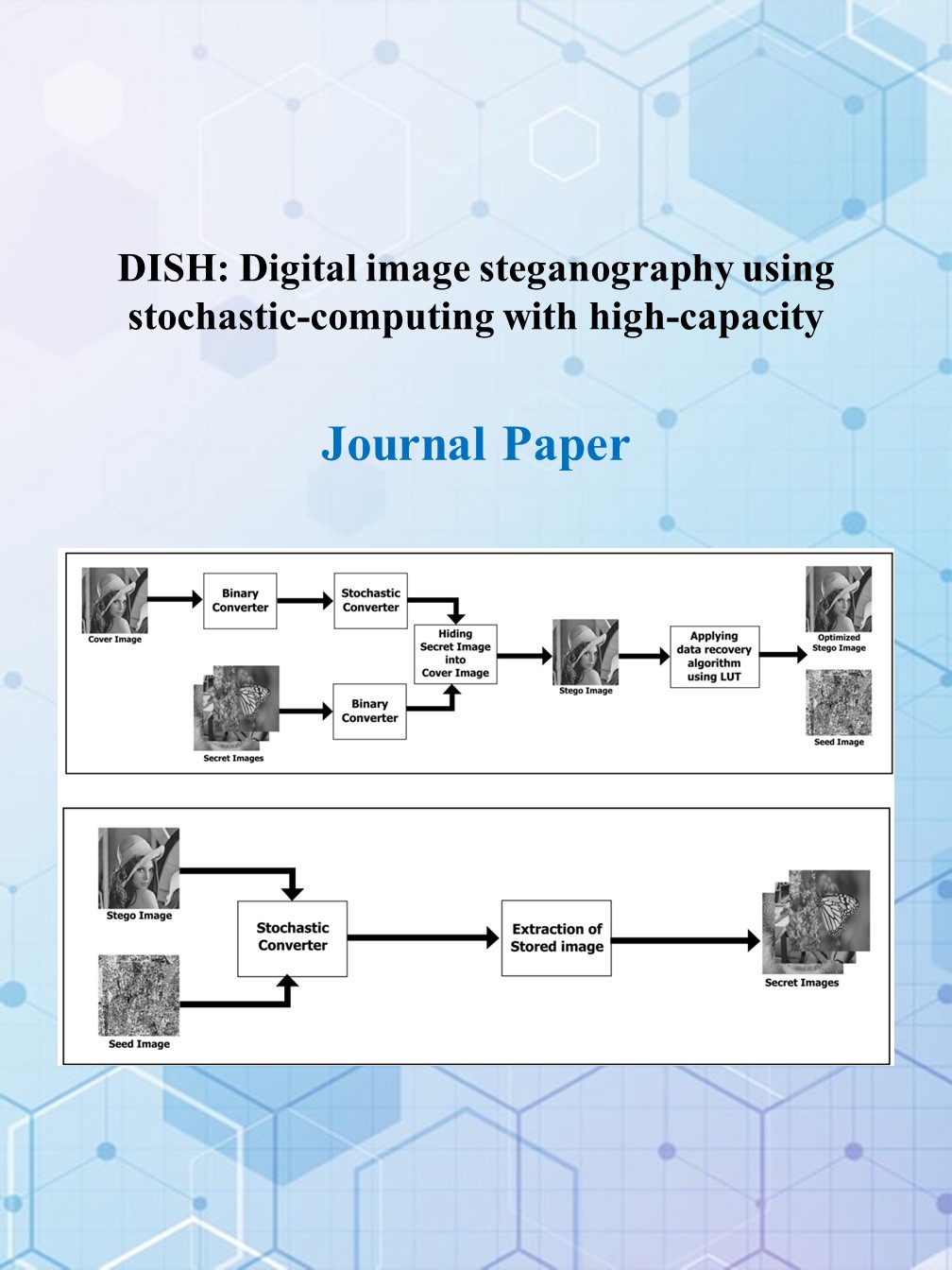
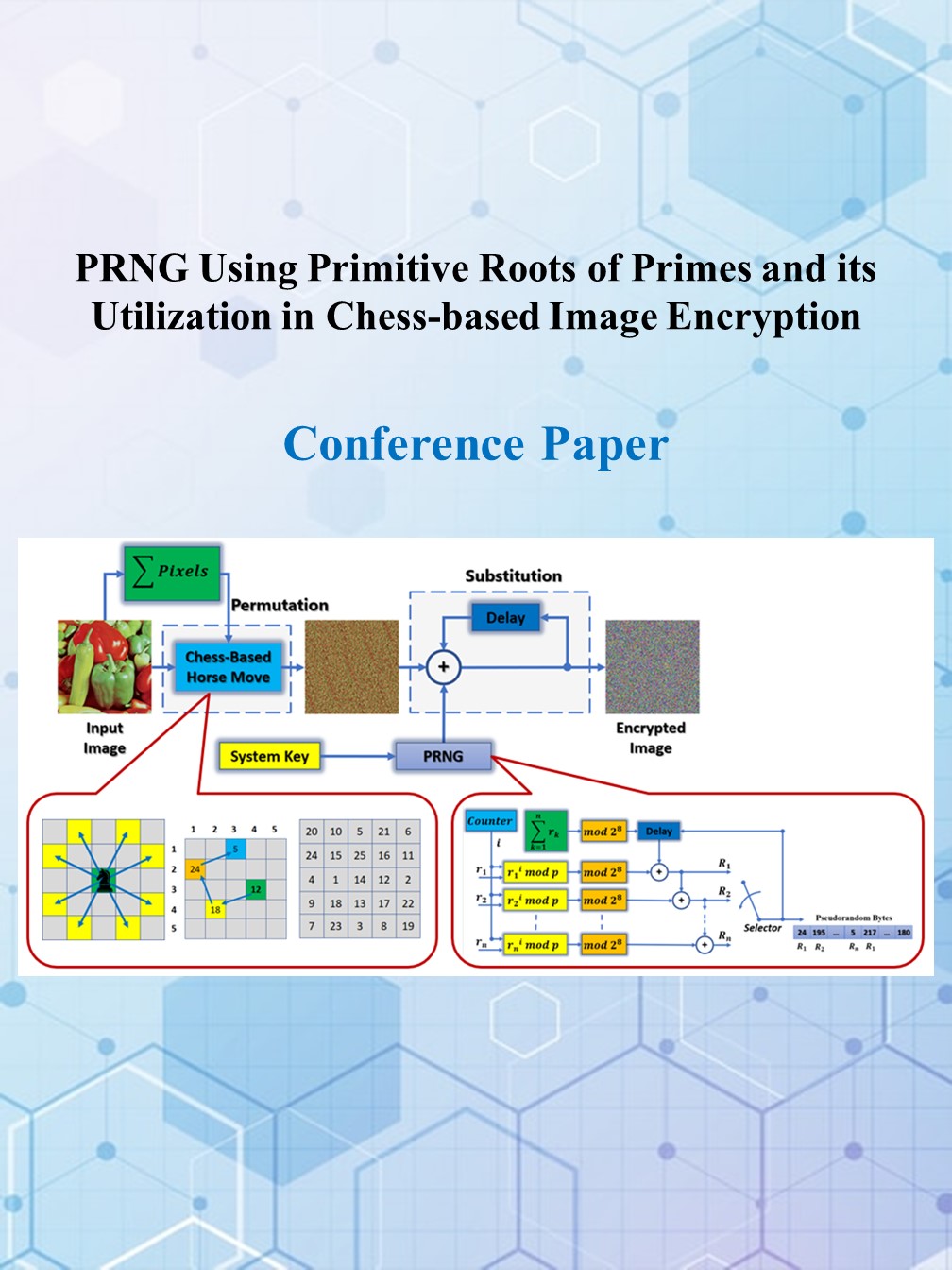
Software Algorithms and Hardware Implementations of Information Security Using Number Theory and Chaotic Systems
The project aims at proposing novel software algorithms for information security and their hardware implementations. The algorithms will utilize different methods based on number theory and chaos theory. Cryptography and information hiding systems will be developed for different media data types such as text, image, audio and video. The project will investigate different classes of symmetric/asymmetric and stream/block ciphers. In addition, it will explore both steganography and watermarking in spatial and frequency domains. The proposed information security solutions will be evaluated using standard performance measures. The project targets achieving technical outcomes that include hardware prototypes and a website.
Outcomes Highlights
The following videos showcase the output predictions using a simplified H.264 system integration. These videos offer a clear summary of the tested video sequences, with different QP values used to assess the system's performance. They not only compare the first frame of each sequence before and after processing but also provide links to the full output videos, displaying all 300 decoded frames. This analysis highlights the system’s robustness in preserving visual quality while achieving efficient video compression, affirming its suitability for applications requiring both high efficiency and quality retention. Moreover, the videos demonstrate minimal quality loss throughout the encoding and decoding processes, emphasizing the effectiveness of the simplified H.264 system.
