisms of accumulation and dissipation of electric energy take place when connected to a charging or discharging power system. Reliably modeling their frequency-domain and time-domain behaviors is crucial for their proper design and integration in engineering applications, knowing that electrochemical capacitors in general exhibit anomalous tendency that cannot be adequately captured with the traditional RC-based models. In this study, we first review some of the widely used fractional-order models for the
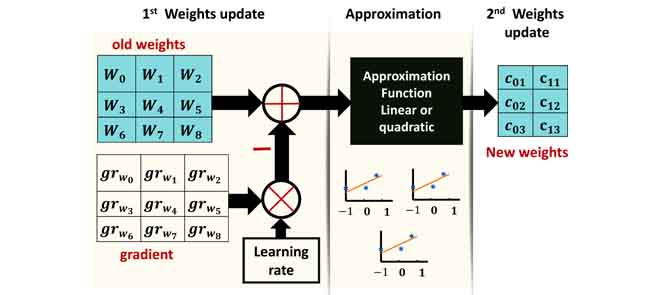
Deep Neural Networks-Based Weight Approximation and Computation Reuse for 2-D Image Classification
Deep Neural Networks (DNNs) are computationally and memory intensive, which present a big challenge for hardware, especially for resource-constrained devices such as Internet-of-Things (IoT) nodes. This paper introduces a new method to improve DNNs performance by fusing approximate computing with data reuse techniques for image recognition applications. First, starting from the pre-Trained network, then the DNNs weights are approximated based on the linear and quadratic approximation methods during the retraining phase to reduce the DNN model size and number of arithmetic operations. Then, the
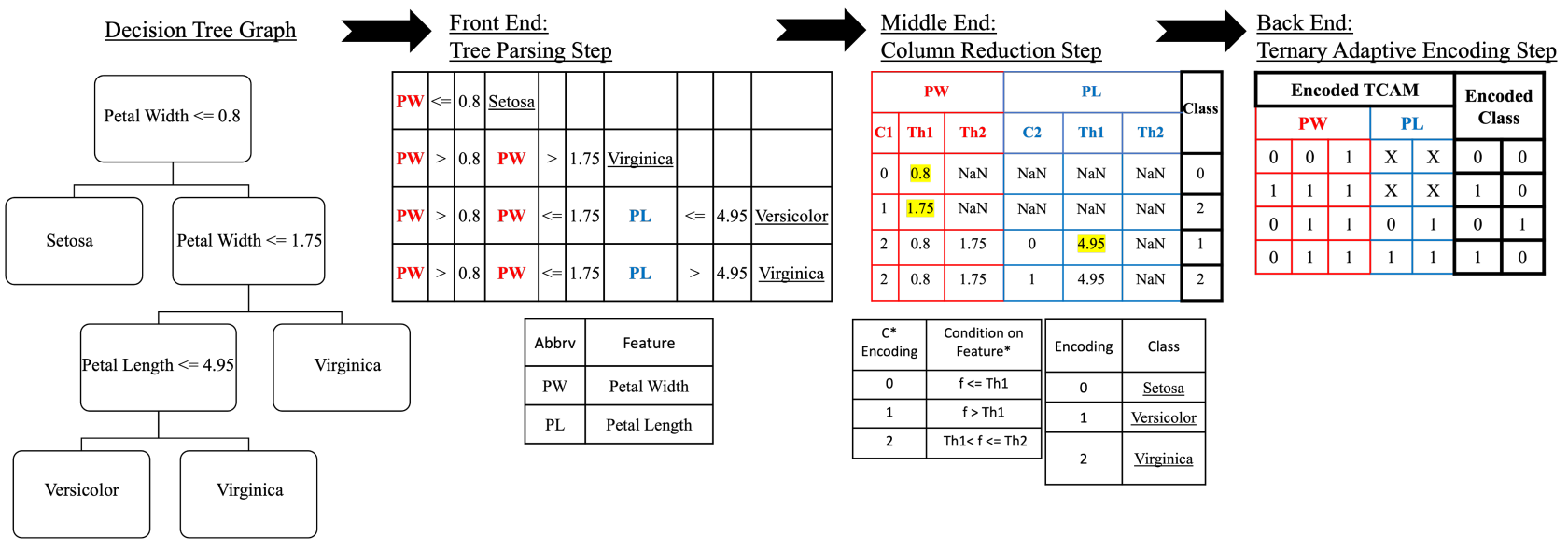
DT2CAM: A Decision Tree to Content Addressable Memory Framework
Decision trees are powerful tools for data classification. Accelerating the decision tree search is crucial for on-the-edge applications with limited power and latency budget. In this article, we propose a content-addressable memory compiler for decision tree inference acceleration. We propose a novel 'adaptive-precision' scheme that results in a compact implementation and enables an efficient bijective mapping to ternary content addressable memories while maintaining high inference accuracies. We also develop a resistive-based functional synthesizer to map the decision tree to resistive
