
Software and Communications

Improving the Performance of Semantic Text Similarity Tasks on Short Text Pairs
Training semantic similarity model to detect duplicate text pairs is a challenging task as almost all of datasets are imbalanced, by data nature positive samples are fewer than negative samples, this issue can easily lead to model bias. Using traditional pairwise loss functions like pairwise binary cross entropy or Contrastive loss on imbalanced data may lead to model bias, however triplet loss showed improved performance compared to other loss functions. In triplet loss-based models data is fed to the model as follow: Anchor sentence, positive sentence and negative sentence. The original data
Using Knowledge Graph Embeddings in Embedding Based Recommender Systems
This paper proposes using entity2rec [1] which utilizes knowledge graph-based embeddings (node2vec) instead of traditional embedding layers in embedding based recommender systems. This opens the door to increasing the accuracy of some of the most implemented recommender systems running in production in many companies by just replacing the traditional embedding layer with node2vec graph embedding without the risk of completely migrating to newer SOTA systems and risking unexpected performance issues. Also, Graph embeddings will be able to incorporate user and item features which can help in
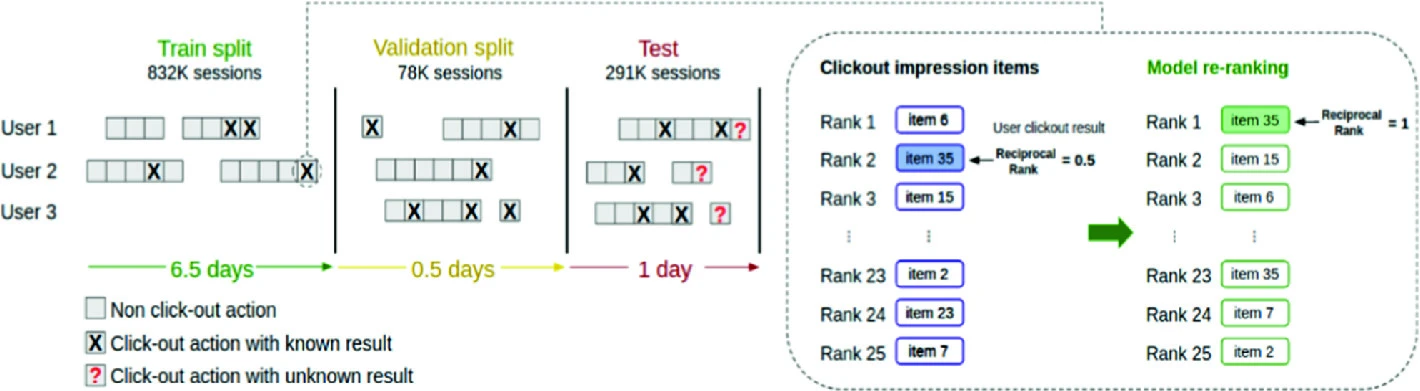
Recommendations on Streaming Data: E-Tourism Event Stream Processing Recommender System
