
Artificial Intelligence

Modeling and Control of a Novel Design of Series Elastic Actuator for Upper Limb Rehabilitation
The field of rehabilitation robotics for upper limb assistance has grown rapidly in the past few years. Rehabilitation robots have direct contact with human joints, which presents a serious safety concern. In this paper, a novel design for a series elastic actuator (SEA) is presented for upper limb rehabilitation of sensorimotor dysfunctions. The proposed SEA ensures safety and robust torque control under various disturbances. The proposed SEA is modeled and simulated using MATLAB Simulink to obtain Input/Output driven data. For the proposed system, two modeling approaches, ARMAX and NN, are
A review of upper limb robot assisted therapy techniques and virtual reality applications
Impairments in the sensorimotor system negatively impact the ability of individuals to perform daily activities autonomously. Upper limb rehabilitation for stroke survivors and cerebral palsy (CP) children is essential to enhance independence and quality of life. Robot assisted therapy has been a bright solution in the last two decades to promote the recovery process for neurological disorders patients. Nevertheless, defining the optimum intervention of robot assisted therapy (RAT) in different cases is not clear yet. With this aim, the presented study reviewed the current literature on RAT
Deep Learning Based Kinematic Modeling of 3-RRR Parallel Manipulator
This paper presents a novel low cost design for a 3-RRR Planar Parallel Manipulator (PPM). These manipulators proved their superiority over serial manipulators due to their speed, precision and smaller work space where the work space area is accounted for in the design to ensure that the robot is performing its task in a smooth and simple way without getting into any singularity points. The challenge with PPM is to obtain the kinematic constraint equations of the manipulator due to their complex non-linear behavior. Screw theory is a new approach that is used to compute the direct and inverse