A note on the bandwidth of negative group delay filters
An updated definition of group delay bandwidth in analog filters is introduced in this work. Unlike existing definitions, this new definition considers simultaneously the value of the group delay and filter gain, leading to minimized distortion in the filter output. In addition, it offers the capability of handling wide-band signals without introducing errors in the shape of their envelopes. Selected first- and second-order filters are studied and simulation results are provided to validate the efficiency of the new definition. © 2024 The Author(s). International Journal of Circuit Theory and
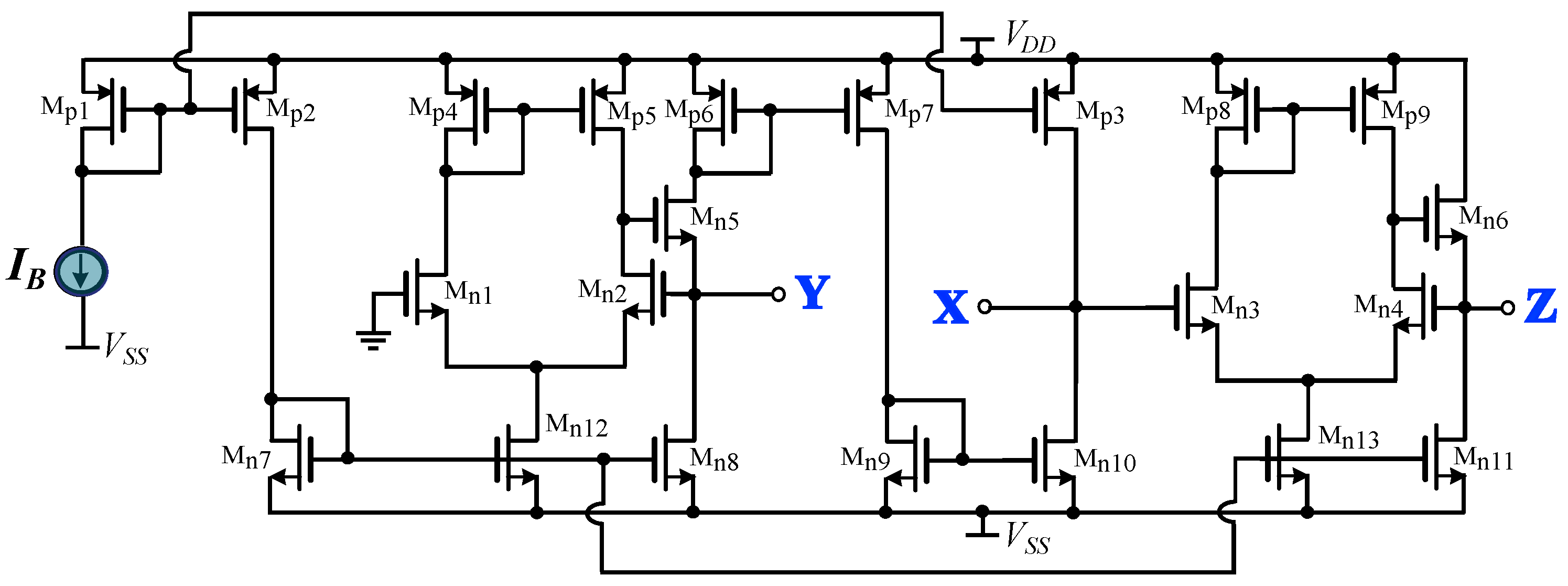
Minimum Active Component Count Design of a PIλDμ Controller and Its Application in a Cardiac Pacemaker System †
A generalized structure for implementing fractional-order controllers is introduced in this paper. This is achieved thanks to the consideration of the controller transfer function as a ratio of integer and non-integer impedances. The non-integer order impedance is implemented using RC networks, such as the Foster and Cauer networks. The main offered benefit, with regards to the corresponding convectional implementations, is the reduced active and, also, passive component count. To demonstrate the versatility of the proposed concept, a controller suitable for implementing a cardiac pacemaker
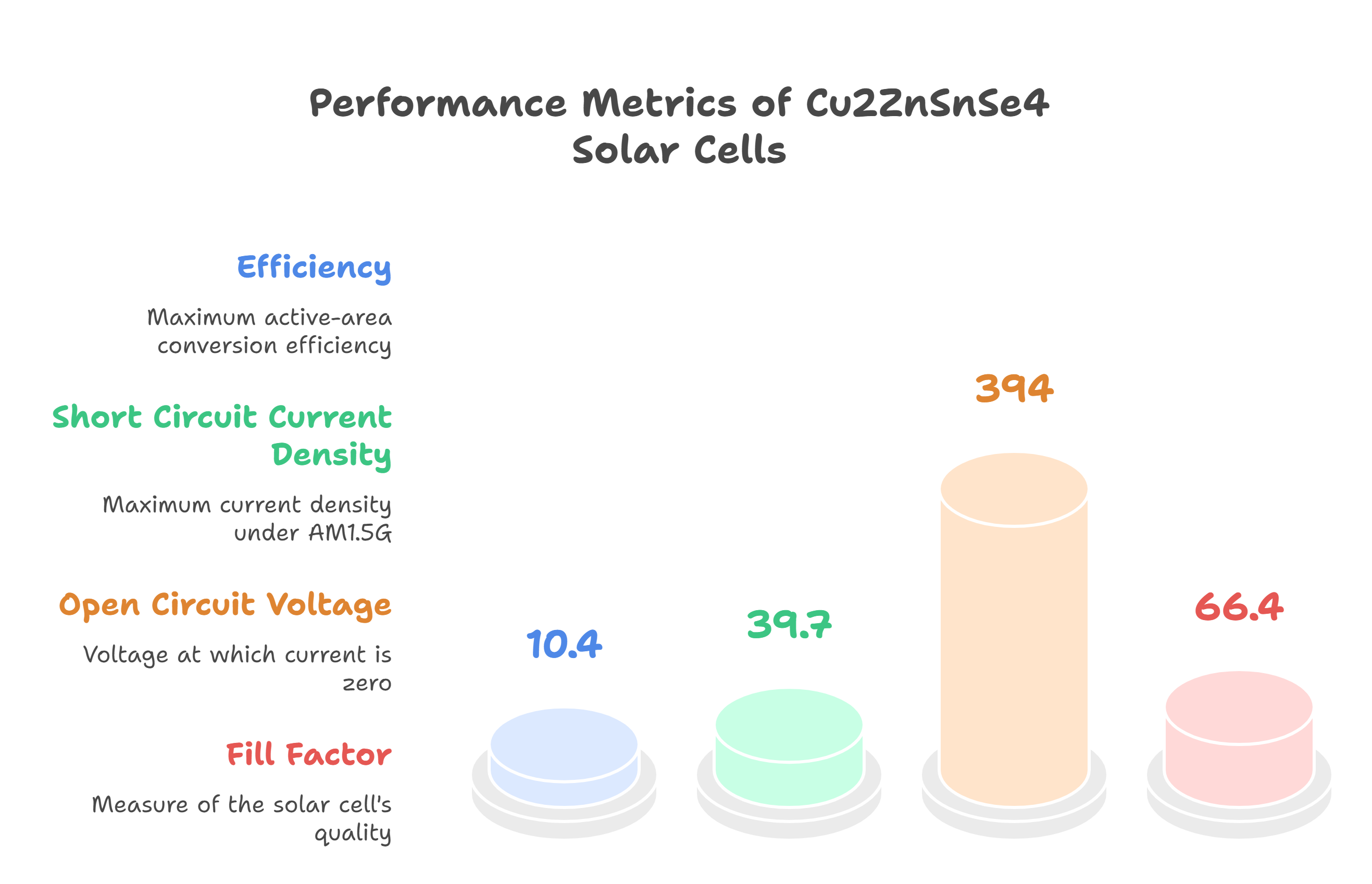
Physical and electrical characterization of high-performance Cu2ZnSnSe4based thin film solar cells
