
Energy and Water

A Framework for Democratizing Open-Source Decision-Making using Decentralized Autonomous Organization
The open Source Software (OSS) became the backbone of the most heavily used technologies, including operating systems, cloud computing, AI, Blockchain, Bigdata Systems, IoT, and many more. Although the OSS individual contributors are the primary power for developing the OSS projects, they do not contribute to the OSS project's decisionmaking as much as their contributions in the OSS Projects development. This paper proposes a framework to democratize the OSS Project's decision-making using a blockchain-related technology called Decentralized Autonomous Organization (DAO). Using DAO
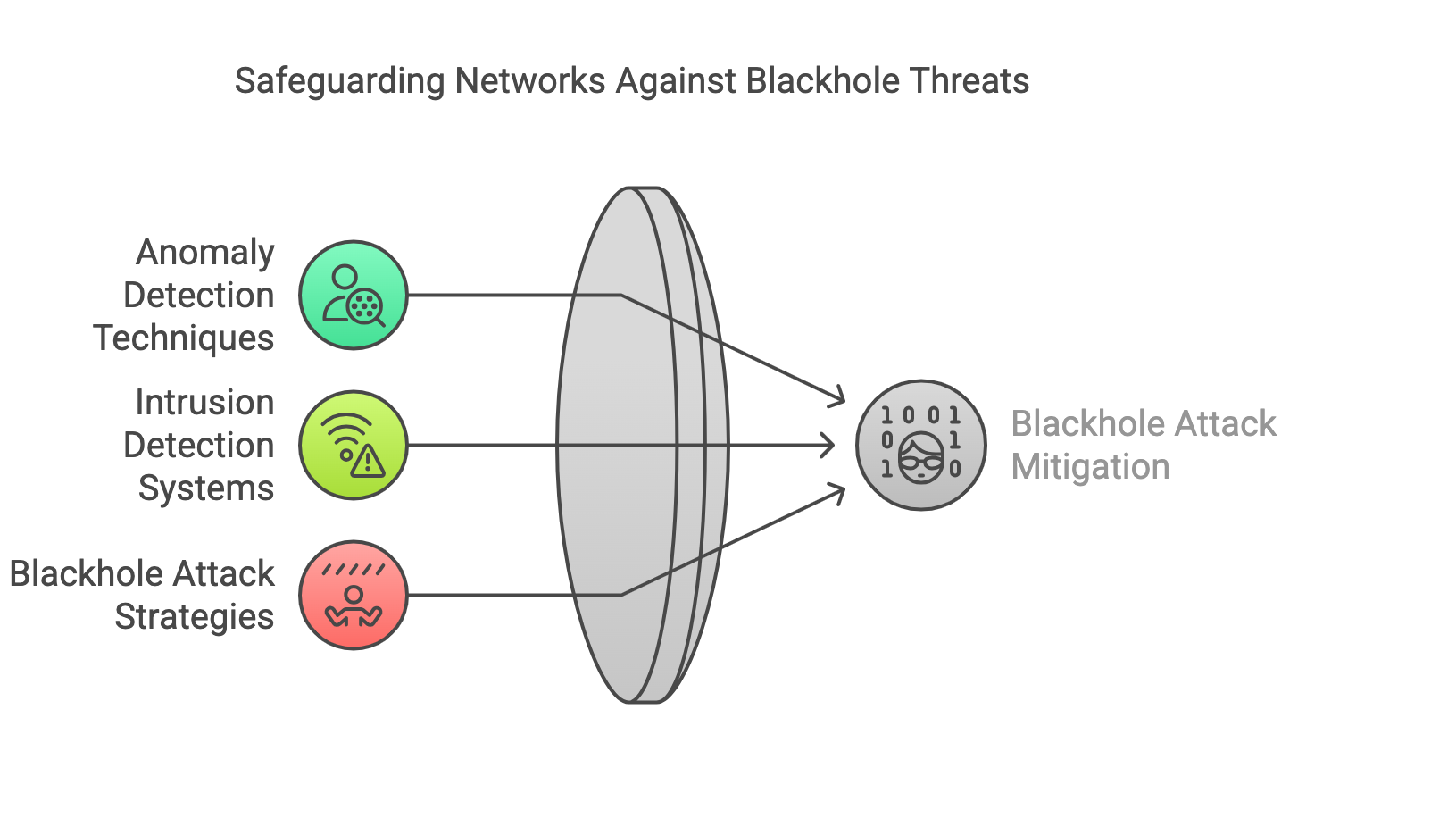
Anomaly-Based Intrusion Detection for Blackhole Attack Mitigation
In the contemporary environment, mobile ad hoc networks (MANETs) are becoming necessary. They are absolutely vital in a variety of situations where setting up a network quickly is required; however, this is infeasible due to low resources. Ad hoc networks have many applications: education, on the front lines of battle, rescue missions, etc. These networks are distinguished by high mobility and constrained compute, storage, and energy capabilities. As a result of a lack of infrastructure, they do not use communication tools related to infrastructure. Instead, these networks rely on one another