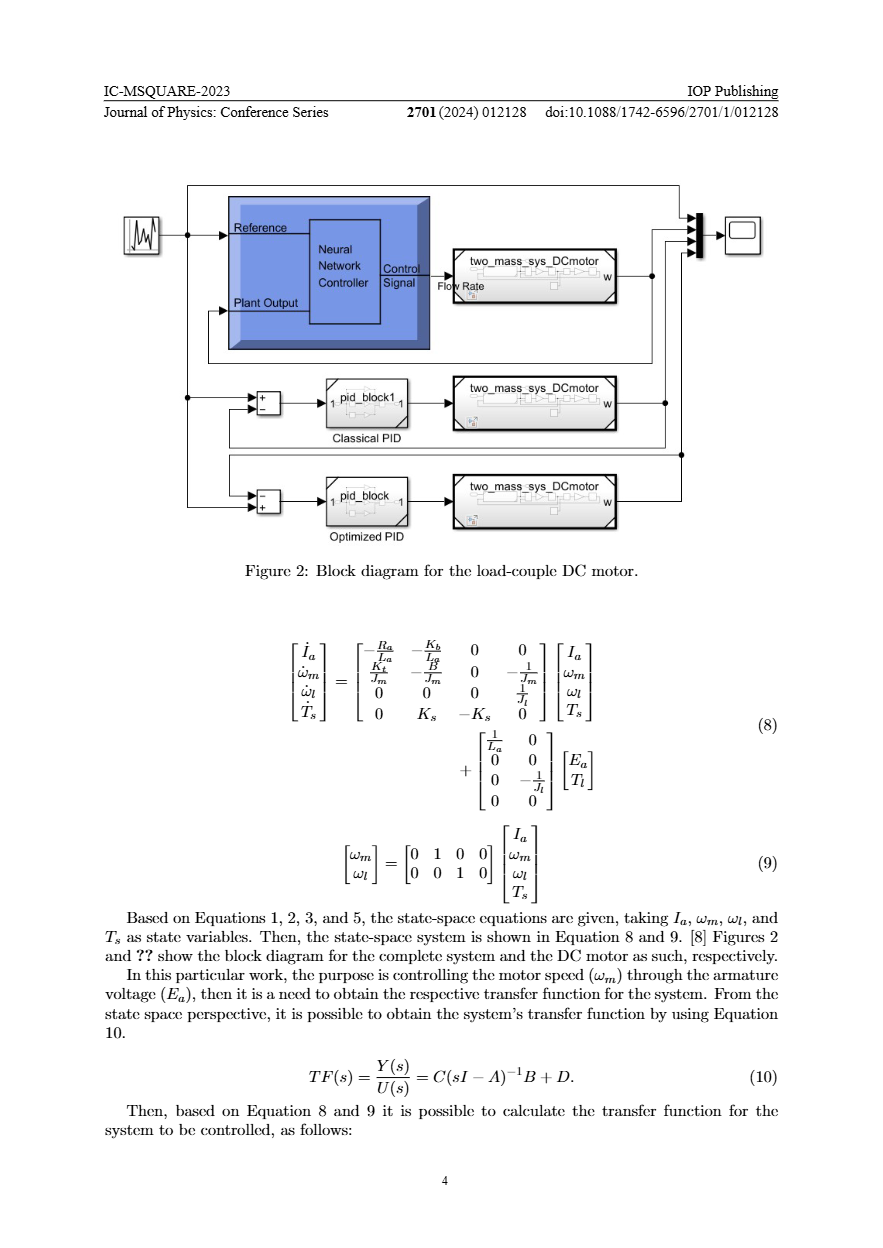
Optimized PID and NN-based Speed Control of a Load-coupled DC Motor
In this work, three control strategies are presented, compared, and discussed, applied on a load-coupled DC motor. The purpose is to control in an optimal way the motor speed in terms of the armature voltage. Two strategies are based on PID control, working on the classical PID controller and the optimized one by using particle swarm optimization (PSO) to tune the PID controller parameters. The other strategy is based on neural networks (NNs) where two NNs are built to model and control the system. Based on the results, all the strategies reach excellent performances, however, in terms of
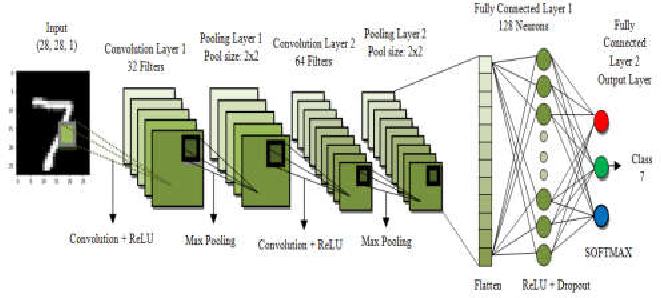
KNN and the CNN for Handwritten Digit Recognition: A comparative study
The automatic identification of handwritten digits by computers or other devices is referred to as "handwritten digit recognition technology,"and it has a wider range of potential applications in the processing of bank bills, financial statements, and postage stamps. This study examines the methods KNN, and CNN, and their use in handwritten digit recognition using samples from the MNIST handwritten digit database. In order to achieve the best results for each method, this work rewrites KNN with Python and CNN with Tensorflow throughout the training phase. The benefits and drawbacks of the two
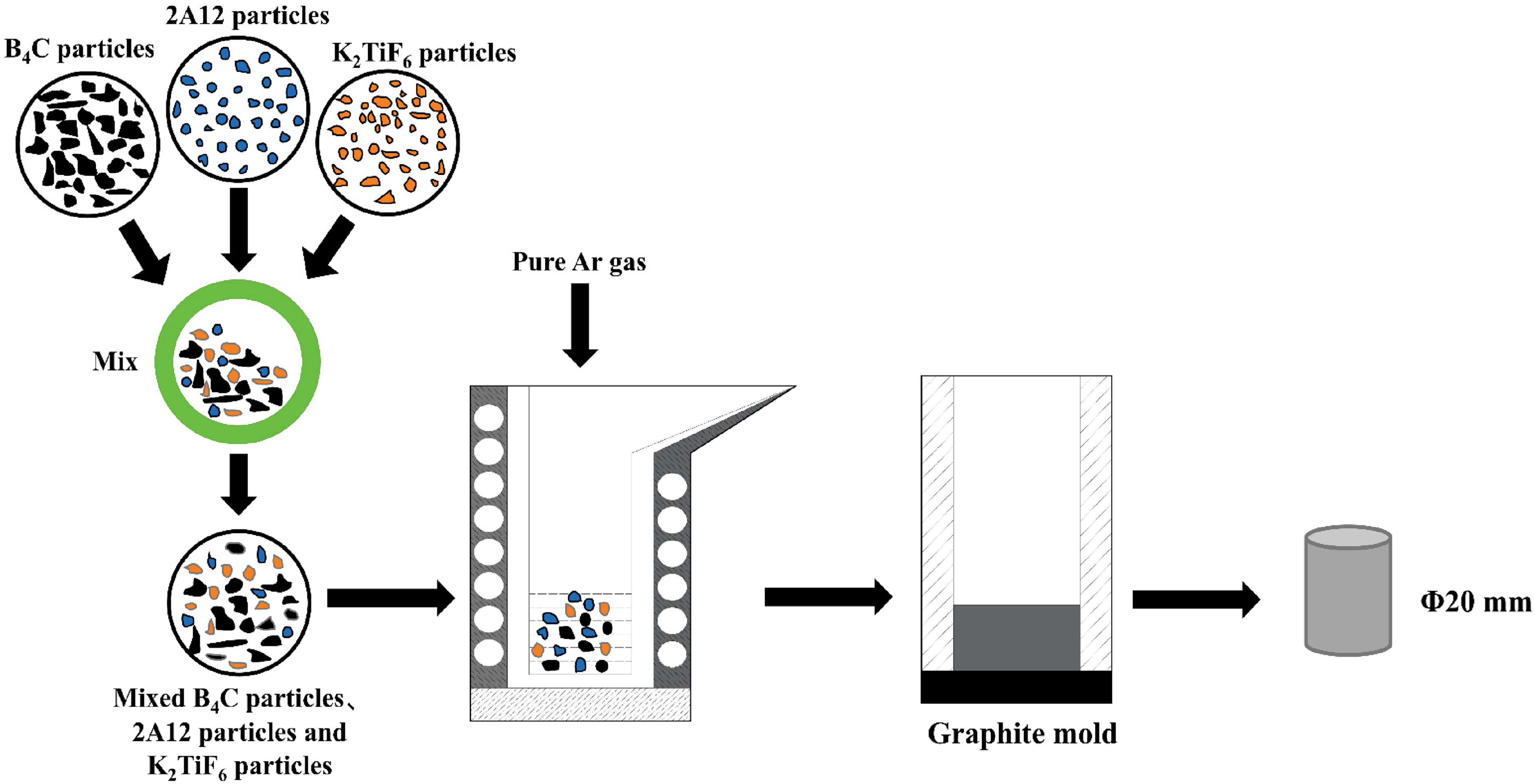
Study on the microstructure, mechanical and corrosion behaviors of 2A12 Al matrix composites containing B4C and 50% K2TiF6 flux
