
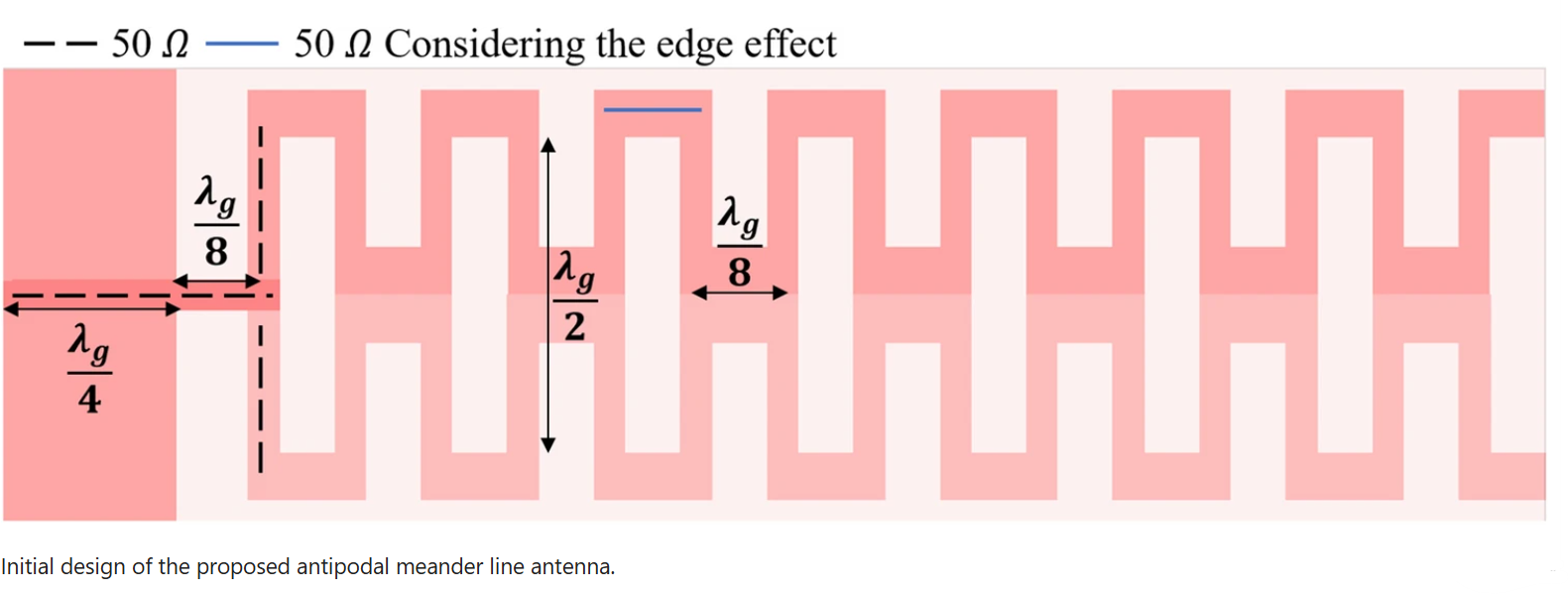
This paper introduces a planar antipodal meander line antenna fabricated using RO3003 substrate. The proposed antenna is designed to radiate in the end-fire direction, achieving a maximum measured gain of 10.43 dBi within its working bandwidth, which ranges from 2.24 GHz to 2.7 GHz, covering long-range WLAN/WiMAX applications. A systematic procedure is adopted in the design process to prove its tunability to cover other application requirements in terms of gain and bandwidth. The proposed design steps show that the bandwidth and the gain can independently be controlled by adjusting specific

Light trapping as a result of embedding plasmonic nanoparticles (NPs) into photovoltaics (PVs) has been recently used to achieve better optical performance compared to conventional PVs. This light trapping technique enhances the efficiency of PVs by confining incident light into hot-spot field regions around NPs, which have higher absorption, and thus more enhancement of the photocurrent. This research aims to study the impact of embedding metallic pyramidal-shaped NPs inside the PV’s active region to enhance the efficiency of plasmonic silicon PVs. The optical properties of pyramidal-shaped

This paper proposes a metamaterial Terahertz sensor with detected sensitivity for biomedical applications. The proposed sensor consists of two interdigitated golden C-shaped structures on top of Teflon substrate that is backed by a gold layer. The absorption spectrum contains a peak resonance corresponding to the maximum absorption of the sensor. The proposed sensor has a maximum narrow-band absorption at 3.35 THz, with an average sensitivity of 2.256 THz/RIU and a quality factor of 22.3. The developed model is checked for the range of refractive index range between n= 1.3 to n= 1.4 to check

