
Artificial Intelligence
Enhanced removal of crystal violet using rawfava bean peels, its chemically activated carbon compared with commercial activated carbon
Crystal violet is a basic dye that is widely used by various industries, such as textiles and paints. These industries discharge their effluents, contaminated with crystal violet, into water streams, and these effluents have an adverse effect on aquatic organisms, the environment, and human health. Crystal violet is a basic dye that is widely used by various industries, such as textiles and paints. These industries discharge their effluents, contaminated with crystal violet, into water streams, and these effluents have an adverse effect on aquatic organisms, the environment, and human health
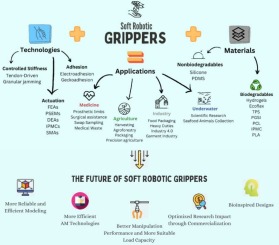
Soft robotic grippers: A review on technologies, materials, and applications
The growing need for manipulators capable of handling delicate objects with care and coexisting safely with humans has brought soft robots to the forefront as a practical and cost-effective solution. In this context, this paper aims to explore soft grippers, a unique and versatile subset of soft robots. It provides an overview of various soft grasping techniques and materials, highlighting their respective advantages and limitations, along with showcasing several designed and tested models. As medicine and agriculture are acknowledged as pivotal domains required for basic human survival, this
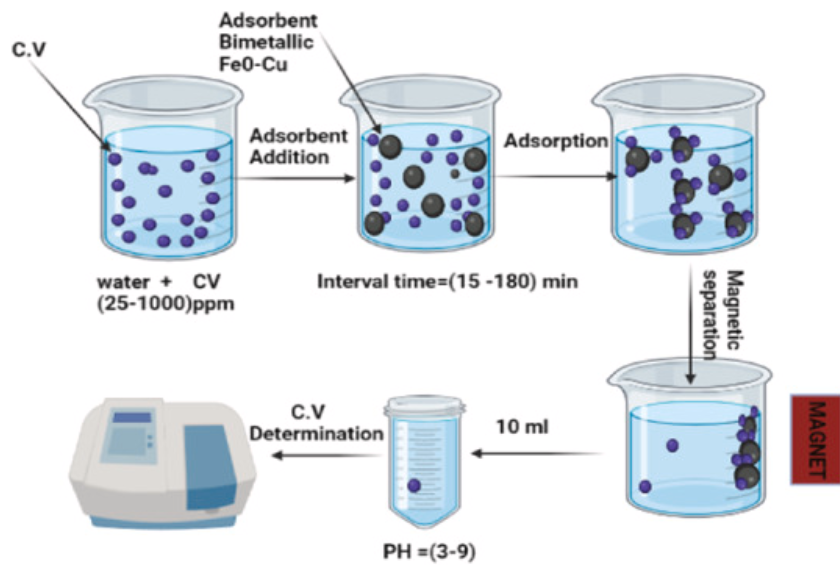
Crystal violet removal using bimetallic Fe0–Cu and its composites with fava bean activated carbon
Nano zero-valent iron (nZVI), bimetallic nano zero-valent iron-copper (Fe0– Cu), and fava bean activated carbon-supported bimetallic nano zero-valent iron-copper (AC-Fe0-Cu) are synthesized and characterized using DLS, zeta potential, FT-IR, XRD, and SEM. The maximum removal capacity is demonstrated by bimetallic Fe0–Cu, which is estimated at 413.98 mg/g capacity at pH 7, 180 min of contact duration, 120 rpm shaking speed, ambient temperature, 100 ppm of C.V. dye solution, and 1 g/l dosage. The elimination capability of the H2SO4 chemical AC-Fe0-Cu adsorbent is 415.32 mg/g under the same

Review on Coral Reef Regeneration Methods through Renewable Powered Electrotherapy
