
The purpose of this paper is to discuss the Blockchain technology adoption opportunities and challenges in Egypt. The Blockchain technology is evolving with diverse benefits worldwide. Each country has its own motives and barriers to adopt the Blockchain. Therefore, it is crucial to understand the benefits and the challenges of adopting the Blockchain technology from Egyptian prospective. The Egyptian supply chain management, real estate, banking and finance, and the governmental services are discussed in this research work as examples of potential sectors for the Blockchain adoption
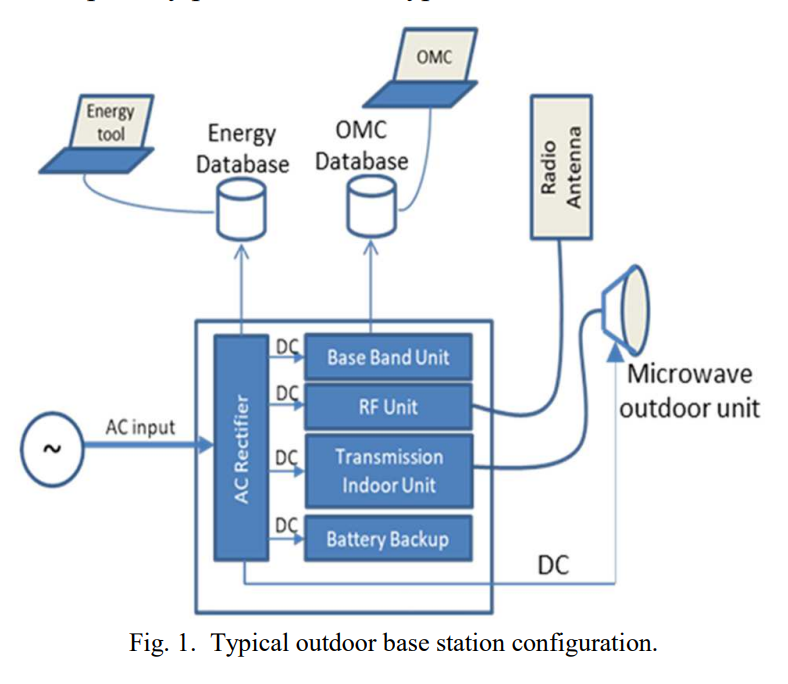
Mobile operators are facing strong challenges regarding the environmental impact of their operations. The International Telecommunications Union (ITU) considered energy consumption as the prime source of Carbon dioxide (CO2) emissions for the whole Information and Communications Technology (ICT) sectors. ITU encouraged all ICT sectors to commit their efforts in order to control their energy consumption and consider renewable energy sources. By the year 2050, CO2 emissions should be fully neutralized as per the Paris climate agreement. The energy consumption of the Radio Access Network (RAN)
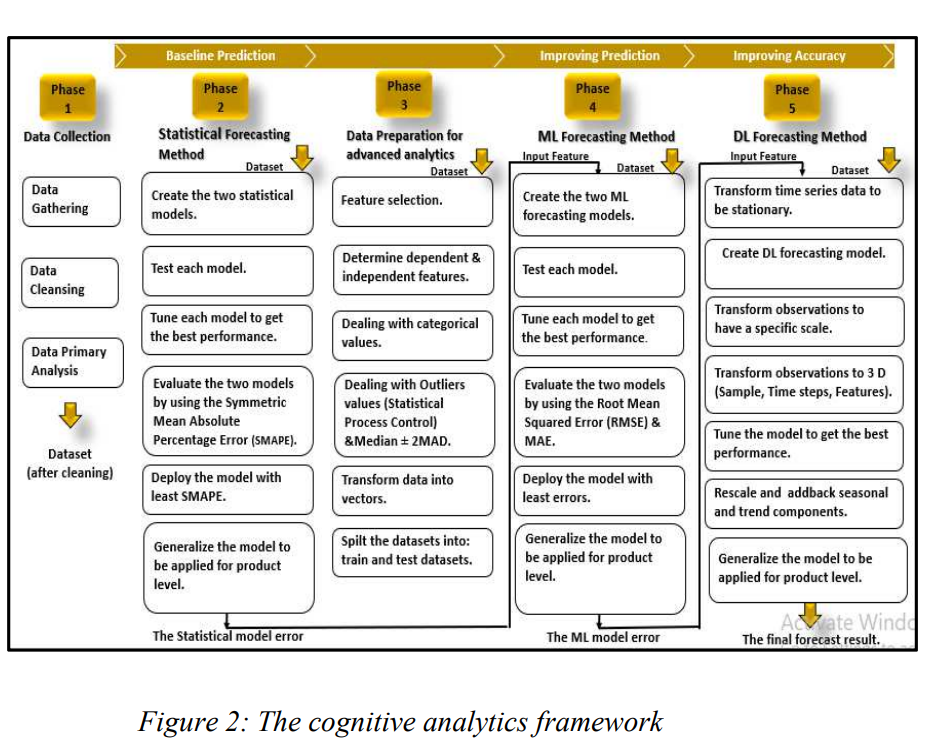
accurate prediction of sales data is an important and challenging problem in the retail industry. However, due to the diversity of data types, it is difficult for traditional time series prediction models to generate good prediction results for different types of data. This research develops a cognitive analytic framework to help transform retailers from the reactive environment to automated continuously learning environment utilizing the power of AI technology in predicting future sales with high accuracy. It proposes a multi-stage prediction framework based on the integration of Statistical
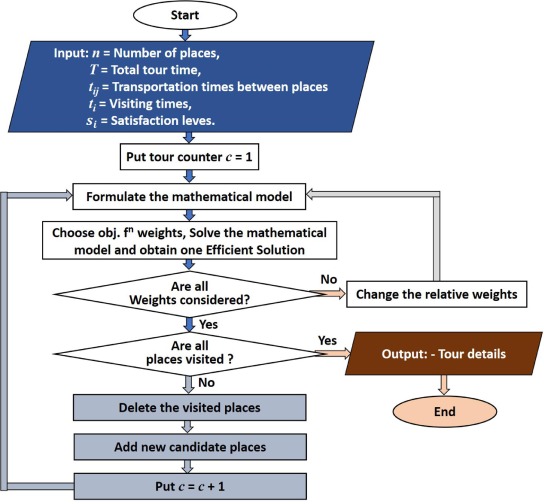
