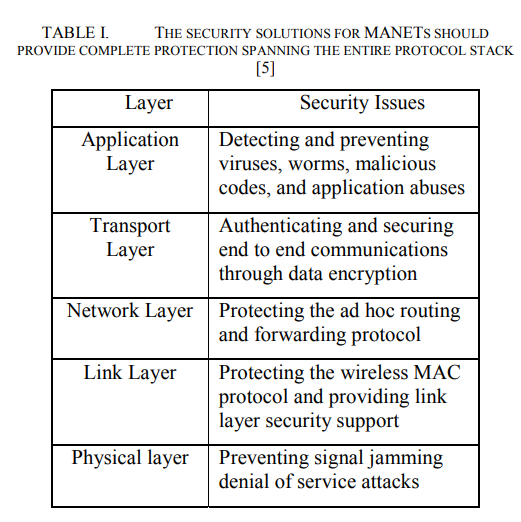
Security in Ad hoc networks: From vulnerability to risk management
Mobile Ad hoc Networks (MANETs) have lots of applications. Due to the features of open medium, absence of infrastructure, dynamic changing network topology, cooperative algorithms, lack of centralized monitoring and management point, resource constraints and lack of a clear line of defense, these networks are vulnerable to attacks. A vital problem that must be solved in order to realize these applications is that concerning the security aspects of such networks. Solving these problems combined with the widespread availability of devices such as PDAs, laptops, small fixtures on buildings and cellular phones will ensure that ad hoc networks will become an indispensable part of our life. In this paper, we discuss the reasons of vulnerability as well as active and passive attacks on such networks. We present the security measures used to secure ad hoc networks such as authentication, threshold cryptography, trust and reputation, and present a risk management scheme. Concluding remarks are presented at the end of this paper, while mentioning the different open research areas and challenges in the discussed security measures. © 2009 IEEE.