We report on the electrical, optical and physical properties of Cu2ZnSnSe4solar cells using an absorber layer fabricated by selenization of sputtered Cu, Zn and Cu10Sn90multilayers. A maximum active-area conversion efficiency of 10.4% under AM1.5G was measured with a maximum short circuit current density of 39.7 mA/cm2, an open circuit voltage of 394 mV and a fill factor of 66.4%. We perform electrical and optical characterization using photoluminescence spectroscopy, external quantum efficiency, current-voltage and admittance versus temperature measurements in order to derive information

Reduce Computing Complexity of Deep Neural Networks Through Weight Scaling
Large deep neural network (DNN) models are computation and memory intensive, which limits their deployment especially on edge devices. Therefore, pruning, quantization, data sparsity and data reuse have been applied to DNNs to reduce memory and computation complexity at the expense of some accuracy loss. The reduction in the bit-precision results in loss of information, and the aggressive bit-width reduction could result in noticeable accuracy loss. This paper introduces Scaling-Weight-based Convolution (SWC) technique to reduce the DNN model size and the complexity and number of arithmetic
Full Connectivity Driven K-LEACH Algorithm for Efficient Data Forwarding in Wireless Sensor Networks
Due to the usage of Internet in everything in our life, our environment is transformed into digital society, in which everything can be accessed from anywhere. This is the main concept of Internet of Things (IoT), which consists of intelligent devices connected together without location limitation. These devices can be sensors and actuators, which are used in environmental monitoring, home automation, disaster management and more. This is the definition of Wireless Sensor Network (WSN), which is considered a subset from IoT environment. WSN consists of hundreds of nodes spread in different