
Software and Communications
Customer Churn Prediction Using Apriori Algorithm and Ensemble Learning
Customer churn poses a formidable challenge within the Telecom industry, as it can result in significant revenue losses. In this research, we conducted an extensive study aimed at developing a viable customer churn prediction method. Our method utilizes the Apriori algorithm's strength to identify the key causes of customer churn. In the pursuit of this goal, we utilized multiple machine learning predictive models. All of which were developed from the insights gleaned from the Apriori algorithm's feature extraction for churning customers. This extensive analysis encompassed a spectrum of

A Comparative Analysis of Time Series Transformers and Alternative Deep Learning Models for SSVEP Classification
Steady State Visually Evoked Potentials (SSVEPs) are intrinsic responses to specific visual stimulus frequencies. When the retina is activated by a frequency ranging from 3.5 to 75 Hz, the brain produces electrical activity at the same frequency as the visual signal, or its multiples. Identifying the preferred frequencies of neurocortical dynamic processes is a benefit of SSVEPs. However, the time consumed during calibration sessions limits the number of training trials and gives rise to visual fatigue since there is significant human variation across and within individuals over time, which

Gender Detection from Hand Palm Images: A PySpark-Driven Approach with VGG19 Feature Extraction and MLP Classification
This paper presents a comprehensive methodology for gender detection using hand palm images, leveraging image processing techniques and PySpark for scalable and efficient processing. The approach encompasses a meticulous image preprocessing pipeline, incorporating essential stages like grayscale conversion, the application ofthe Difference of Gaussians (DoG) filter, and adaptive histogram equalization. This approach not only refmes image features but also ensures scalability, accommodating large datasets seamlessly. After preprocessing of hand images, the VGG19 model is employed as a powerful
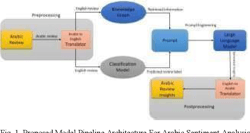
Sentiment Analysis for Arabic Product Reviews using LLMs and Knowledge Graphs
The exploration of sentiment analysis in multilingual contexts, particularly through the integration of deep learning techniques and knowledge graphs, represents a significant advance in language processing research. This study specifically concentrates on the Arabic language, addressing the challenges presented by its morphological complexity. While the primary focus is Arabic, the research also includes a comprehensive review of related work in other languages such as Bangla and Chinese. This contextualizes the challenges and solutions found in Arabic sentiment analysis within a broader

Comparative Analysis of a Generalized Heart Localization Model: Assessing Its Efficacy Against Specialized Models
Heart localization holds significant importance in the process of the diagnosis and treatment of heart diseases. Additionally, it plays an important role in planning the cardiac scanning protocol. This research focuses on heart localization by employing the multi-label classification task with the utilization of RES-Net50. The primary objective is to predict the slices containing the heart and determine its endpoint. To ensure high-quality data, we implement filtering techniques and perform up-sampling during the pre-processing stage. Two experiments were conducted to assess different