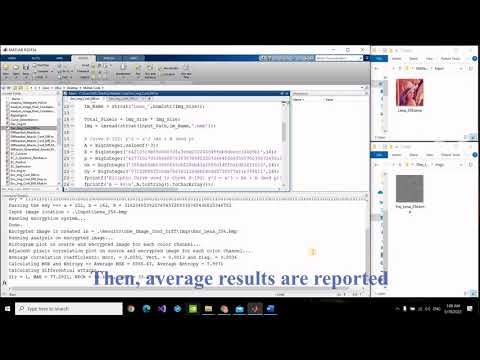
This video demonstrates the use of elliptic curves in designing a PRNG and shows the execution steps in MATLAB for an image encryption system that utilizes the designed PRNG-based-EC. In the beginning, the input image is shown and different parts of the MATLAB GUI are described. Then the histogram analysis is shown, followed by image pixel correlation in the horizontal, vertical, and diagonal directions. Finally, the differential attacks are performed and the results are printed in the MATLAB window.
This video shows the encrypted Foreman sequence using the Selective Encryption System. The SES is integrated inside the H.264 video compression where important syntax elements are selected for encryption such as the Intra Prediction Mode (IPM), Non Zero Quantized Coefficients (NZ QC), and the Motion Vector Difference (MVD). The video shows the encryption result using Test Case 7 which represents IPM, Sign of NZ-QC, and Sign of MVD.
Information Security 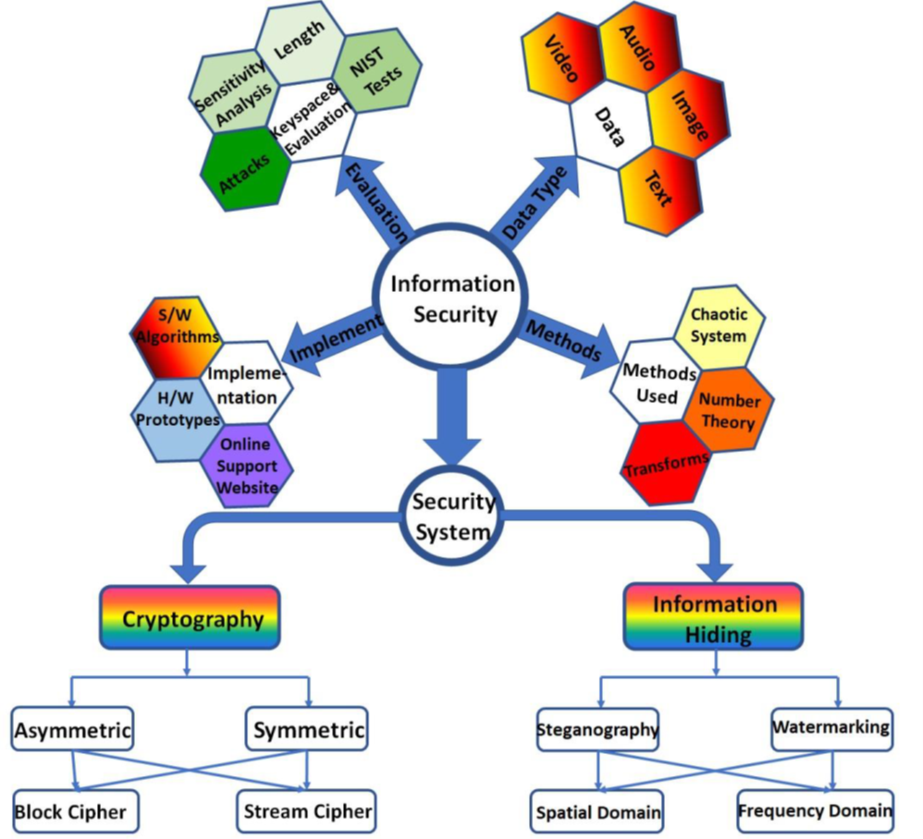
Software Algorithms and Hardware Implementations of sing Number Theory and Chaotic Systems.
Funded by: Science, Technology & Innovation Funding Authority (STIFA) Grant #45631.
 |
 |
 |
 |
|
PI |
Co-PI |
Researcher |
Researcher |
 |
 |
 |
 |
|
Researcher |
Researcher |
Reasearcher |
Reasearcher |
 |
 |
 |
|
|
Researcher |
Researcher |
Researcher |