
Edge detection is one of the main steps in the image processing field, especially in bio-medical imaging, to diagnose a disease or trace its progress. The transfer of medical images makes them more susceptible to quality degradation due to any imposed noise. Hence, the protection of this data against noise is a persistent need. The efficiency of fractional-order filters to detect fine details and their high noise robustness, unlike the integer-order filters, it renders them an attractive solution for biomedical edge detection. In this work, two novel central fractional-order masks are proposed
Computer vision is shaping a new era with its constant development of SOTA algorithms. One heavily contested sub-field of computer vision is face detection, due to its versatile usage in many fields such as security, medical diagnosis, entertainment, and military applications. As the technology develops, it aims to run faster and more accurately on mobile devices and remote computers. In this paper, we aim to compare a number of the best face recognition algorithms and analyze the performance of each of them by deploying each algorithm on a Jetson Nano Developer Kit. Among the 6 algorithms
The issues of multitude of noisy, irrelevant, misleading features, and the capability to tackle inaccurate and inconsistent data in real world topics are the justification to turn into one of the most significant needs for feature selection. This paper proposes an intelligent hybrid approach using Rough Set Theory (RST), Chaos Theory and Binary Grey Wolf Optimization Algorithm (CBGWO) for feature selection problems. Ten different chaotic maps are used to estimate and tune GWO parameters. Experiments are applied on complex medical datasets with various uncertainty features and missing values

This paper studies the frequency/time selective K-user Gaussian interference channel with secrecy constraints. Two distinct models, namely the interference channel with confidential messages and the interference channel with an external eavesdropper, are analyzed. The key difference between the two models is the lack of channel state information (CSI) of the external eavesdropper. Using interference alignment along with secrecy precoding, it is shown that each user can achieve non-zero secure degrees of freedom (DoF) for both cases. More precisely, the proposed coding scheme achieves K-2/2K-2
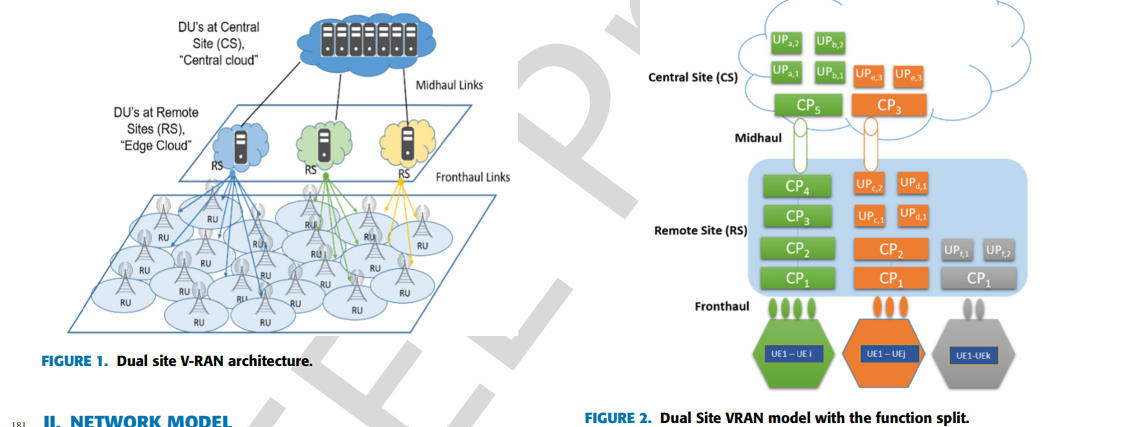
A virtualized radio access network (V-RAN) is considered one of the key research points in the development of 5G and the interception of machine learning algorithms in the Telecom industry. Recent technological advancements in Network Function Virtualization (NFV) and Software Defined Radio (SDR) are the main blocks towards V-RAN that have enabled the virtualization of dual-site processing instead of all BBU processing as in the traditional RAN. As a result, several types of research discussed the trade-off between power and bandwidth consumption in V-RAN. Processing at remote locations
