Analysis and Guidelines for Different Designs of Pseudo Random Number Generators
Analysis and Guidelines for Different Designs of Pseudo Random Number Generators
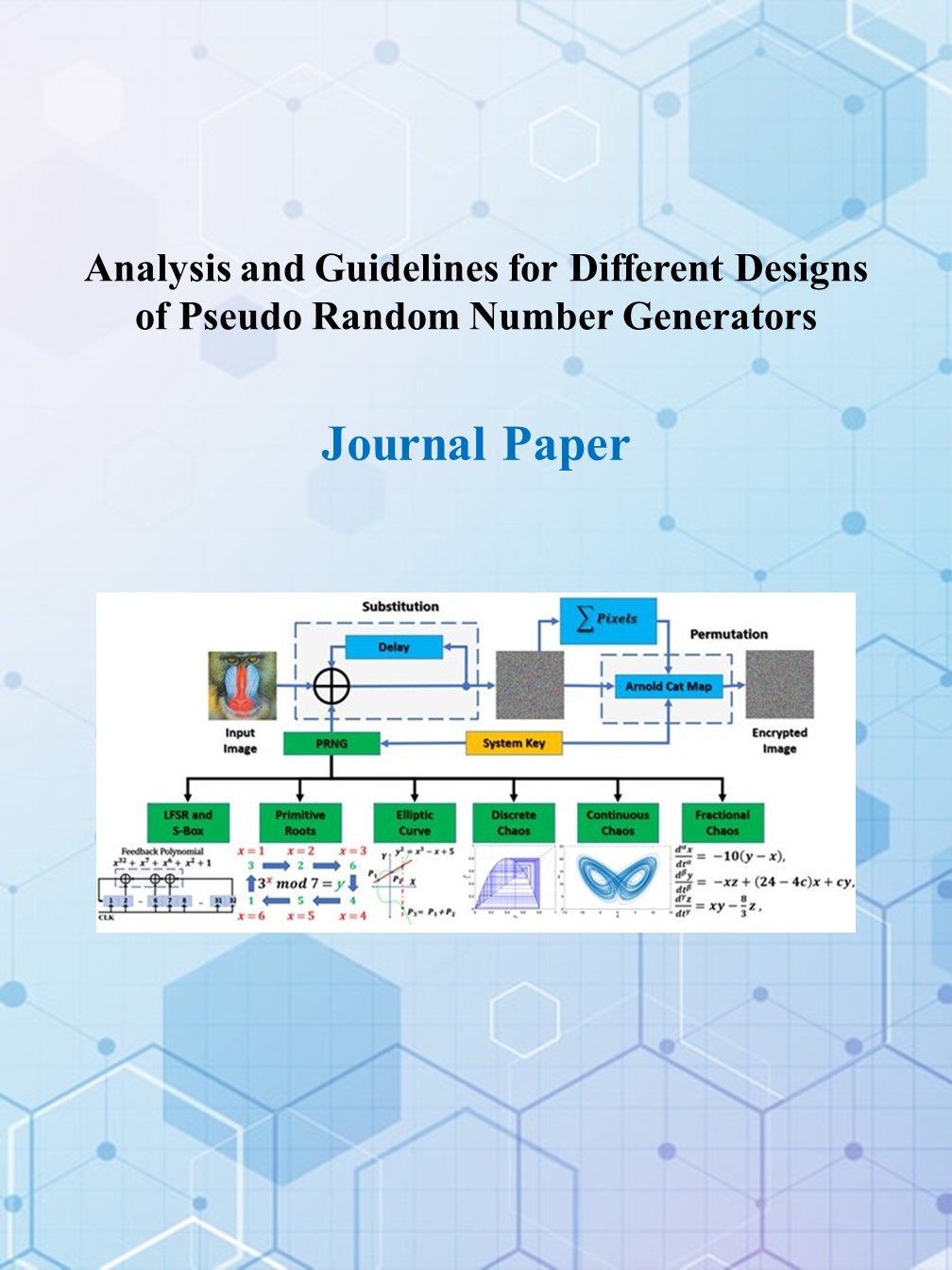
The design of an efficient Pseudo Random Number Generator (PRNG) with good randomness properties is an important research topic because it is a core component in many applications. Based on an extensive study of most PRNGs in the past few decades, this paper categorizes six distinct design scenarios under two primary groups: non-chaotic and chaotic generators. The non-chaotic group comprises Linear Feedback Shift Registers (LFSR) with S-Boxes, primitive roots, and elliptic curves, whereas the chaotic group encompasses discrete, continuous, and fractional-order chaotic generators. This paper delves into the related scientific summaries, equations, flowcharts, and designs with necessary recommendations for each PRNG scenario. Even though the focus is on the basic design characteristics that provide simple, functional and secure PRNGs, it is possible to enhance those designs for additional features and improved efficiency. Simulation outcomes and system key configurations, which produce long random sequences, are also presented and evaluated using leading criteria. The evaluation criteria include the National Institute of Standards and Technology (NIST) SP-800-22 test suite, TestU01 randomness tests, histogram, entropy, autocorrelation, and cross-correlation. Furthermore, key space, key sensitivity, and bit rate indicate that all designed examples meet international standards with high quality. The presented PRNGs are compared and integrated into an image encryption system. Although each PRNG design scenario can have a different key space, simple designs with fixed-length system keys are chosen for the sake of proper comparisons. Statistical and security assessments of the encryption system demonstrate that the PRNGs are cryptographically secure.