The Association for Computing Machinery ACM recommendation systems challenge (ACM RecSys) [1] released an e-tourism dataset for the first time in 2019. Challenge shared hotel booking sessions from trivago website asking to rank the hotels list for the users. Better ranking should achieve higher click out rate. In this context, Trivago dataset is very important for e-tourism recommendation systems domain research and industry as well. In this paper, description for dataset characteristics and proposal for a session-based recommender system in addition to a comparison of several baseline

Dynamic Modeling and Identification of the COVID-19 Stochastic Dispersion
In this work, the stochastic dispersion of novel coronavirus disease 2019 (COVID-19) at the borders between France and Italy has been considered using a multi-input multi-output stochastic model. The physical effects of wind, temperature and altitude have been investigated as these factors and physical relationships are stochastic in nature. Stochastic terms have also been included to take into account the turbulence effect, and the r and om nature of the above physical parameters considered. Then, a method is proposed to identify the developed model's order and parameters. The actual data has
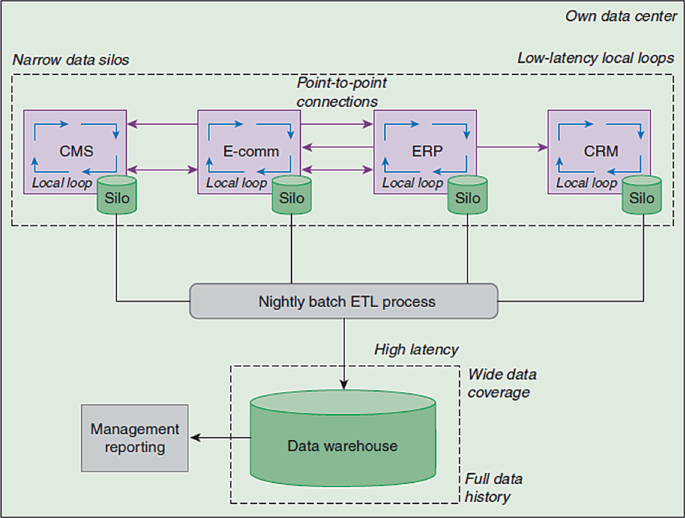
Walk Through Event Stream Processing Architecture, Use Cases and Frameworks Survey
Nowadays events stream processing is one of the top demanding field(s) because of the business urgent need for ongoing real time analytics & decisions. Most business domains avail huge amount of data aiming to make use of each data point efficiently. Corporate(s) have a cloud of events vary from internal business transactions, social media feeds, IoT devices logs,.. etc. In this paper we would discuss state of the art event stream processing technologies using cloud of events by summarizing event stream processing definition, data flow architectures, common use cases, frameworks and
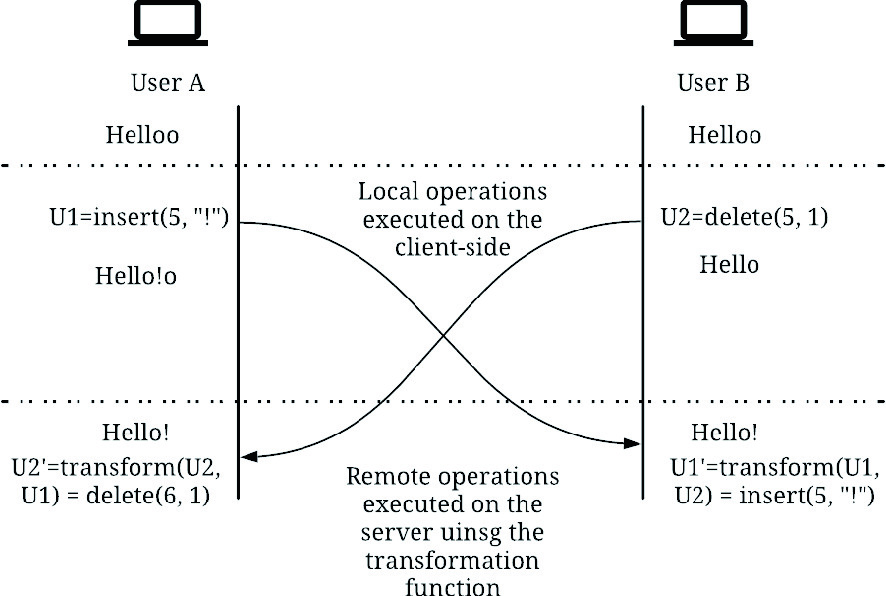
