
Artificial Intelligence
Microfactory strategic decision making using simulation
This paper aims to study how the agility concept is successfully applied in manufacturing facilities. The study is involved in selecting the industry and the machines for the novel Microfactory established at Nile Preneurs, Nile University, with focus on the sheet metal workshop located in the Microfactory. The recommendations of this work include the most suitable layout, scheduling technique according to the manufacturing lead time, utilization, work in process, tool change over and distance travelled by operators. Flexsim simulation software is used to determine the optimum combination of

Organic Binding Materials in Cotton Waste
The continued logging for hardwood in subtropical rainforests is causing deforestation and the destruction of diverse environmental ecosystems. Synthetic plastics and particle boards containing synthetic binders such as formaldehydes are alternatives to hardwood, both of which are harmful to the environment and human health. To eliminate wood logging, various biomaterials could be used as promising alternatives to wooden materials. Cotton have been shown to be a viable alternative to various types of wood. Binders are essential in the production of composite wood from cotton. Natural
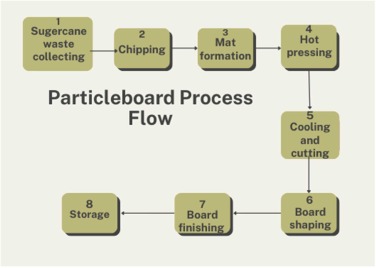
Sustainable utilization of sugarcane bagasse for wood-based panels: A promising approach for waste management in Egypt
One method to sustainable development is to reduce waste generation and recycle it in a way that contributes to the economic, social, and environmental goals of sustainable development. The study focuses on particle board production from Sugar Cane Bagasse (SCB). Various fiber-matrix combinations were used to create composites using SCB and epoxy resin matrix. Mechanical testing and water absorbance tests were employed to assess the effects of the epoxy content (0–25 wt%). The outcomes demonstrated that the optimal tensile strength of bio composites was attained by the 25 wt% of epoxy with SCB
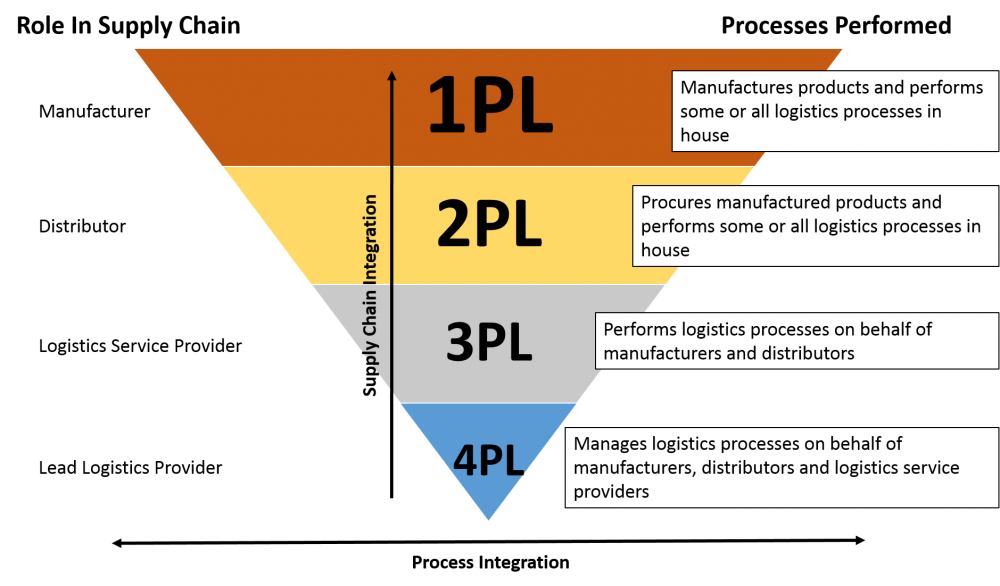
Modelling of 3rd Party Logistics Provider Using Unified Modelling Language