Plasmonic Photovoltaics (PVs) are an effective method for increasing optical absorption by adding metallic nanoparticles to the photovoltaic active layer. The role of these nanoparticles is confining the incident light near them in the PV cell, resulting in thin film PVs of enhanced efficiency. Therefore, different materials and new NPs shapes are used for this purpose. In this research, a step pyramid is introduced as a novel structure for nanoparticles for enhancing plasmonic PVs by embedding an array of the proposed step pyramid nanoparticles within the PV cell. Therefore, the extinction
Monte Carlo (MC) simulation is a widely adopted computational method that relies on random sampling, but it is susceptible to exhibiting patterns and biases due to the use of pseudo-random numbers. In contrast, Quasi-Monte Carlo (QMC) techniques employ low discrepancy sequences, resulting in more evenly distributed random numbers and the potential for more accurate and reliable simulation outcomes. Mushroom-Waveguide Photodetectors (WGPDs) are integrated to a wide range of applications, and their performance is critically dependent on precise dimensional parameters. In this research, we

In this paper, a highly directive meander line antenna is proposed to be utilized in the unlicensed Bluetooth band. The main goal of the proposed structure is to achieve low profile, and high gain in the Bluetooth band. Moreover, the antenna should be of low cost to be suitable for commercial use. The proposed structure is simulated using HFSS and CST to verify the obtained results. The maximum calculated gain of the antenna is 9.95 dBi (9.79 dBi) along the end-fire direction as simulated by HFSS (CST). The antenna demonstrated high radiation efficiency which is around 96% over its working
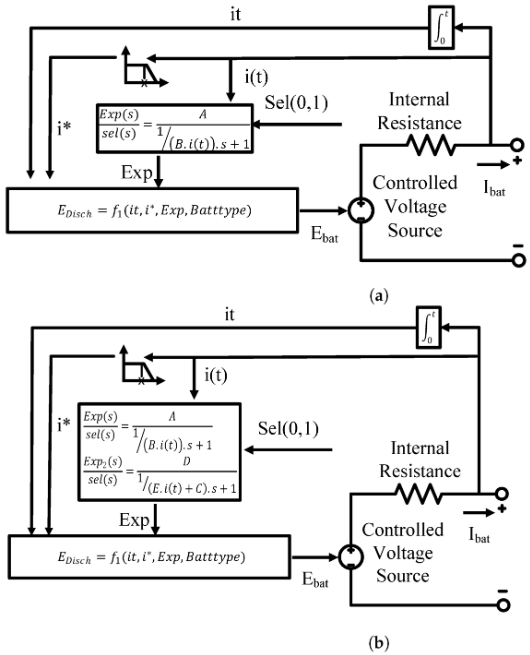
Lithium-ion batteries are crucial building stones in many applications. Therefore, modeling their behavior has become necessary in numerous fields, including heavyweight ones such as electric vehicles and plug-in hybrid electric vehicles, as well as lightweight ones like sensors and actuators. Generic models are in great demand for modeling the current change over time in real-time applications. This paper proposes seven dynamic models to simulate the behavior of lithium-ion batteries discharging. This was achieved using NASA room temperature random walk discharging datasets. The efficacy of

In various areas of life, rechargeable lithium-ion batteries are the technology of choice. Equivalent circuit models are utilized extensively in characterizing and modeling energy storage systems. In real-time applications, several generic-based battery models are created to simulate the battery's charging and discharging behavior more accurately. In this work, we present two generic battery models based on Mittag-Leffler function using a generic Standard battery model as a reference. These models are intended to fit the continuous discharging cycles of lithium-ion, Nickel-cadmium, and Nickel

This paper introduces an efficient prediction algorithm tailored for advanced and high efficiency video coding, encompassing both H.264 and H.265. The proposed approach aims at replacing the standard intra prediction methodology by employing a streamlined prediction mode, which significantly reduces computational overhead and system complexity while eliminating the requirement for mode decision. By leveraging block comparison criteria, the designed method combines neighboring blocks in a linear fashion to accurately represent the target block. Extensive comparisons are conducted with the H.264
We investigate a one-dimensional restriction of a nonlinear model of thermo-electroelasticity in extended thermodynamics and in the quasi-electrostatic regime (see Ghaleb et al. in Int J Eng Sci 119:29–39, 2017. https://doi.org/10.1016/j.ijengsci.2017.06.010). An additional dependence of the thermal conductivity and the thermal relaxation time on temperature and heat flux is introduced. The aim of the present work is to assess the effect of some quadratic nonlinear couplings between the mechanical, thermal and electric fields. Such couplings are known to have a crucial effect on the stability