A Survey of Concurrency Control Algorithms in Collaborative Applications
Collaborative applications are becoming more prevalent for a variety of reasons, most important of which is the increased interest in remote work. In addition to adapting the business processes to a remote setting, designers of collaborative software have to decide on how their software can be used collaboratively. This paper discusses the two main technologies used to enable network-based real- or near-real-time collaborative software, namely Operational Transformation and Conflict-free Replicated Data Types. Recent developments in each technology are discussed, as well as a brief overview of
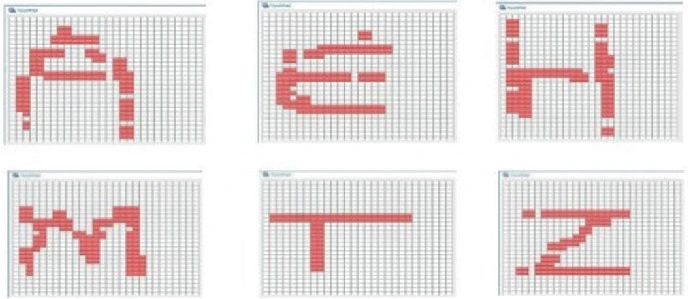
Handwriting Letter Recognition on the Steering Wheel Switches
Automotive steering wheel switches technologies are evolving to give easy access to the several interior or exterior functions. This is worth a deep analysis for the current trends in order not to become unintuitive for the driver due to the increasing number of buttons. Through different technologies particularly the capacitive ones, range of innovative solutions have been developed like reconfigurable buttons on the steering wheel to offer commanding several functions twice or triple the number of allocated push buttons. In this paper, we address the problem in a different freely way to
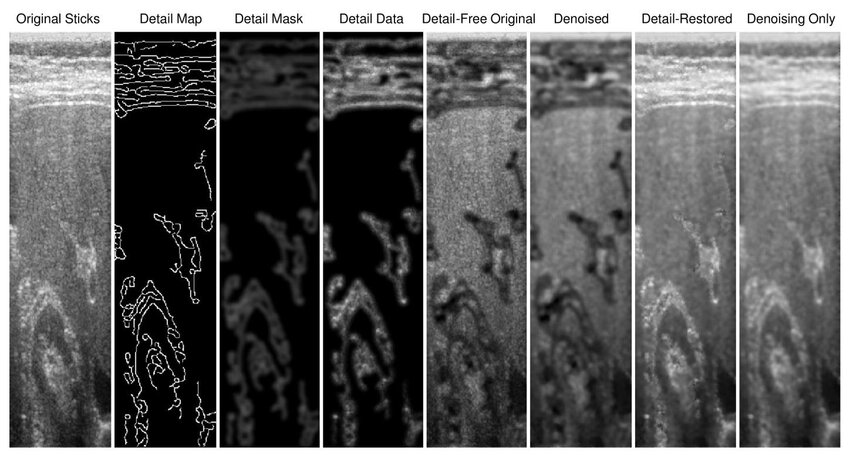
Edge Detail Preservation Technique for Enhancing Speckle Reduction Filtering Performance in Medical Ultrasound Imaging