This chapter proposes a novel binary version of recently developed Gaining-Sharing knowledge-based optimization algorithm (GSK) to solve binary optimization problems. GSK algorithm is based on the concept of how humans acquire and share knowledge during their life span. Binary version of GSK named novel binary Gaining-Sharing knowledge-based optimization algorithm (BGSK) depends on mainly two binary stages: binary junior gaining sharing stage and binary senior gaining sharing stage with knowledge factor 1. These two stages enable BGSK for exploring and exploitation of the search space
Big Data Stream processing engines such as Apache Flink use windowing techniques to handle unbounded streams of events. Gathering all pertinent input within a window is crucial for event-time windowing since it affects how accurate results are. A significant part of this process is played by watermarks, which are unique timestamps that show the passage of events in time. However, the current watermark generation method in Apache Flink, which works at the level of the input stream, tends to favor faster sub-streams, resulting in dropped events from slower sub-streams. In our analysis, we found
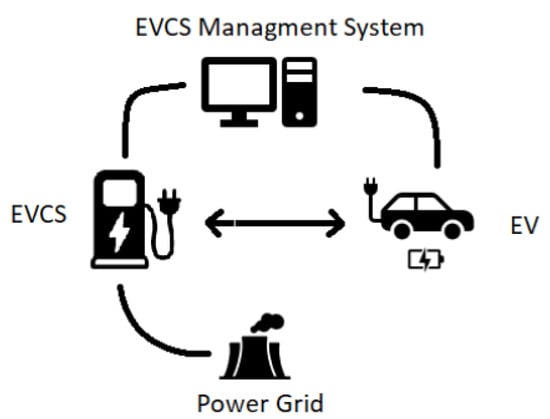
The demand for electric vehicles (EVs) is growing rapidly. This requires an ecosystem that meets the user’s needs while preserving security. The rich data obtained from electric vehicle stations are powered by the Internet of Things (IoT) ecosystem. This is achieved through us of electric vehicle charging station management systems (EVCSMSs). However, the risks associated with cyber-attacks on IoT systems are also increasing at the same pace. To help in finding malicious traffic, intrusion detection systems (IDSs) play a vital role in traditional IT systems. This paper proposes a classifier
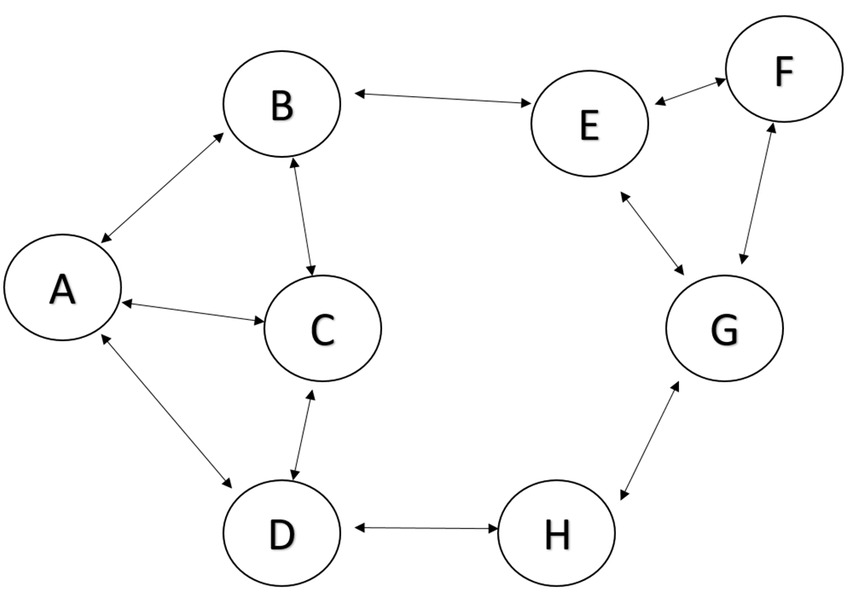
Vehicle Ad-Hoc Networks (VANETs) are a special type of Mobile Ad-Hoc Network (MANETs). In VANETs, a group of vehicles communicates with each other to transfer data without a need for a fixed infrastructure. In this paper, we compare the performance of two routing protocols: Ad-hoc on Demand Distance Vector protocol (AODV) and Destination-Sequenced Distance Vector protocol (DSDV) in VANETs. We measure the reliability of each protocol in the packet delivery. © 2022 IEEE.