Apache Spark Powered: Enhancing Network Intrusion Detection System Using Random Forest
The increasing sophistication of cyber attacks necessitates effective intrusion detection systems. We propose a novel intrusion detection method integrating deep learning with big data management using Apache Spark. Leveraging the comprehensive CSE-CIC-IDS2018 dataset, we apply extensive data preprocessing, including handling missing and unreliable values, duplicates, and redundant columns. In addition, implementation of a Random Forest based feature importance approach is derived to prioritize the most impactful Features. Furthermore, stratified k-fold cross-validation is used for a model
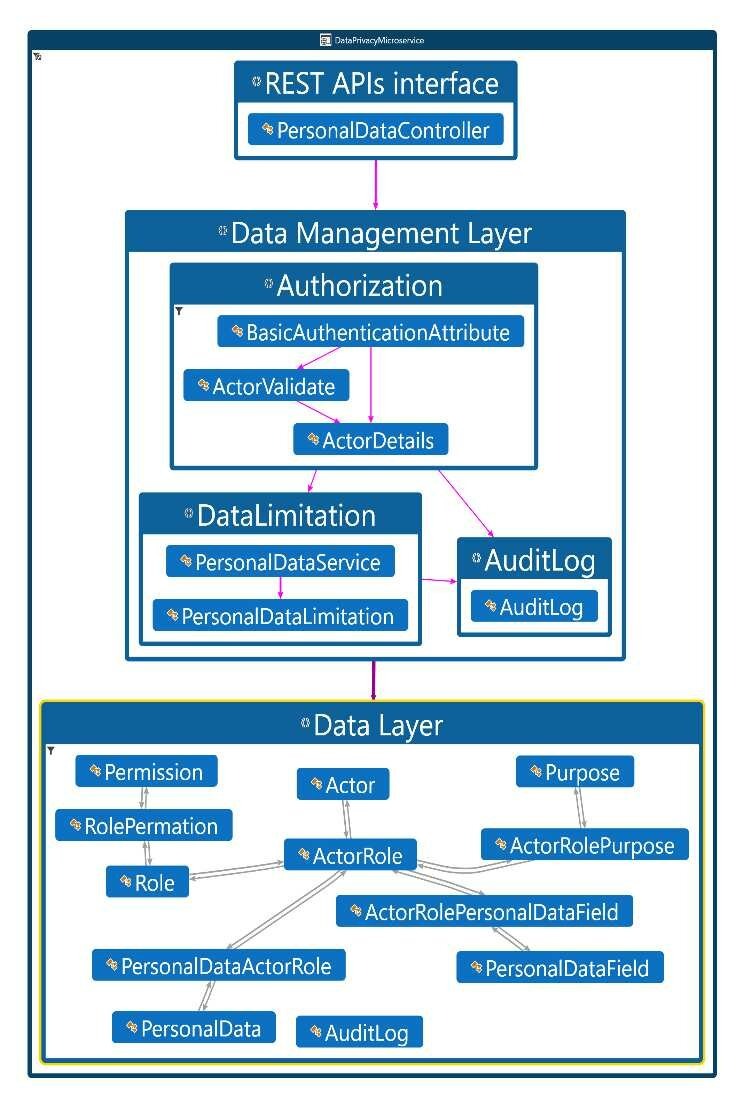
Privacy by Design: A Microservices-Based Software Architecture Approach
Data privacy regulations have increased significantly recently. As a result, privacy by design (PbD) has become a critical consideration for enterprises that handle personal data. PbD is no longer a plain principle. Rather than that, the General Data Protection Regulation (GDPR) addresses PbD as a required legal requirement for controllers who may face fines for non-compliance with the GDPR. In this paper, we propose a practical solution, 'PbD Microservice,' that can help organizations to achieve privacy regulatory compliance. We will focus on GDPR, one of the most important regulations that
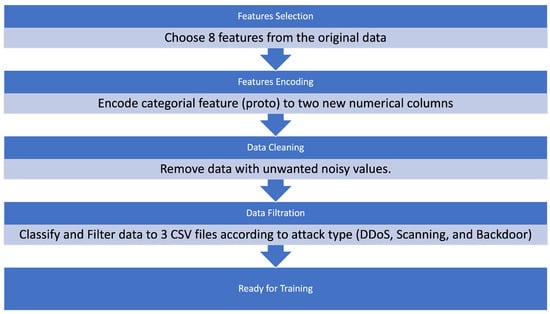
Anomaly Detection of Zero-Day Attacks Based on CNN and Regularization Techniques
The rapid development of cyberattacks in the field of the Internet of things (IoT) introduces new security challenges regarding zero-day attacks. Intrusion-detection systems (IDS) are usually trained on specific attacks to protect the IoT application, but the attacks that are yet unknown for IDS (i.e., zero-day attacks) still represent challenges and concerns regarding users’ data privacy and security in those applications. Anomaly-detection methods usually depend on machine learning (ML)-based methods. Under the ML umbrella are classical ML-based methods, which are known to have low
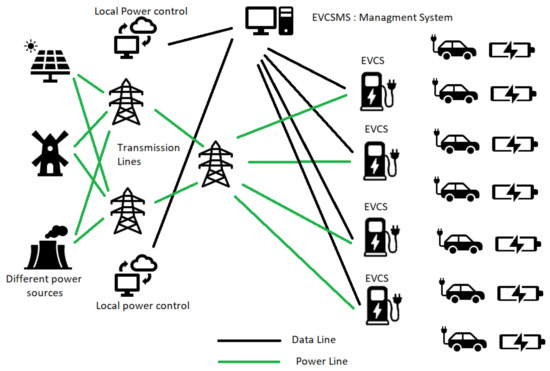
Intrusion Detection for Electric Vehicle Charging Systems (EVCS)
The market for Electric Vehicles (EVs) has expanded tremendously as seen in the recent Conference of the Parties 27 (COP27) held at Sharm El Sheikh, Egypt in November 2022. This needs the creation of an ecosystem that is user-friendly and secure. Internet-connected Electric Vehicle Charging Stations (EVCSs) provide a rich user experience and add-on services. Eventually, the EVCSs are connected to a management system, which is the Electric Vehicle Charging Station Management System (EVCSMS). Attacking the EVCS ecosystem remotely via cyberattacks is rising at the same rate as physical attacks
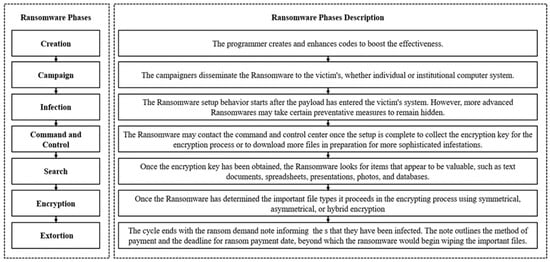
A New Scheme for Ransomware Classification and Clustering Using Static Features
Ransomware is a strain of malware that disables access to the user’s resources after infiltrating a victim’s system. Ransomware is one of the most dangerous malware organizations face by blocking data access or publishing private data over the internet. The major challenge of any entity is how to decrypt the files encrypted by ransomware. Ransomware’s binary analysis can provide a means to characterize the relationships between different features used by ransomware families to track the ransomware encryption mechanism routine. In this paper, we compare the different ransomware detection