—Ultrasound imaging is a unique medical imaging modality due to its clinical versatility, manageable biological effects, and low cost. However, a significant limitation of ultrasound imaging is the noisy appearance of its images due to speckle noise, which reduces image quality and hence makes diagnosis more challenging. Consequently, this problem received interest from many research groups and many methods have been proposed for speckle suppression using various filtering techniques. The common problem with such methods is that they tend to distort the edge detail content within the image and
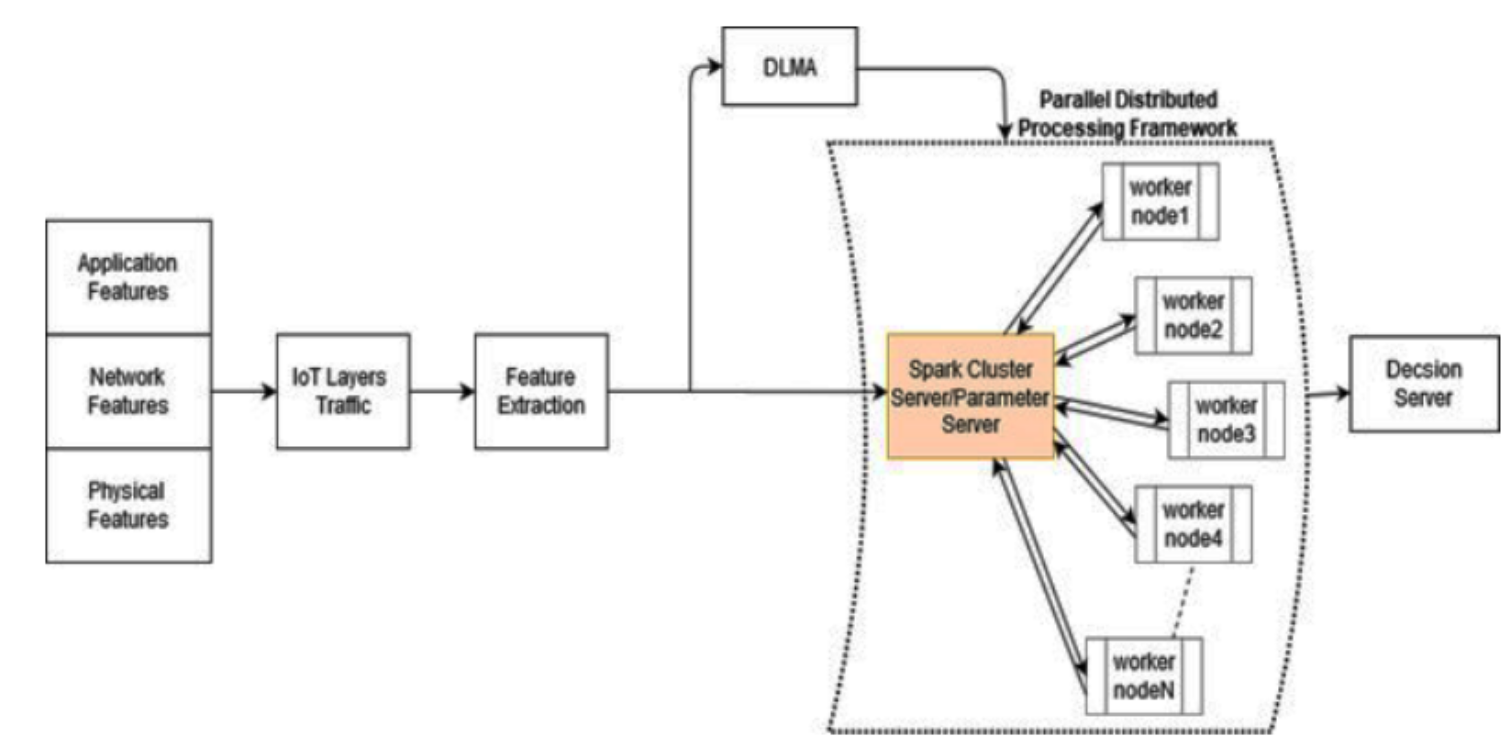
Cross-Layer Distributed Attack Detection Model for the IoT
The security of IoT that is based on layered approaches has shortcomings such as the redundancy, inflexibility, and inefficiently of security solutions. There are many harmful attacks in IoT networks such as DoS and DDoS attacks, which can compromise the IoT architecture in all layers. Consequently, cross layer approach is proposed as an effective and practical security defending mechanism. Cross-layer distributed attack detection model (CLDAD) is proposed to enhance security solutions for IoT environments. CLDAD presents a general detection method of DDoS in sensing layer, network layer, and
Ibn Sina: A patient privacy-preserving authentication protocol in medical internet of things
The prosperous advancement in Medical Internet of Things (MIoT) technologies has hastened the development of healthcare systems. MIoT improves the traditional medical facilities through periodically monitor of patient's health records. Electronic Medical Records (EMRs) are sensitive private data and needs efficient secure and private schemes that interchange these EMRs between healthcare providers and patients. Most of the current privacy preserving schemes do not provide the desired privacy level and suffer from computation and communication overheads. The length of an IDentity-based Strong