
Software and Communications
Integrating Smart Contracts with WDNs Framework for Energy Management and Secure Transactions
The management of energy consumption and payment transactions using a secure, decentralized energy system framework is essential in the water distribution network (WDN). The water energy market, in which energy may be transformed into a digital asset that is potentially monitored, trackable and tradable, might greatly benefit from the deployment of blockchain technology. This is because the blockchain has transaction privacy, decentralization, security, and immutability features. Furthermore, using blockchain smart contracts enables energy market management operations such as consumers
Energy Optimization and Cost Reduction in Water Distribution Networks
Since the majority of energy consumed by water supply systems is used in transporting and distributing water, in addition to the energy required to pump the water from its sources, energy consumption is significantly associated with the water demand. Several studies have been carried out to optimize pump operations to achieve appropriate pressure and reduce the energy associated with controlling water levels in storage facilities. In this paper, we develop an optimization and decision support technique for a Water Distribution Network (WDN) that considers energy efficiency by limiting the
A Lightweight Image Encryption Scheme Using DNA Coding and Chaos
Protecting transmitted multimedia data such as images is a significant concern. This work proposes an encryption algorithm for greyscale images using a Pseudo-Random Number Generator (PRNG), DNA coding, and pixel sum. The proposed approach is implemented on a Genesys 2 FPGA using minimal hardware resources and can operate at a maximum frequency of 110.8 MHz. In addition, several performance evaluation tests are conducted for multiple images, including statistical analysis of the encrypted image, keyspace analysis, and differential attack analysis. The system is compared to recent works with
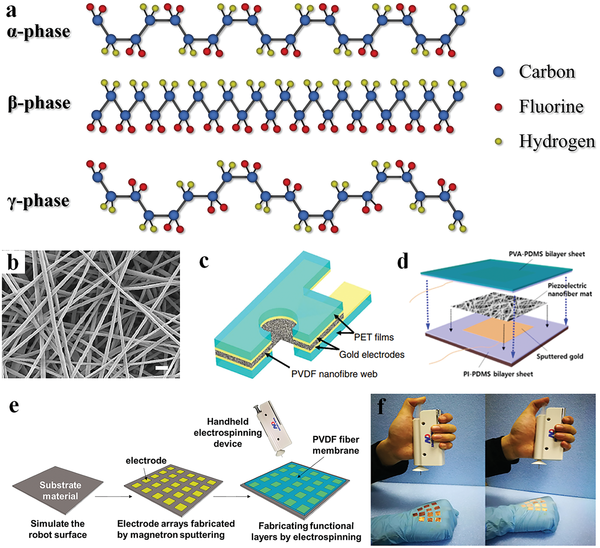
Improvement of piezoresistive pressure sensor using zig-zag shaped and PVDF material
Due to a wide range of applications in the biomedical industry, the need for flexible and wearable sensors is growing every day. A pressure sensor generates a signal based on the applied pressure. Sensors have become an integral component of our daily lives, from personal gadgets to industrial machinery. The identification of the low signal from the body necessitates the use of particularly sensitive sensors. The development of a pressure sensor that can transform the maximum input signal into an electrical output is critical. In this paper, zig-zag piezoresistors on a square diaphragm were
Developing Smart Control Platoon Algorithm for Secure VANET Environment
A vehicular ad hoc network (VANET) is a part of smart transportation. As a result of the vehicles being able to communicate with one another and share sensitive information, it is necessary to have an environment that can be trusted. Vehicles are clustered into platoons to ensure the secure transfer of information between them and select the platoon head of each platoon to control the vehicles. This paper proposes a smart control platoon system employing local and global trust schemes among vehicles in order to establish a secure environment. The platoon head calculates the local trust in each
Developing an Ultra-Dense Optical Frequency Comb Using an Integrated MZM and SPM Schemes in HNLF
Optical frequency comb (OFC) is a broad spec-trum comprised of closely spaced equidistant narrow lines. The generation of OFC is based on several nonlinear effects in highly nonlinear fiber (HNLF), which is employed to produce the repetitive frequencies. This work investigates the usage of cascaded Mach-Zehnder modulators (MZM) and self-phase modulation (SPM) in HNLF as effective spectrum broadening and comb generation techniques. Several parameters have been investigated in order to improve the output spectrum of the comb generation system. The parameters being investigated in this research
Real-time facial emotion recognition model based on kernel autoencoder and convolutional neural network for autism children
Autism Spectrum Disorder (ASD) is a neurodevelopmental disorder that is characterized by abnormalities in the brain, leading to difficulties in social interaction and communication, as well as learning and attention. Early diagnosis of ASD is challenging as it mainly relies on detecting abnormalities in brain function, which may not be evident in the early stages of the disorder. Facial expression analysis has shown promise as an alternative and efficient solution for early diagnosis of ASD, as children with ASD often exhibit distinctive patterns that differentiate them from typically
Wireless Optogenetics Visual Cortical Prosthesis Control System
This research paper presents the wireless data and power transfer system for optogenetics visual cortical prosthesis. The system uses the inductive coupling power transfer and 2.4GHz Bluetooth 4.0 data transfer. This system contains two hardware parts: the external headset consists of power and data transmitters, image capture, and image processing units; the subcutaneous implant PCB consists of power and data receiver and the control unit. We also present the relative image processing method for this system. The whole system could power and control the optogenetic neural stimulus of the

Integration of Federated Machine Learning in Smart Metering Systems
The applications of Federated Learning are many, and they can be used to predict electricity consumption and, at the same time, enable smart meters to collaboratively learn a shared model while keeping all their data locally in their own private database. With this approach, the central model will see more data and will work better to predict electricity consumption more accurately than the models trained on only one local Dataset. The planning of infrastructure, grid operation, and budgeting all depend on accurate load forecasting. As a result, this paper suggests federated learning for load
Realistic Wireless Smart-Meter Network Optimization Using Composite RPL Metric
In smart metering applications, transferring and collecting data within delay constraints is crucial. IoT devices are usually resource-constrained and need reliable and energy-efficient routing protocol. Furthermore, meters deployed in lossy networks often lead to packet loss and congestion. In smart grid communication, low latency and low energy consumption are usually the main system targets. Considering these constraints, we propose an enhancement in RPL to ensure link reliability as well as low latency. We refer to the proposed new additive composite metric as Delay-Aware RPL (DA-RPL)