
Artificial Intelligence
Keyed Watermarks: A Fine-grained Tracking of Event-time in Apache Flink
Big Data Stream processing engines such as Apache Flink use windowing techniques to handle unbounded streams of events. Gathering all pertinent input within a window is crucial for event-time windowing since it affects how accurate results are. A significant part of this process is played by watermarks, which are unique timestamps that show the passage of events in time. However, the current watermark generation method in Apache Flink, which works at the level of the input stream, tends to favor faster sub-streams, resulting in dropped events from slower sub-streams. In our analysis, we found
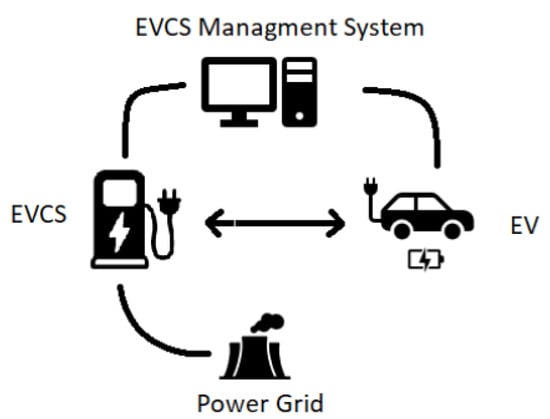
A Machine Learning-Based Intrusion Detection System for IoT Electric Vehicle Charging Stations (EVCSs)
The demand for electric vehicles (EVs) is growing rapidly. This requires an ecosystem that meets the user’s needs while preserving security. The rich data obtained from electric vehicle stations are powered by the Internet of Things (IoT) ecosystem. This is achieved through us of electric vehicle charging station management systems (EVCSMSs). However, the risks associated with cyber-attacks on IoT systems are also increasing at the same pace. To help in finding malicious traffic, intrusion detection systems (IDSs) play a vital role in traditional IT systems. This paper proposes a classifier
Ad-hoc Networks Performance based on Routing Protocol Type
There are many situations where there is a need for certain devices to be connected in a network independently without having a heavy infrastructure or human interventions to configure and connect them. This type of network is called ad-hoc networks. The key concern with such networks is how nodes communicate with each other and exchange information efficiently and securely. The issue with ad hoc networks is that traditional routing protocols are not suitable for such networks. In this paper, the performance of specific routing protocols for ad hoc networks will be evaluated. © 2022 IEEE.
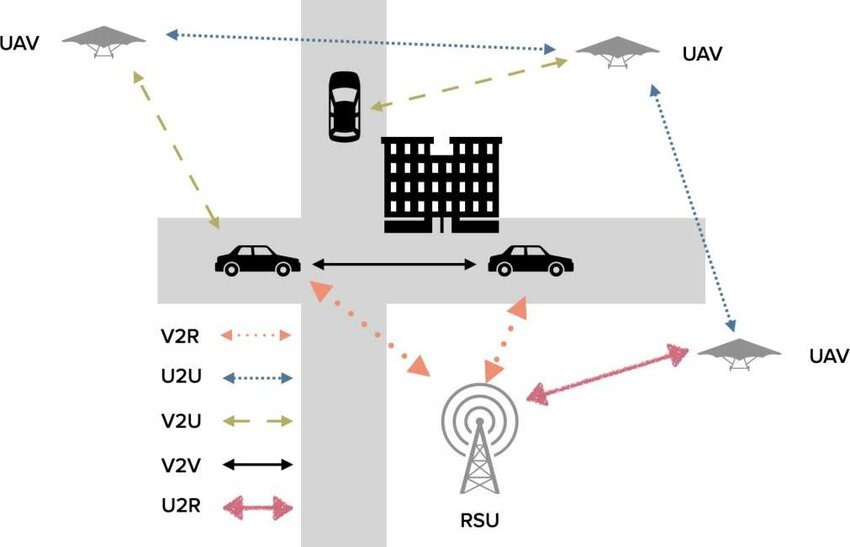
Intrusion Detection in VANETs and ACVs using Deep Learning
There are many novel techniques for intrusion detection in vehicular ad hoc networks and autonomous and connected vehicles. Detecting and reporting an attack is the main responsibility of an Intrusion detection system (IDS). Deep learning is used to make IDS smarter and more accurate. It implies other challenges on the other hand. This paper covers the proposed IDS based deep learning solutions and comparing effectiveness and efficiency of those solutions. © 2022 IEEE.
