
Artificial Intelligence
Light-Weight Face Mask Detector
People's lives have been severely disrupted recently due to the COVID-19 outbreak's fast worldwide proliferation and transmission. An option for controlling the epidemic is to make individuals wear face masks in public. For such regulation, automatic and effective face detection systems are required. A facial mask recognition model for real-time video-recorded streaming is provided in this research, which categorizes the pictures as (with mask) or (without mask). A dataset from Kaggle was used to develop and assess the model. The suggested system is computationally more precise, efficient and
Accelerated Edge Detection Algorithm for High-Speed Applications
Digital Image Processing (DIP) is a growing field for various applications, such as autonomous vehicles and video surveillance. To improve the performance of DIP systems, image processing algorithms are implemented in hardware rather than software. The idea here is primarily to get a faster system than software imaging or other alternative hardware. Field-programmable gate arrays (FPGAs) have the advantages of parallel processing, low cost, and low power consumption. These semiconductor devices contain many logic blocks that can be programmed to perform everything from basic digital gate-level
Light-Weight Face Shape Classifier for Real-Time Applications
Deep neural networks (DNNs) are memory and computationally intensive; hence they are difficult to apply to real-time systems with limited resources. Therefore, the DNN models need to be carefully optimized. The solution was a model based on a convolutional neural network (CNN) called MobileNet that decreases the computational and space complexities with classification precision loss by utilizing depthwise separable convolutions. This study uses MobileNet vl architecture to improve image classification complexities to reach an acceptable complexity that can be used in real-time applications
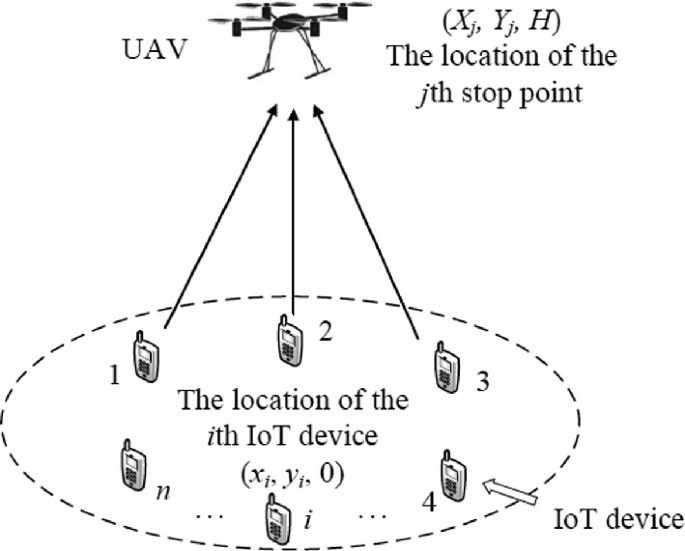
UAV-Assisted IoT Data Collection Optimization Using Gaining-Sharing Knowledge Algorithm
Unmanned aerial vehicles (UAVs) provide an energy-efficient and robust solution for data collection from the internet of things (IoT) devices. However, the UAV’s deployment optimization, including locations of the UAV’s stop points, is necessary to save the overall energy consumption and conduct the data collection efficiently. Thus, the objective is to minimize the energy consumption of the UAV and the IoT devices while collecting the data efficiently. This chapter proposes gaining-sharing knowledge (GSK) algorithm for optimizing the UAV’s deployment. In GSK, the number of UAV’s stop points
Liver Disease Diagnosis using Tree-Based Machine Learning Algorithms
Liver Disease (LD) is a lethal yet relatively common disorder that is impacting the lives of millions across the world, causing slow yet irreversible internal organ damage or total organ failure if left untreated. In this study, LD is determined as the damage a Liver sustained due to excessive drug or alcohol abuse and other causes which leave severe scarring on the Liver leading to permanent functionality loss or cancer. This study revolves around determining if a person suffers from the disease regardless of the stage of the disease. To detect and minimize the impact of LD, tree-based
Threshold Energy Based LEACH-K Effect on the Accessibility of Wireless Sensor Networks
This paper aims to deliver an exhaustive investigation on the threshold energy parameter's direct impact on the Cluster Head (CH) selection phase in Low-Energy Adaptive Clustering Hierarchy Based on K-Means (LEACH-K) protocols. The most prominent threshold energy selection criterion out of the scarcely available research on the LEACH-K threshold energy parameter is used to simulate the LEACH-K protocol. Simulations are carried out on scaled-up Wireless Sensor Networks (WSNs) in terms of size and number of nodes. An analysis is performed on the life-cycle of the CH selection process, which

Novel Edge AI with Power-Efficient Re-configurable LP-MAC Processing Elements
Deep learning has become increasingly important in various fields, such as robotics, image processing, and speech recognition. However, the high computational requirements of deep learning models make it challenging to deploy them on edge & embedded devices with constrained power and area budgets. This paper proposes a novel low-power technique for implementing deep learning models on edge devices called LP-MAC (Low Power Multiply Accumulate). LP-MAC is designed for fixed-point format operations and takes advantage of reusing the input vector for MAC operations. It provides a new hardware

Sustainable Energy-Aware Task Scheduling for Wearable Medical Device Using Flower Pollination Algorithm
Power management and energy conservation are crucial for medical wearable devices that rely on energy harvesting. These devices operate under strict power budgets and require prolonged and stable operation. To achieve this, Energy-aware task scheduling is proposed as a solution to minimize energy consumption while ensuring the continued operational capabilities of the device. our paper presents a task scheduling method using the Flower Pollination Algorithm (FPA). The proposed task scheduling focuses on managing the activity of key components such as the heart rate sensor, temperature sensor

Modified Arnold Transform and DNA Manipulation for Chaos-Based RGB Image Encryption
Multimedia applications use image encryption algorithms extensively to safeguard and authenticate digital images. This paper presents an RGB image encryption method, which uses Chaos, DNA, pixel sum, and modified Arnold transform. The suggested algorithm is validated to be robust and resistant to visual, statistical, differential, and brute-force attacks. Additionally, the resulting encrypted images pass all tests of the NIST SP 800-22 test suite. © 2023 IEEE.
An Efficient DMO Task Scheduling Technique for Wearable Biomedical Devices
The popularity of wearable devices has grown as they improve the quality of life in many applications. In particular, for medical devices, energy harvesters are the dominating source of energy for wearable devices. However, their power budget is limited. Thus, power-saving techniques are essential components in the whole technology stack of those devices. That is, choosing the optimal schedule for different tasks running on the wearable device can help to reduce energy consumption. This paper presents a sensor task scheduling technique for optimizing energy consumption for energy harvesting