The restoration of coral reef population in coastal regions is currently a growing concern. Many attempts have been made to apply new approaches to limit the deterioration of coral reefs, and to accelerate the growth of new reefs to protect coastal areas and ecosystems using available renewable energy sources. This paper highlights the new approaches and their various advantages and limitations in tidal and wave energy. The paper also suggests improvements to some of those systems using the recent developments in soft robotics, especially the use of biomimetic fish as a feasible support
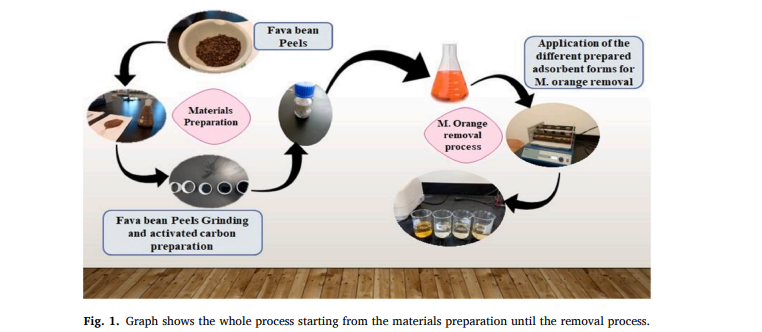
Experimental investigation of methyl-orange removal using eco-friendly cost-effective materials raw fava bean peels and their formulated physical, and chemically activated carbon
The discharge of effluents from dye industries into water streams poses a significant environmental and public health risk. In response, eco-friendly adsorbents derived from agricultural waste, such as Fava Bean Peels (R–FBP), have been investigated as potential materials for the removal of such pollutants. In this study, R–FBP and their corresponding physical and chemically activated carbon (P-RFB-AC and C-FBP-AC) were synthesized using H3PO4 acid and characterized using FT-IR, and SEM analyses. An optimization process was conducted to determine the optimum conditions for achieving high
Bio-inspired adsorption sheets from waste material for anionic methyl orange dye removal
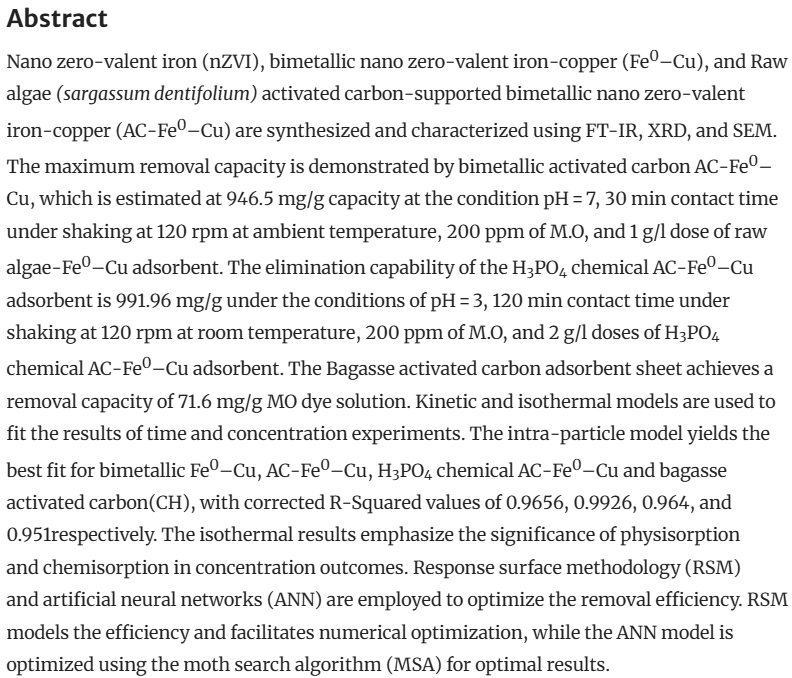
Abstract: Nano zero-valent iron (nZVI), bimetallic nano zero-valent iron-copper (Fe0–Cu), and Raw algae (sargassum dentifolium) activated carbon-supported bimetallic nano zero-valent iron-copper (AC-Fe0–Cu) are synthesized and characterized using FT-IR, XRD, and SEM. The maximum removal capacity is demonstrated by bimetallic activated carbon AC-Fe0–Cu, which is estimated at 946.5 mg/g capacity at the condition pH = 7, 30 min contact time under shaking at 120 rpm at ambient temperature, 200 ppm of M.O, and 1 g/l dose of raw algae-Fe0–Cu adsorbent. The elimination capability of the H3PO4
Valorization of Agricultural and Marine Waste for Fabrication of Bio-Adsorbent Sheets