This study presents an innovative exploration into the development and characterization of boron carbide (B4C) reinforced aluminum (Al) metal matrix composites (AMMCs), specifically focusing on the 2A12 Al alloy. Utilizing a cutting-edge vacuum induction melting process, the research investigates the effects of varying B4C particle concentrations in conjunction with 50% K2TiF6 flux additions. This novel approach aims to enhance the microstructural integrity, mechanical properties, and corrosion resistance of the AMMCs. The research unveils a significant improvement in microhardness and tensile
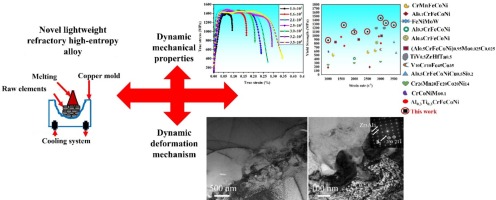
Influence of high-strain-rate compression and subsequent heat treatment on (TiNbZr)89(AlTa)11 refractory high-entropy alloys: Dynamic-mechanical behavior and microstructural changes
This study explored the dynamic-mechanical behavior of a novel low-density (TiNbZr)89(AlTa)11 refractory high-entropy alloy (RHEA) across strain rates ranging from 1.0 × 103 to 3.5 × 103 s−1. A significant increase in the yield and ultimate compressive strengths with rising strain rates up to 3.0 × 103 s−1 was observed and attributed to enhanced dislocation activities and stress-induced microstructural transformations. The formation of the B2 phase and Zr5Al3 precipitates was found to be crucial in bolstering the alloy strength at high strain rates. Beyond strain rates of 3.0 × 103 s−1, a
Fractional-order fuzzy sliding mode control of uncertain nonlinear MIMO systems using fractional-order reinforcement learning
