
Innovation, Entrepreneurship and Competitiveness
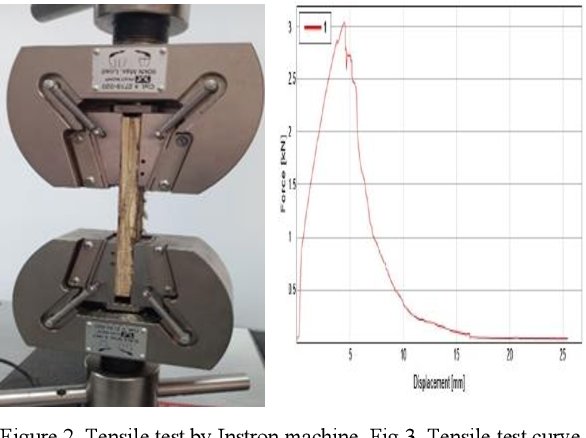
Utilization cotton stalks as a raw material for wooden products
Wood is one of the most used materials in the construction industry. However, the traditional source of wood, which is forestry, has some negative impacts on the environment. Hence, there have been increased efforts to find alternative sources of wood to minimize environmental degradation. Cotton stalks have been identified as a potential raw material for this industry, and research has shown that this material has good potential to replace wood. Furthermore, the disposal of cotton stalks is a significant environmental problem in many regions. This study discusses utilizing cotton stalks for
Investigation of a novel drying technique in tableware production process
The primary by-product of the sugarcane industry is sugarcane bagasse, which is considered a raw material for molded tableware production process. Studies proved that this industry is energy and water intensive. Attempts have been conducted to produce biodegradable bagasse plates utilizing a novel drying technique for the bagasse pulp using mechanical rollers for dehydration and cold drying instead of conventional vacuum drying. It was found that the new drying mechanism reduces the energy consumed by 32% and water consumption by 90% compared to the traditional molded tableware manufacturing
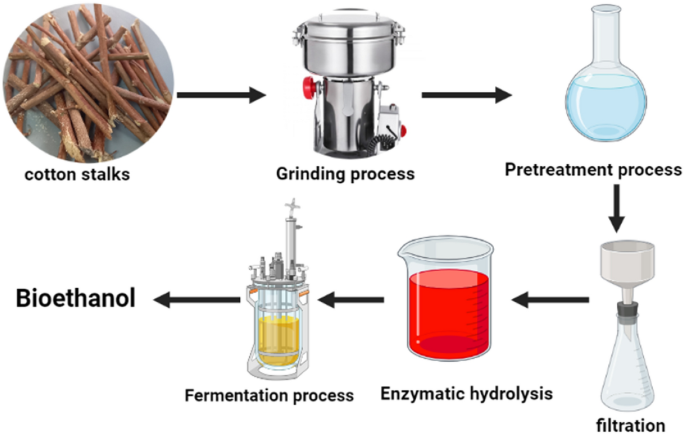
A comparative cradle-to-gate life cycle assessment of three cotton stalk waste sustainable applications
This paper presents a novel approach to utilizing agricultural waste. It compares three different applications for cotton stalks: fabrication of wood composites, bioethanol production, and biogas cradle-to-gate Life cycle assessment production processes. Cotton cultivation generates a lot of debris, mostly cotton stalks, which are incinerated or landfilled, Sustainable resource management is critical for maintaining the ecosystem, and economic stability, and promoting social fairness since it ensures the long-term availability of resources while minimizing environmental damage. The

Lab to Industry
In terms of environmental and socio-economic benefits, the utilization of agro-fiber wastes in pulp-based product manufacturing is advantageous. Non-wood plant pulp production has shattered, and numerous non-wood fiber resources are being commercially used to make chemical pulp and paper in China, India, Latin America, Africa, the Middle East, and Turkey. Agricultural wastes, including rice and wheat straws, sorghum stalks, and annual plants like hemp and jute, are being utilized as raw materials for pulp and paper manufacture. In addition, various research has been carried out to introduce

Technological innovation in ergonomics & safety in automotive industries in Egypt
The increase in the complexity and the inspiring environment between the automotive organizations in Egypt forced the quality experts and management team to propose various tools related to Quality Management Systems but there is a slight apprehension to the ergonomic concepts in these industries. This study investigates the complications related to the ergonomics in the assembly line of an automotive company in Egypt. The assembly line is divided into several stations including trim line, chassis line and a glass handling station. The focus of this study is the ergonomics of the glass
Analysis of musculoskeletal disorders in personal care industries in Egypt
The increase in the complexity of operations in personal care industries in Egypt forced the ergonomic experts to propose various tools to analyze the human errors and eliminate the most dangerous operations according to the international standards of safety and ergonomics. International references such as the Rapid Upper Limb Assessment (RULA) and Rapid Entire Body Assessment (REBA) analysis are performed to investigate different postures as well as Computer Aided Three-Dimensional Interactive Application (CATIA) and Maynard Operation Sequence Technique (MOST softwares). A modified scissor
Towards a circular economy: valorization of banana peels by developing bio-composites thermal insulators
The building construction materials are responsible for a large amount of energy and natural resource consumption. In light of the current challenges of resource scarcity and global climate change, the circular economy (CE) is a promising strategy to mitigate pressure on the environment, improve supplying of raw materials, and increase new market and employment opportunities. Developing eco-friendly thermal insulation materials based on agro-waste is a new waste management trend to achieve the sustainability of the resource and energy consumption in the construction sectors. In this work

NEW Hybrid ZIF-8/NC-PU and NC-PU Gel Composites for the Effective Removal of Cationic and Anionic Dye from Aqueous Solution: Process Optimization
New hybrid metal organic framework based polymer nanocomposite (ZIF-8/NC-PU) and interpenetrating polymer gel nanocomposites (NC-PU) were prepared for the adsorption of cationic (Rh-B) and anionic (IC) dyes from aqueous solution. The characterisation of the ZIF-8 based composites and gel composites is carried out using FT-IR and SEM analysis to investigate the chemical composition and morphology of the sample. Moringa oleifera seed pod based nanocellulose (5 wt%) is used as the filler in NC-PU gel composites and ZIF-8/NC-PU MOF composites. The optimal level of the most significant identified

Modeling circular supply chains as an approach for waste management: A systematic review and a conceptual framework
All world countries are suffering from repercussions of the global climate change problems and there is an urgent need to mitigate their negative impacts. Improper waste management methods contribute directly to climate change where common waste treatment methods are basically relying on incineration or landfilling. Nowadays, incorporating the circular economy perspective into the business model demonstrates the ability of creating value from wastes and reducing the residuals by adopting the circular supply chains management (CSCM) as a promising alternative to linear supply chains. Studying

A hybrid bat algorithm to solve the capacitated vehicle routing problem
The vehicle routing problem (VRP) is one of the important problems that has been examined extensively over the past decades. The problem holds a central position within the fields of transportation logistics and supply chain management. Due to the NP-hard nature of the problem, many researchers have developed several heuristics and metaheuristics to solve the problem. This research proposes a hybrid bat algorithm to solve the VRP. The algorithm employs the Bat algorithm hybridized with a modified kmeans algorithm. The proposed solution technique adopts the methodology of cluster first route