Industrial wastewater often contains considerable amounts of toxic pollutants that would endanger public health and the environment. In developing countries, these toxins are often discharged into natural ecosystems without pretreatment as it requires costly treatment processes, which causes long-term harmful socioeconomic impacts. Employing wastewater treatment plants using physical, biological, and chemical methods to clean the wastewater is considered by many nations the answer to the environmental crises. The treated water could be used for targeting the irrigation systems in its majority
Voltage-controlled M-M relaxation Oscillator
This paper discusses voltage-controlled M-M relaxation oscillator with analytical and circuit simulations. The introduced circuit has two different configurations based on the polarities of memristor; whether they are in the same direction or in the opposite direction. The Analytical formulas are function of the reference voltage such as the oscillation frequency and oscillation conditions for each case are derived with some numerical examples. The circuit simulations are introduced to validate the mathematical concepts as well as the effect of the reference voltage which can be used in
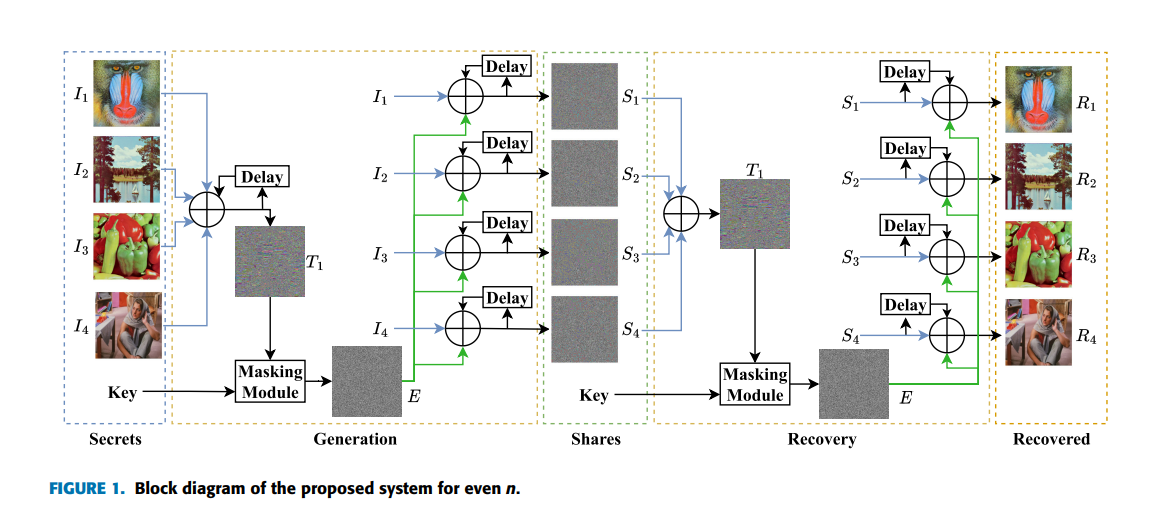
An Efficient Multi-Secret Image Sharing System Based on Chinese Remainder Theorem and Its FPGA Realization
Multi-Secret Image Sharing (MSIS) is important in information security when multiple images are shared in an unintelligible form to different participants, where the images can only be recovered using the shares from participants. This paper proposes a simple and efficient ( n,n )-MSIS system for colored images based on XOR and Chinese Remainder Theorem (CRT), where all the n share are required in the recovery. The system improves the security by adding dependency on the input images to be robust against differential attacks, and by using several delay units. It works with even and odd number
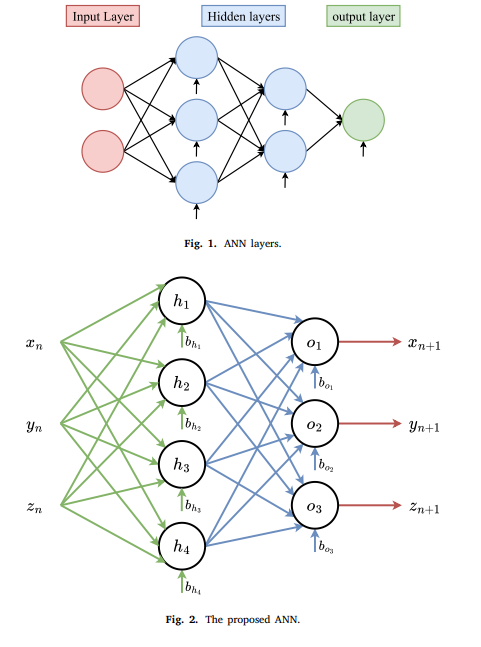
Artificial Neural Network Chaotic PRNG and simple encryption on FPGA
Artificial Neural Networks (ANNs) are remarkably able to fit complex functions, making them useful in various applications and systems. This paper uses ANN to fit the Pehlivan–Uyaroglu Chaotic System (PUCS) to produce an Artificial Neural Network Chaotic Pseudo-Random Number Generator (ANNC-PRNG). The proposed PRNG imitates the PUCS chaotic system's properties and attractor shape. The proposed ANNC-PRNG is implemented in a simple image encryption system on the Xilinx Kintex-7 Genesys 2 Field Programmable Gate Array (FPGA) board. Hardware realization of an ANN trained on chaotic time series has