A Survey on Recommender Systems Challenges and Solutions
A recommender system is a set of tools for information retrieval. It improves access and proactively recommends items and services that match users' tastes by considering their explicit and implicit preferences and behaviors. Recommender systems have become very popular in the e-commerce field. Today, the internet is flooded with diverse information that makes it very difficult for the end-users to reach out for what they need. Recommender systems provide tailored views to users who are constantly adapted to the users' changing tastes. Although many recommendation techniques have been

Anomaly Detection Based on CNN and Regularization Techniques Against Zero-Day Attacks in IoT Networks
The fast expansion of the Internet of Things (IoT) in the technology and communication industries necessitates a continuously updated cyber-security mechanism to keep protecting the systems' users from any possible attack that might target their data and privacy. Botnets pose a severe risk to the IoT, they use malicious nodes in order to compromise other nodes inside the network to launch several types of attacks causing service disruption. Examples of these attacks are Denial of Service (DoS), Distributed Denial of Service (DDoS), Service Scan, and OS Fingerprint. DoS and DDoS attacks are the
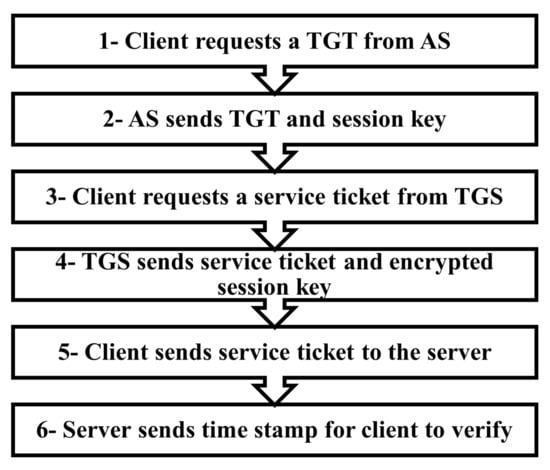
Active Directory Attacks—Steps, Types, and Signatures
Active Directory Domain is a Microsoft service that allows and facilitates the centralized administration of all workstations and servers in any environment. Due to the wide use and adoption of this service, it has become a target for many attackers. Active Directory attacks have evolved through years. The attacks target different functions and features provided by Active Directory. In this paper, we provide insights on the criticality, impact, and detection of Active Directory attacks. We review the different Active Directory attacks. We introduce the steps of the Active Directory attack and
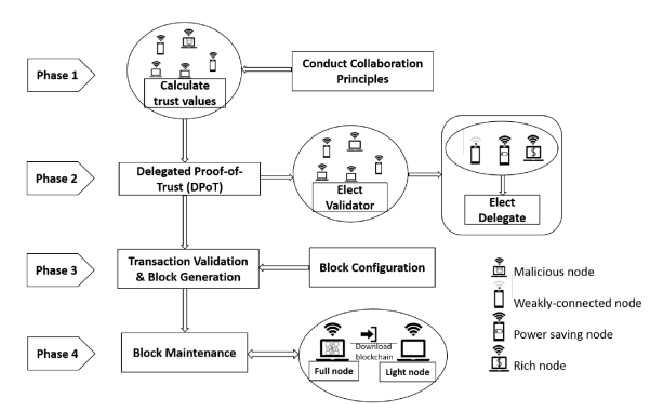
Using Blockchain Technology in MANETs Security
Many systems have recently begun to examine blockchain qualities in order to create cooperation enforcement methods. This paper provides a complete and extensive evaluation of work on multi-hop MANETs with blockchain-based trust control between nodes. We contextualize the snag of security in MANETs resulting from the lack of trust between the participating nodes. We present the blockchain concepts and discuss the limitation of the current blockchain in MANETs. We review the promising proposed ideas in the state-of-the-art based on research papers. Finally, we discuss and summarize strategies
Dual-Level Sensor Selection with Adaptive Sensor Recovery to Extend WSNs’ Lifetime
Wireless sensor networks (WSNs) have garnered much attention in the last decades. Nowadays, the network contains sensors that have been expanded into a more extensive network than the internet. Cost is one of the issues of WSNs, and this cost may be in the form of bandwidth, computational cost, deployment cost, or sensors’ battery (sensor life). This paper proposes a dual-level sensor selection (DLSS) model used to reduce the number of sensors forming WSNs. The sensor reduction process is performed at two consecutive levels. First, a combination of the Fisher score method and ANOVA test at the
Hybrid Global Optimization Algorithm for Feature Selection
This paper proposes Parallelized Linear Time-Variant Acceleration Coefficients and Inertial Weight of Particle Swarm Optimization algorithm (PLTVACIW-PSO). Its designed has introduced the benefits of Parallel computing into the combined power of TVAC (Time-Variant Acceleration Coefficients) and IW (Inertial Weight). Proposed algorithm has been tested against linear, non-linear, traditional, and multiswarm based optimization algorithms. An experimental study is performed in two stages to assess the proposed PLTVACIW-PSO. Phase I uses 12 recognized Standard Benchmarks methods to evaluate the