There are many situations where there is a need for certain devices to be connected in a network independently without having a heavy infrastructure or human interventions to configure and connect them. This type of network is called ad-hoc networks. The key concern with such networks is how nodes communicate with each other and exchange information efficiently and securely. The issue with ad hoc networks is that traditional routing protocols are not suitable for such networks. In this paper, the performance of specific routing protocols for ad hoc networks will be evaluated. © 2022 IEEE.
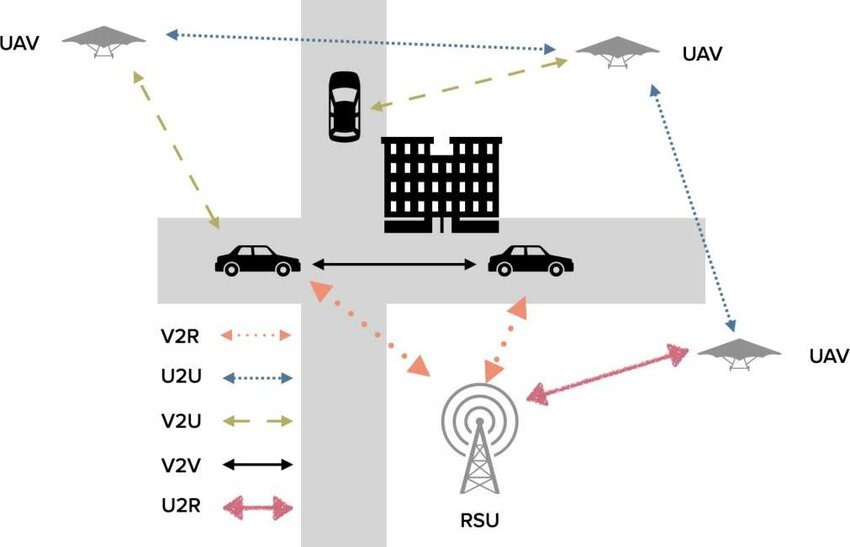
There are many novel techniques for intrusion detection in vehicular ad hoc networks and autonomous and connected vehicles. Detecting and reporting an attack is the main responsibility of an Intrusion detection system (IDS). Deep learning is used to make IDS smarter and more accurate. It implies other challenges on the other hand. This paper covers the proposed IDS based deep learning solutions and comparing effectiveness and efficiency of those solutions. © 2022 IEEE.
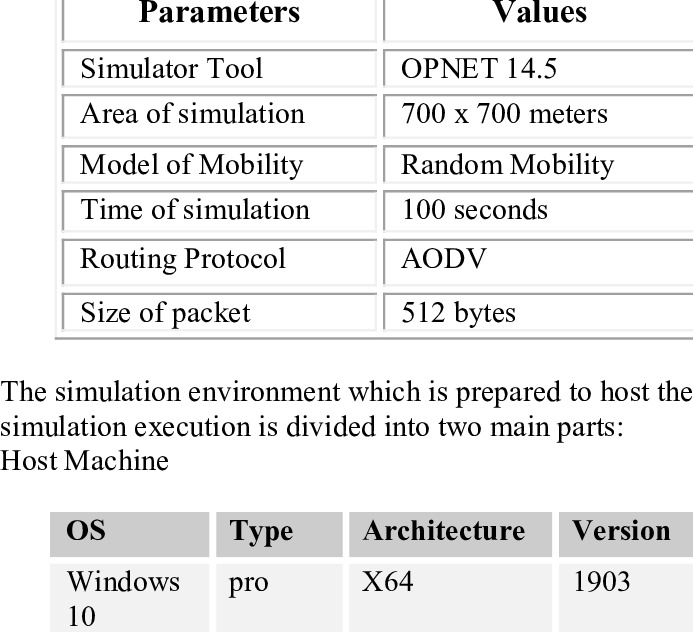
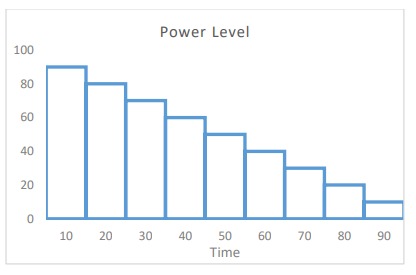
Mobile Ad hoc networks (MANETs) facilitate the communication of devices with a limited communication range. A MANET can be described as a decentralized network with a constantly changing topology. This makes it vulnerable to different attacks. The black hole is one of the most dangerous attacks in MANETs. This paper discusses the Blackhole attack in a random mobility environment and analyses its impact on MANETs using several parameters for single and multiple connections. © 2022 IEEE.