This paper aims to help self-driving cars and autonomous vehicles systems to merge with the road environment safely and ensure the reliability of these systems in real life. Crash avoidance is a complex system that depends on many parameters. The forward-collision warning system is simplified into four main objectives: detecting cars, depth estimation, assigning cars into lanes (lane assign) and tracking technique. The presented work targets the software approach by using YOLO (You Only Look Once), which is a deep learning object detector network to detect cars with an accuracy of up to 93%
In this paper, we propose a Reinforcement Learning-based MAC layer protocol for cognitive radio networks, based on exploiting the feedback of the Primary User (PU). Our proposed model relies on two pillars, namely an infinite-state Partially Observable Markov Decision Process (POMDP) to model the system dynamics besides a queuing-theoretic model for the PU queue, where the states represent whether a packet is delivered or not from the PU's queue and the PU channel state. Based on the stability constraint for the primary user queue, the quality of service (QoS) for the PU is guaranteed. Towards
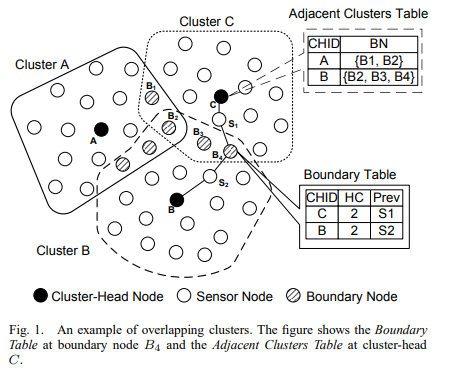
Clustering is a standard approach for achieving efficient and scalable performance in wireless sensor networks. Traditionally, clustering algorithms aim at generating a number of disjoint clusters that satisfy some criteria. In this paper, we formulate a novel clustering problem that aims at generating overlapping multihop clusters. Overlapping clusters are useful in many sensor network applications, including intercluster routing, node localization, and time synchronization protocols. We also propose a randomized, distributed multihop clustering algorithm (KOCA) for solving the overlapping
In recent years, many probability models proposed to calculate the collision probability for each vehicle and those models used in collision avoidance algorithms and intersection management algorithms. In this paper, we introduce a method to calculate the collision probability of vehicles at an urban intersection. The proposed model uses the current position, speed, acceleration, and turning direction then each vehicle shares its required information to the roadside unit (RSU) via the Vehicle to Infrastructures (V2I). RSU can predict each vehicle's path in intersections by using the received
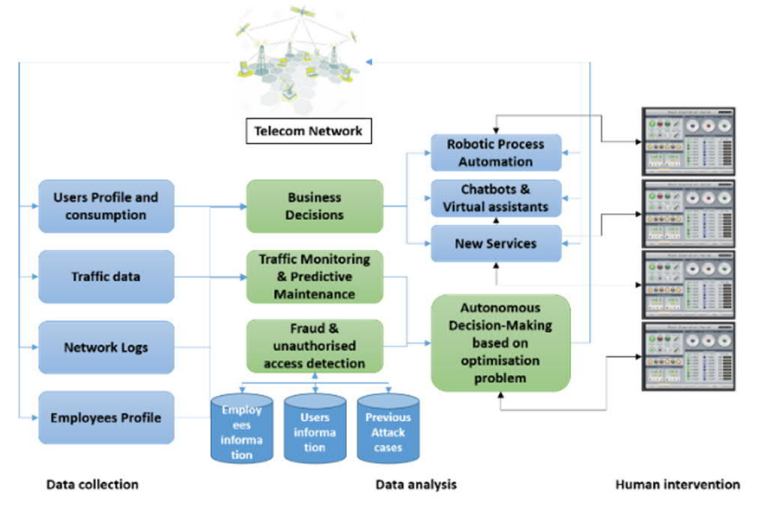
With the development of the 5G and Internet of things (IoT) applications, which lead to an enormous amount of data, the need for efficient data-driven algorithms has become crucial. Security concerns are therefore expected to be raised using state-of-the-art information technology (IT) as data may be vulnerable to remote attacks. As a result, this paper provides a high-level overview of machine-learning use-cases for data-driven, maintaining security, or easing telecommunications operating processes. It emphasizes the importance of analyzing the role of machine learning in the