Transportation is a vital driver in logistics management. Third party logistics (3PL) involves a company outsourcing logistics services to other companies. Third party logistics aids in facilitating and optimizing transportation by aggregating demand for trucks and drivers. This paper proposes a model of a transportation 3PL System. The system under study is modelled using the Unified Modelling Language 2.0 (UML 2.0) through an analysis of 3PL provider located in Egypt. The system is analyzed and identified with Integrated Definition for Function Modeling Diagram (IDEF0) & context diagram
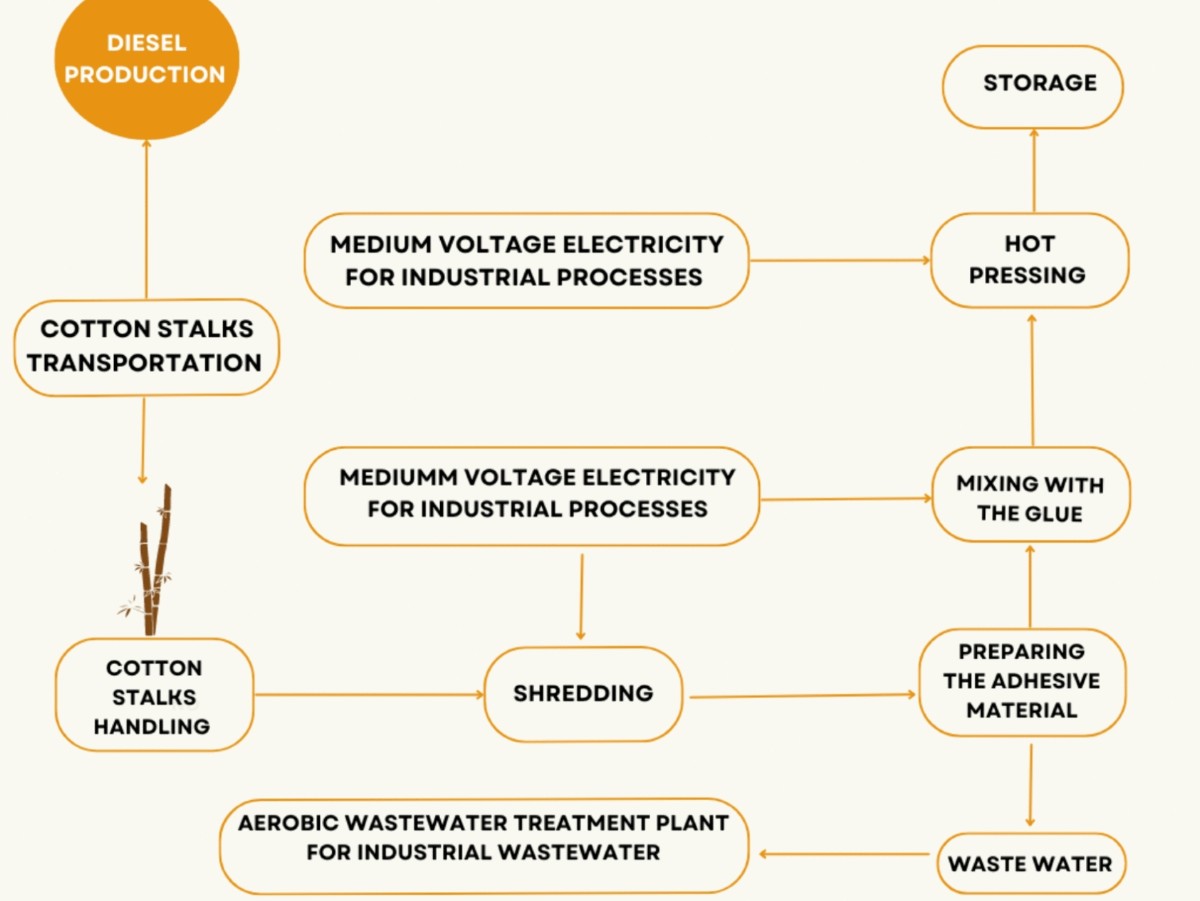
Mechanical and environmental performance assessment of cotton stalk composites with natural adhesives for sustainable construction materials
Carbon dioxide emissions pose a global issue, with deforestation, forest loss from logging, fires, and construction highlighting the adverse effects of climate change. Urgent action is required to reduce carbon dioxide emissions and preserve forests. Egypt can contribute to reducing greenhouse gas emissions by effectively utilizing its waste resources, especially agricultural waste. The research focuses on developing environmentally friendly and sustainable construction materials with a forward-looking approach. This involves exploring alternative options for synthetic formaldehyde adhesives
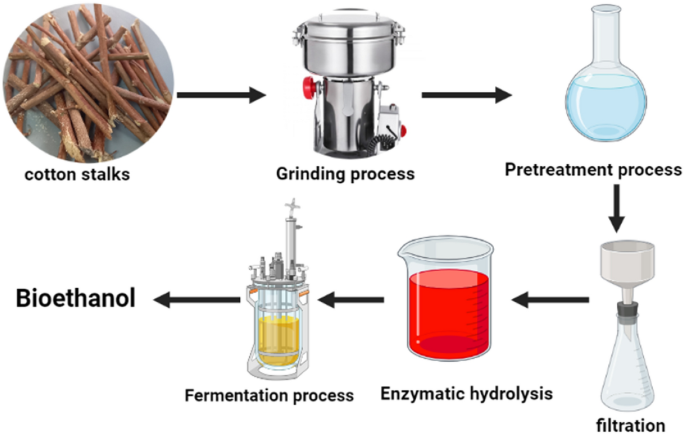
A comparative cradle-to-gate life cycle assessment of three cotton stalk waste sustainable applications
This paper presents a novel approach to utilizing agricultural waste. It compares three different applications for cotton stalks: fabrication of wood composites, bioethanol production, and biogas cradle-to-gate Life cycle assessment production processes. Cotton cultivation generates a lot of debris, mostly cotton stalks, which are incinerated or landfilled, Sustainable resource management is critical for maintaining the ecosystem, and economic stability, and promoting social fairness since it ensures the long-term availability of resources while minimizing environmental damage. The
Bioplastics, biodegradable plastics, and degradation in natural environments
The widespread manufacturing of traditional plastics and their use in various commercial applications endangers both fossil fuel sources and the environment. Bioplastics have emerged from the development of renewable resources to provide sustainable solutions. These polymers are more acceptable than conventional plastics because they use renewable resources such as agricultural wastes (rather than petroleum sources) and are biodegradable under various conditions. The physical and chemical structure of bioplastics significantly affects their biodegradability, and their environment plays a