This paper introduces a novel approach aimed at enhancing the control performance of a specific class of unknown multiple-input and multiple-output nonlinear systems. The proposed method involves the utilization of a fractional-order fuzzy sliding mode controller, which is implemented through online fractional-order reinforcement learning (FOFSMC-FRL). First, the proposed approach leverages two Takagi–Sugeno–Kang (TSK) fuzzy neural network actors. These actors approximate both the equivalent and switch control parts of the sliding mode control. Additionally, a critic TSK fuzzy neural network

Constitutive equation for compressible non-isothermal polymeric fluids: A microstructural approach
This contribution presents a microstructural approach to relax both the incompressibility and the isothermality constraints in the elastic-dumbbell model. This results in a compressible version for the Smoluchowski equation which is used to derive a non-isothermal compressible evolution equation for the conformation tensor for a general spring force. The devised general equation is used to derive constitutive equations depending on spring force model whether linear or non-linear. A moving-grid numerical scheme is developed to test the ability of the proposed model in capturing experimental
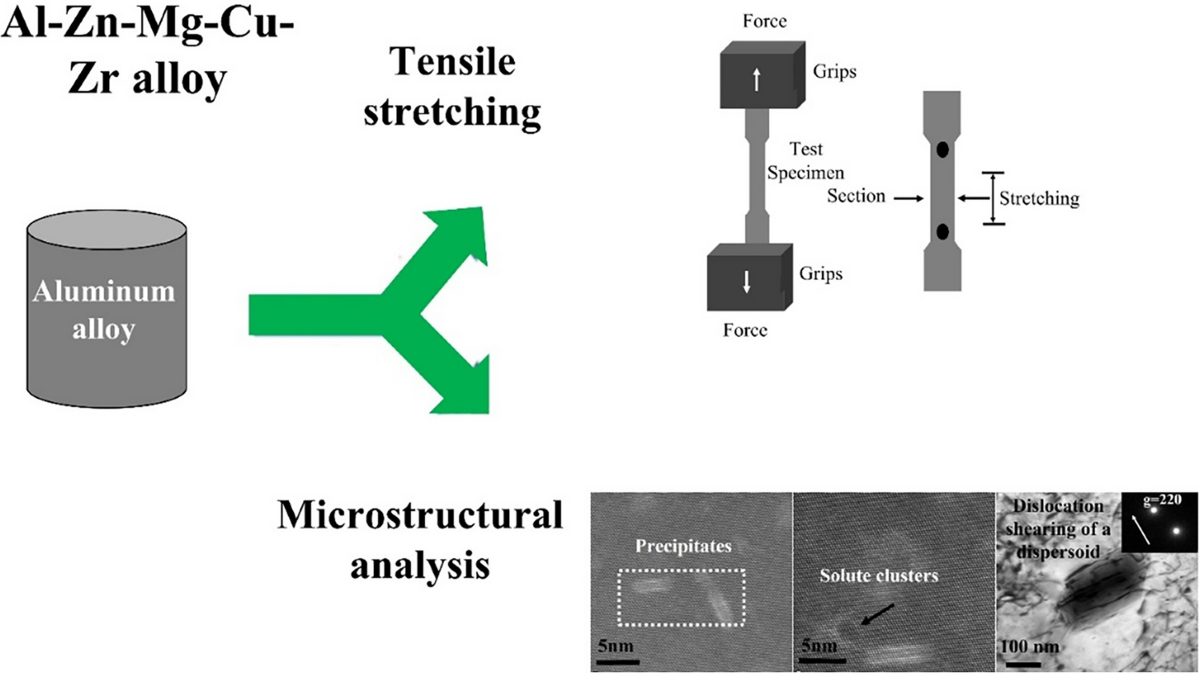
Investigating the Microstructural Impact of Tensile Stretching on Al-Zn-Mg-Cu Alloys: Dislocation-Precipitate Interactions
The study investigates the effects of tensile stretching on the microstructural evolution and mechanical properties of a high Zn-content Al-Zn-Mg-Cu alloy, emphasizing dislocation dynamics and precipitate behavior. The alloy, with a composition of Al-9.01 Zn-2.45 Cu-2.25 Mg-0.13 Zr (wt.%), prepared through casting subjected to peak-aged (T6) at 743 K for 1 h followed by 393 K for 24 h. Tensile stretching at room temperature (~ 298 K) and a strain rate of 1.0 × 10−3 s−1 resulted in a 20% increase in yield strength from to 300 to ~ 360 MPa, with ductility decreasing to ~ 1% elongation to