Detecting Mimikatz in Lateral Movements Using Windows API Call Sequence Analysis
Advanced Persistent Threat (APT) is classified as a high threat stealthy attack on modern networks. It uses sophisticated techniques, which makes it very challenging to be detected. It can remain undetectable for an extended period by gaining unauthorized access and lateral movements in the target network. Depending on the APT group tools, responding to the initiated attack can be challenging and composite. Mimikatz is a credential theft tool used in many APT attacks to achieve their objectives. It calls Windows APIs in a particular order during the execution time. This makes the APT group
A novel artificial intelligent-based approach for real time prediction of telecom customer’s coming interaction
Predicting customer’s behavior is one of the great challenges and obstacles for business nowadays. Companies take advantage of identifying these future behaviors to optimize business outcomes and create more powerful marketing strategies. This work presents a novel real-time framework that can predict the customer’s next interaction and the time of that interaction (when that interaction takes place). Furthermore, an extensive data exploratory analysis is performed to gain more insights from the data to identify the important features. Transactional data and static profile data are integrated
Multiobjective design optimization of parabolic trough collectors
Despite the large amount of research conducted on PTC performance analysis, few and rare numbers of research have considered the design optimization of PTCs. In the present work, a novel multiobjective-optimization model is developed for design optimization of PTCs. The objective functions are the thermal and exergetic efficiencies because they are the most important performance indicators (PIs) of PTCs. The design variables are the inlet temperature, and the outlet and inlet diameters of the PTC receiver tube. The PTC material volume (refers to the volume of the PTC receiver and collector) is
Analysis, control, and optimization of aeroelastic systems: An introduction to the recent literature for the new investigator
Aeroelasticity studies the static and dynamic interaction between structural deformation and fluid forces. As a result, the aeroelasticity is usually divided into three parts: aerodynamics, structural response, and dynamics with statics as a special case. Instabilities may occur to this interaction (feedback) that lead to structural failure and, even when no instability occurs, the interaction may lead to degradation or improvement of the system performance. There are several unstable phenomena may occur for elastic bodies such as flutter, divergence, low cycle oscillation, buffet, and control

Dynamic Modeling and Identification of the COVID-19 Stochastic Dispersion
In this work, the stochastic dispersion of novel coronavirus disease 2019 (COVID-19) at the borders between France and Italy has been considered using a multi-input multi-output stochastic model. The physical effects of wind, temperature and altitude have been investigated as these factors and physical relationships are stochastic in nature. Stochastic terms have also been included to take into account the turbulence effect, and the r and om nature of the above physical parameters considered. Then, a method is proposed to identify the developed model's order and parameters. The actual data has

An IoT Privacy-Oriented selective disclosure credential system
Personal credentials, such as passports and drivers' licenses, can be implemented electronically using multi-show protocols. In this paper, we introduce an IoT Privacy-Oriented selective disclosure credential system, i.e. based on bilinear pairings and multilinear maps. The proposed system consists of three protocols, which allow users to be in control of their personal credentials. The Credentials Authority (CA) verifies and attests to the users credentials. Once the CA signs these credentials, the users cannot modify any of them. Moreover, the users can mask these credentials in every
Text-Independent Algorithm for Source Printer Identification Based on Ensemble Learning
Because of the widespread availability of low-cost printers and scanners, document forgery has become extremely popular. Watermarks or signatures are used to protect important papers such as certificates, passports, and identification cards. Identifying the origins of printed documents is helpful for criminal investigations and also for authenticating digital versions of a document in today’s world. Source printer identification (SPI) has become increasingly popular for identifying frauds in printed documents. This paper provides a proposed algorithm for identifying the source printer and
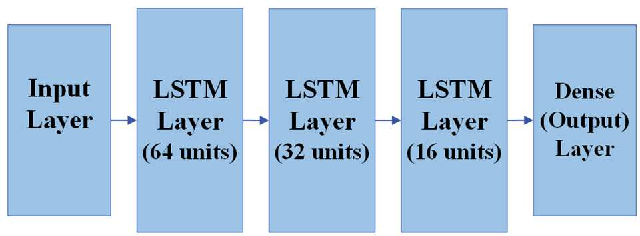
Multi-Band Radio Frequency Energy Predictor for Advanced Energy Harvesting Cellular Bands Systems
Radio Frequency (RF) energy harvesting has been employed to power wireless devices. Nevertheless, RF energy harvesting encounters restrictions regarding the quantity of power it can harvest depending on signal accessibility. As a result, accurately predicting energy levels becomes crucial for enhancing the performance of energy harvesting circuits. Most research efforts have concentrated on enhancing power harvesting policies or theoretically estimating the energy obtained through RF energy harvesting. Moreover, the existing literature has primarily focused on single-band prediction approaches