Sustainable wood composite production using cotton waste and exopolysaccharides as green binders
Burning agricultural waste is a common practice among farmers in many countries, leading to global warming and climate change. Upcycling abundant agricultural waste will prevent incineration-generated hazards and provide sustainable and eco-friendly wood. An alternative wood composite was prepared using Aspergillus niger mycelium and exopolysaccharides (EPS) as a green binder. Autoclaving and gamma irradiation were both tested as wood pre-treatment to enhance binding. The mixture was incubated at 30 °C for 1 week. The results showed that wet pre-treatment using autoclaving resulted in improved
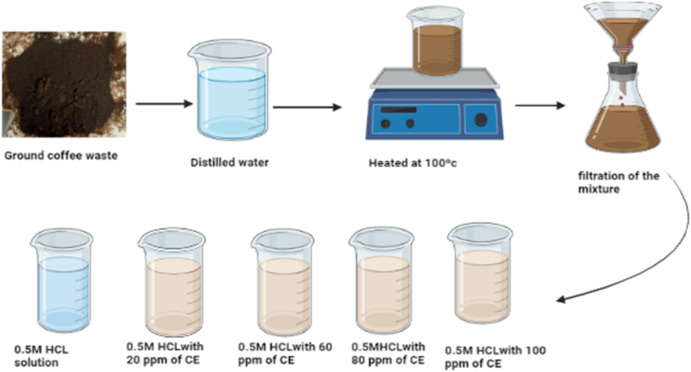
Electrochemical evaluation of green corrosion inhibitor based on ground coffee waste in Petroleum fields
Corrosion poses a significant challenge in industrial sectors that handle metallic materials. The objective of this study was to evaluate the feasibility of employing a cost-effective, organic, and eco-friendly solution derived from discarded coffee grounds, known as coffee waste extract (CE), to mitigate the corrosion rate of carbon steel in an acidic environment comprising 0.5 M hydrochloric acid (HCL) with varying concentrations ranging from 20 to 100 ppm. This research aims to explore the prospective utilization of coffee waste as an inhibitory agent that can be reutilized for diverse

Nanoionic liquid for hydrogen generation and storage
Climate change and the increase in population are encouraging many researchers to work on getting nonconventional sources of energy. Ionic liquids (ILs) have unique physicochemical properties for this field. Therefore, using nanoionic liquids and ILs in energy storage is very promising, particularly considering the reported high efficiency in the existing literature. Hydrogen production technologies have garnered considerable interest in the energy sector, particularly involving the formation of water from a petroleum field and carbon steel materials. Modern methods rely on hydrogen production